What is a Microvisor?
Time to read: 3 minutes
The Internet of Things (see also What is IoT) is a rapidly growing field that connects physical devices, such as appliances, vehicles, and industrial equipment, to the internet to enable communication and data exchange. However, achieving reliable and secure connectivity for these devices is still a significant challenge.
One of the main obstacles is the lack of robust firmware development and maintenance tools, specifically for low-power microcontrollers (MCUs), which are increasingly used in IoT devices. Unlike software development, firmware development for deployed devices lacks true line-by-line remote debugging capabilities and other agile development practices, making it difficult to iterate fast and often, as is so common in cloud software development.
New approaches are required to address these challenges, one of which is the use of a microvisor, a hypervisor for MCUs.
What is a microvisor?
A microvisor is an IoT approach using hypervisors for microcontrollers, which enables reliable and secure remote operations, such as failsafe over-the-air firmware updates, on Internet-connected devices.
Architecturally, a microvisor makes use of hardware separation within a microcontroller – such as the STM32U585 from ST – to divide it into two sections at boot time, e.g. by leveraging Arm® TrustZone®.
TrustZone provides a cost-effective methodology to isolate security critical components in a system, by hardware-separating a rich operating system from a much smaller, secure operating system. Peripherals are assigned to either the microvisor zone or the customer application zone at boot time and the two sections run code independently of each other. This allows for complete security, and to be completely agnostic in terms of which operating system or programming language the application zone runs.
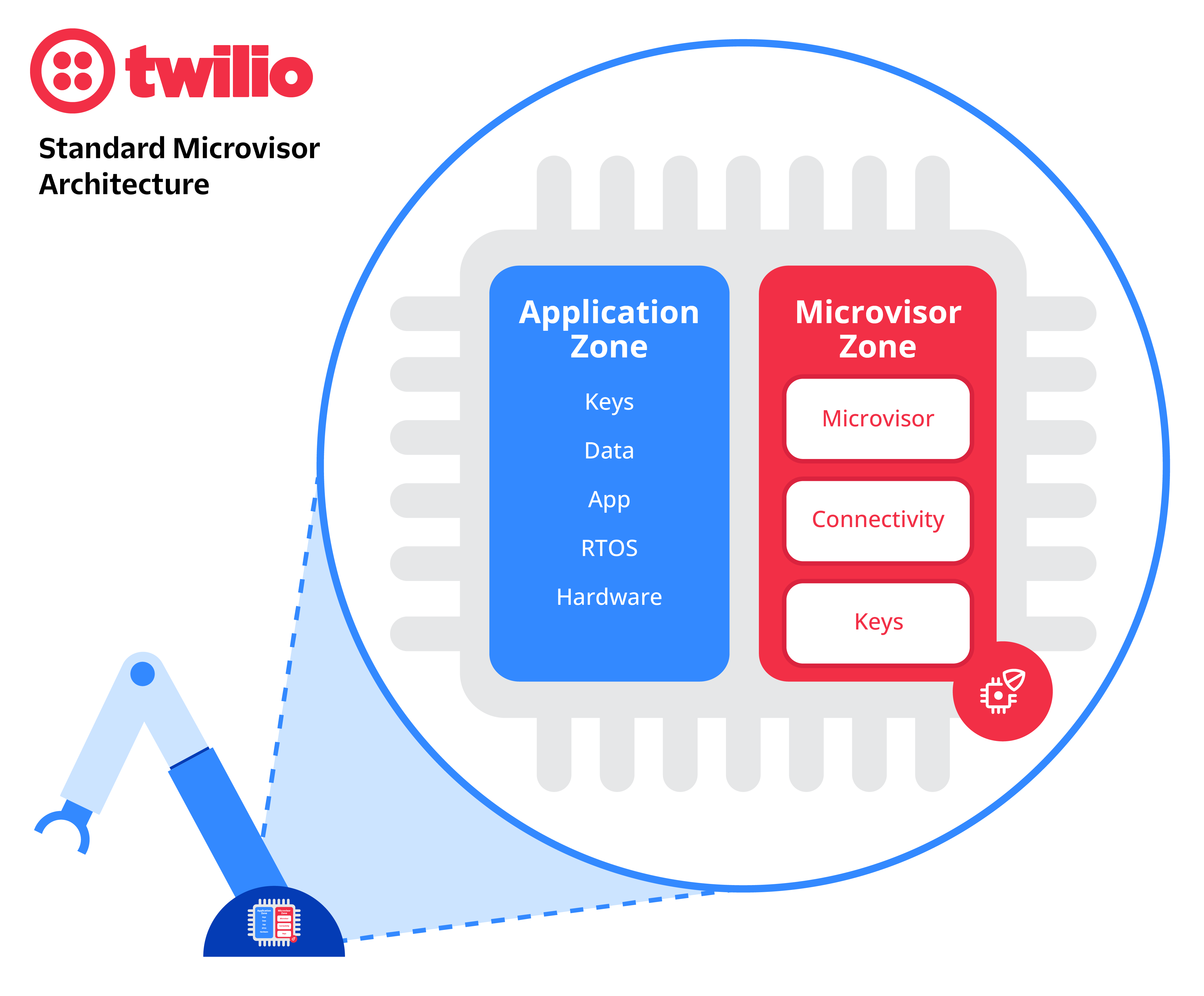
The microvisor element runs ‘alongside’ the application code on the same MCU but with different security privileges, thanks to the TrustZone split. The microvisor wraps a layer of security and connectivity around the application code space.
A microvisor-based IoT platform does not impose any limitations on which OS or language must be used, something that many other IoT platforms that are not microvisor-based do. It adapts to any approach in embedded development, whether it is
- a custom bare-metal approach
- built on top of an “off-the-shelf” realtime operating system, e.g., Amazon FreeRTOS or Microsoft Azure RTOS (fka ThreadX)
- using whatever programming language you choose
One of the key capabilities that a microvisor-based architecture allows is over-the-air (OTA) firmware updates, but in a way that does away with the need to keep 2 versions of the firmware on the device in case of failures.
About the Twilio Microvisor
Twilio Microvisor is a fully managed implementation of the microvisor architecture. It offers functionality that goes beyond what a barebones microvisor would provide.
- Managed security: Twilio Microvisor offers security for the complete lifecycle of a connected device, starting with a secure factory provisioning process with Secure Boot. Twilio also ensures constant ongoing improvement and protection for devices without having to invest any additional engineering effort on the side of the customer. Essentially, Twilio offers security as a managed service, which helps companies manage the predictability of ongoing cost.
- True remote debug: Rather than relying on historic troubleshooting through stack traces and log files, Twilio Microvisor allows for true, line-by-line remote debugging on individual devices, to uncover issues that might only occur in the field, but not in the lab.
- Unbrickable over-the-air firmware updates: With a simple API call, developers can push updates to cellular or otherwise connected devices remotely. The architectural split of the microvisor approach guarantees that whatever happens to the application itself, the microvisor will ensure that your device(s) will be able to connect and upgrade the application and file system.
The following (silent) video shows how firmware updates and secure remote debugging looks like in action:
Interested in receiving a development board? Sign up here to join our Beta Program, or head over to our documentation for more information. If you would like to dive deeper into the architecture and the thinking behind it, please explore our whitepaper: Twilio Microvisor—Architecture and Design Considerations for Modern IoT Infrastructure
Related Posts
Related Resources
Twilio Docs
From APIs to SDKs to sample apps
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars
Learn from customer engagement experts to improve your own communication.
Ahoy
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.


