Secure Playback of Recordings from Custom Storage
Public beta
Flex Insights (also known as Historical Reporting) is currently available as a public beta release and the information contained in the Flex Insights documentation is subject to change. This means that some features are not yet implemented and others may be changed before the product is declared as generally available. Public beta products are not covered by a Twilio SLA.
Any reference to "Historical Reporting", "Flex Insights API", "Flex Insights Historical Reporting", or "Flex Insights Historical Reporting API" in the Flex Insights documentation refers to Flex Insights.
You can manage user access to call recordings from Flex Insights on your own terms.
If you store call recordings outside of Twilio, you can use this feature to:
- Create a custom authorization of users
- Log user access to individual recordings
- Decrypt Twilio recordings encrypted by your public key (using your private key)
You can use the url_provider attribute when attaching Custom Media. Flex Insights Player sends a request to the URL to ask for the actual link to the recording. Your service at the provided URL can then perform any authorization operations before providing the link. The link itself has to carry any authorization information, such as a time-limited token, single-use token, etc.
You can point the Player to a standard service such as AWS S3. Or, you can point the Player to a custom service that may perform additional operations before streaming the actual audio. For example, decryption of the audio.
Info
Waveform (blue, green, red, and orange bars) is not available in the Conversation Screen for recordings that are stored externally. This means users will not see when an agent or customer is speaking while playing back recordings.
The value of the url_provider attribute is a link to your API service. The service has to validate the Flex JWE token and provide back the link to the recording. The link has to contain an identifier of the recording that your service understands so it can point the Player to the right recording.
Example TaskRouter attributes structure for task-level voice link:
1{2"task_attributes": {3"conversations": {4"media": [5{6"type": "VoiceRecording",7"url_provider": "https://your_domain/?recording=RExxxxxxxxxxxxxxxxx"8}9]10}11}12}
Info
You can also use the url_provider attribute on the reservation level as
described in Custom Media attached to
Conversations.
You can have different media attached to individual segments of a
conversation.
When you open a recording from Flex Insights, the Player calls the API URL you provided as the value of the url_provider attribute. The Player adds the Flex JWE token in the authorization header. The token is Base64 encoded.
Example request:
1GET /sec_rec?recording_sid=RExxxxxxxxxxxxxxxxxxxxxxx HTTP/1.12Host: your_domain3Connection: keep-alive4Pragma: no-cache5Cache-Control: no-cache6Authorization: Basic dG9rZW46ZXlKNmFYQWlPaUpFUlVZaUxDSnJhV1FpT2lKVFFWTmZVek1==7User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.113 Safari/537.368Accept: */*9Origin: https://flex.twilio.com10Sec-Fetch-Site: cross-site11Sec-Fetch-Mode: cors12Sec-Fetch-Dest: empty13Accept-Encoding: gzip, deflate, br14Accept-Language: en-US,en;q=0.9,cs;q=0.8
To enable playback, your API service has to:
- Validate the Flex JWE token provided by the Player in the authorization header. The validation ensures that the user has a valid Flex session.
- Return the 'media_url' link to the audio file of the recording. The Player uses this link to retrieve the actual recording.
Warning
In the following example, we are using a Twilio function to validate a token. You cannot host your authentication function using Twilio Serverless due to its max header limitations.
The Flex JWE token is sent in the following format:
1Basic ${Buffer.from(`token:${flexJWE}`).toString('base64')}2
The Flex JWE token is Base64 encoded. Your service has to decode the token, then use the Twilio Flex Token Validator in a Twilio Function or in any NodeJS application. Alternatively you can use the Twilio API to validate the token.
Example of token validation in Python:
1header_raw = request.headers.get('Authorization')2header_decoded = b64decode(header_raw.split()[1]).decode()3token = header_decoded.split(':')[1]45url = "https://iam.twilio.com/v1/Accounts/{}/Tokens/validate".6format(TWILIO_ACCOUNT_SID)7headers = {8"content-type": "application/json",9"cache-control": "no-cache",10"Authorization": header_raw11}12payload = {"token": token}13response = requests.post(url, data=json.dumps(payload), headers=headers)
The validated token result contains the following data:
1{2"valid": true,3"code": 0,4"message": null,5"expiration": "2018-09-24T23:22:44.240Z",6"realm_user_id": "user@example.com",7"identity": "user_40example_2Dcom",8"roles":[9"agent"10],11"worker_sid": "WKxxx"12}
Flex Insights Player expects a response containing a direct link to the media in the following format:
1{2"media_url": "https://link/to/recording"3}4
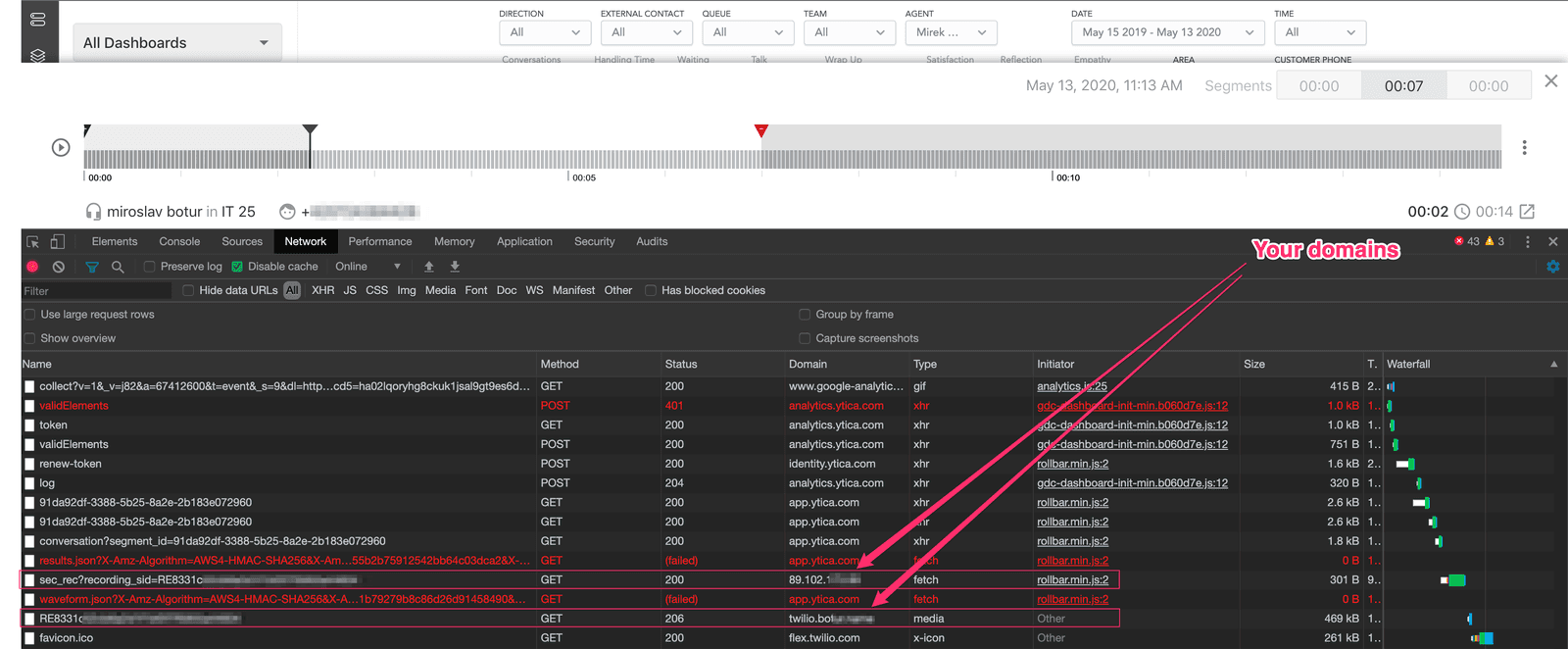
While listening to a recording, open the Developer Tools > Network tab in your browser. Confirm that your browser requested both the 'url_provider' and the 'media_url'.