What is Two Factor Authentication?
Two-factor authentication (commonly abbreviated 2FA ) adds an extra layer of security to your user's account login by requiring two types of authentication. This is usually something your user knows and something they have.
Looking for how to add 2FA to your personal accounts? Check out Authy's 2FA guides for adding 2FA to sites like Gmail, Fortnite, Gemini, and many more.
There are three types of factors:
- Knowledge - something you know like a password
- Possession - something you have like a mobile phone
- Inherence - something you are like a fingerprint
2FA means using any two of these factors. In web authentication, this is commonly something you know and something you have.
Also known as multi-factor authentication (MFA), two-factor authentication is a common authentication best practice to increase account security normally provided by passwords. Passwords became a de facto standard for online authentication because unlike a possession factor, you can't lose a password.
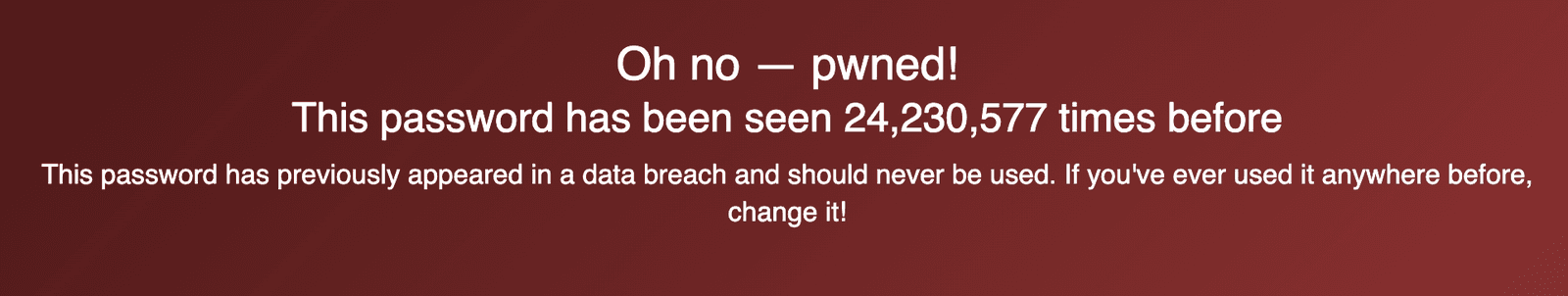
According to the website haveibeenpwned.com, guessable passwords like 123456 are still incredibly common. That password, 123456, has been seen in data breaches over 24 million times . To make matters worse, a 2019 Google study shows that 64% of people admit to reusing passwords across multiple sites. This is a problem because even if someone has a complex password, if they're reusing it for many sites, a data breach at MySpace or Adobe could lead to the user's account getting breached on your company's site through a process known as credential stuffing.
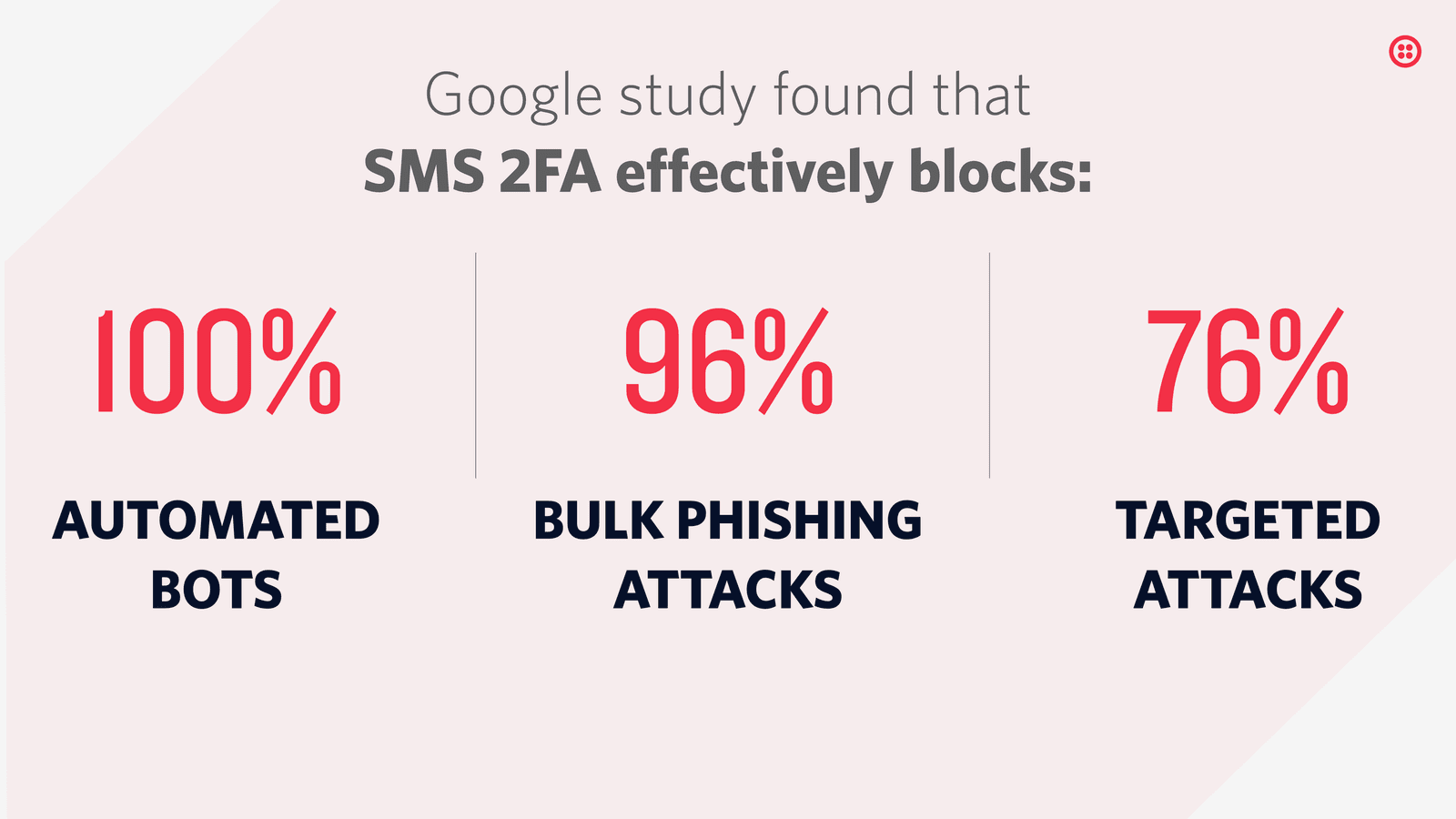
Things like password reuse, poorly encrypted passwords, social engineering, and leaked databases make even a secure password vulnerable. By requiring users to add a second factor to their authentication flow, an account with a compromised password will still be protected. Even targeted attacks are more difficult because the attacker would be required to access to different forms of authentication. A Google study showed that SMS based authentication "can block up to 100% of automated bots, 99% of bulk phishing attacks, and 66% of targeted attacks".
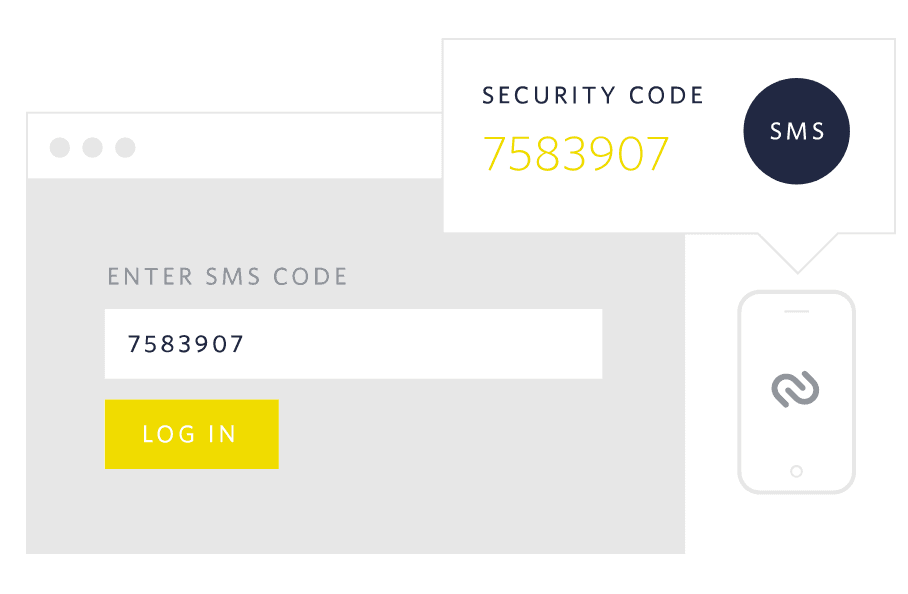
Mobile phone 2FA has become the industry standard, as most people carry their mobile phones at all times. It's a user-friendly flow, and dynamically generated passcodes are safe to use and users can receive special tokens through SMS or a dedicated authenticator app like Twilio's Authy.
SMS authentication has long been a popular choice for securing consumer accounts. It's a familiar channel to deploy and SMS 2FA usage has even grown 9% in the last two years. While the SMS channel has legitimate security concerns, businesses should consider their threat model and offer a spectrum of 2FA options. Offering more secure channels like authenticator apps and push authentication is especially important when you're protecting high value targets like a bank account or email. For more details, check out this blog post on 5 reasons SMS 2FA isn't going away.
Offering 2FA isn't enough: your users also have to turn it on. Check out this blog post with tips for incentivizing 2FA including real world examples from banking and gaming companies.
When you use your credit card and are prompted for your billing zip code, that's 2FA in action. Knowledge factors like your zip code may also be passwords or a personal identification number (PIN). Possession factors like your credit card include (but are not limited to) a physical key, fob, and personal cell phones. Two factor authentication for web applications similarly requires something your user knows (their password) and something they have (their personal mobile phone).
Using two knowledge factors like a password and a PIN is two-step authentication. Using two different factors like a password and a one-time passcode sent to a mobile phone via SMS is two-factor authentication.
Most people add a possession authentication factor in addition to an existing knowledge channel. When a user signs up or logs in to your application 1) a numeric code is sent to their mobile device either via SMS, calls, email, 2) with a push notification or 3) through an authenticator app.
Each channel has different tradeoffs:
- SMS is convenient to use but requires cell service and is less secure.
- An authenticator app (TOTP) provides a constantly rotating set of codes your users can use whenever needed, and does not require a cellular or internet connection.
- Push authentication provides additional context about the authentication event, and has predictable pricing for the business, but does require a specific app download.
Only after the user enters the correct numeric code in your application's login flow are they authenticated.
There are a wide variety of ways to add two-factor authentication to your application. By using the Twilio Verify API, implementation is simplified and can boil down to just a few lines of code.
1// Download the helper library from https://www.twilio.com/docs/node/install2const twilio = require("twilio"); // Or, for ESM: import twilio from "twilio";34// Find your Account SID and Auth Token at twilio.com/console5// and set the environment variables. See http://twil.io/secure6const accountSid = process.env.TWILIO_ACCOUNT_SID;7const authToken = process.env.TWILIO_AUTH_TOKEN;8const client = twilio(accountSid, authToken);910async function createVerification() {11const verification = await client.verify.v212.services("VAaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa")13.verifications.create({14channel: "sms",15to: "+15017122661",16});1718console.log(verification.sid);19}2021createVerification();
Response
1{2"sid": "VEaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",3"service_sid": "VAaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",4"account_sid": "ACaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa",5"to": "+15017122661",6"channel": "sms",7"status": "pending",8"valid": false,9"date_created": "2015-07-30T20:00:00Z",10"date_updated": "2015-07-30T20:00:00Z",11"lookup": {},12"amount": null,13"payee": null,14"send_code_attempts": [15{16"time": "2015-07-30T20:00:00Z",17"channel": "SMS",18"attempt_sid": "VLaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa"19}20],21"sna": null,22"url": "https://verify.twilio.com/v2/Services/VAaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa/Verifications/VEaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa"23}
Ready to add 2FA to your application with Twilio? Here are some resources to get you started:
- Serverless phone verification with Twilio Verify and Twilio Functions
- How to do Phone Verification in iOS Apps with Twilio Verify and Swift
- Verify Push Overview
- Twilio Verify documentation
Let's build something amazing.