Single Sign On
Twilio Editions feature
Single Sign-On is available to all Twilio Editions customers. Learn more about Editions.
Single Sign-On (SSO) enables customers to allow their users to log in to Twilio Console using their corporate Identity Provider (such as Azure Active Directory, Okta, OneLogin etc) credentials.
SSO provides security and compliance benefits such as -
- Using SSO, Twilio Customers can have a single source for authenticating their users (through the IdP). They can also manage security and compliance policies such as password policies and mandating two-factor authentication at a single place.
- Similarly when users leave their organization, they just have to remove the user from one place.
SSO for Twilio Console supports SAML (Security Assertion Markup Language) 2.0 standard. Once SSO is configured, Twilio acts as a Service Provider (SP) and allows users to log in either via IdP-initiated flows or SP-initiated flows.
- To allow a user to log in by SSO, Twilio needs that user to be created first. Twilio doesn't support Just In-Time (JIT) provisioning.
- Once the user is created, Twilio requires the user's email address to be the unique identifier (NameID as per SAML terminology) i.e. Twilio will expect the NameID value in SAML assertion to be the user's email address.
- When SSO is enforced, a user will only be able to log in by SSO. They can't log in using their password.
- Twilio SSO only handles the authentication - what accounts a user has access to and what roles the user has aren't managed by SSO. To manage these, you will need to use the Twilio Console or Admin Center UI.
-
SP-Initiated Login with Proof Key for Code Exchange (PKCE): Twilio SSO supports SP-initiated login (when the user starts their login process by visiting Twilio Console and entering their email address) PKCE to secure user authentication to Twilio. Any IdP-initiated login attempts to the Twilio Console (when a user clicks on the Twilio app, link, or tile from your IdP) are converted to SP-initiated and then proceed to authenticate the user by sending a SAML authentication request to your IDP.
-
SSO Enforcement for Users Based on Domains: Twilio SSO provides the ability to enforce SSO for users based on their email domains. Once you select the domains and enforce SSO on them -
- All existing Managed Users belonging to those domains will get SSO-enforced
- And any new managed users created for these domains will also get SSO enforced. The users will be required to set up their password during the initial log-in but from subsequent log-in sessions, they will be required to log in via SSO.
- Once SSO is enforced for a user, they can't log in using their password. They can log in only using SSO.
-
Enable/Disable SSO for specific Managed Users: If you have any specific user(s) who should be allowed to log in without SSO then you can disable SSO for them using the Admin Center and enable it again as needed.
-
Multiple SSO Profiles: Twilio Console now supports multiple SSO profiles. So if you have more than one IdPs that you want to configure with Twilio, you can do so.
Info
SCIM provisioning and deprovisioning
If you are looking for SCIM-based provisioning and deprovisioning for users from your IDP, we have recently launched a Twilio Organizations Public API with SCIM support in Private Beta. Reach out to your account executive or Twilio Support to get access to this feature.
- Just-In-Time or Automated User Provisioning
- Configuring Roles or other attributes via SSO
Info
Note that the SSO Configuration steps shared below are for the new Self-Service SSO product.
If you are looking to configure SSO with Twilio Console without using the Self-Service Interface in Admin Center (i.e. the legacy SSO for Console), please refer to this page.
Before starting the configuration for Twilio Console SSO, please check and make sure that you have
-
An Identity Provider which supports SAML 2.0
-
Created a Twilio Organization and have access to the Admin Center as an Organization Administrator
-
Purchased a Twilio Edition that includes Single Sign-On and has got Single Sign-On feature enabled for your Twilio Organization
-
Added and Verified the domains to which the users email addresses belong to
-
Added or Imported your existing users (for whom SSO needs to be enabled) as managed users in your Organization
- You can use the Bulk User Import feature to find and import all existing users from your domain
To configure the SSO you have to follow these steps -
- You will need to add Twilio (as SP) metadata into your IdP and then configure your IdP metadata into Twilio.
- Once both sides have the metadata configured, you can test the SSO connection to make sure that everything is in order.
- Once you have tested an SSO connection, then you can select any of your verified domains to enforce SSO for users belonging to those domains.
Follow the configuration guides specific to your Identity Provider (IDP) system from the following links. If this list omits your IDP, use the "Other SAML 2.0" guide.
Info
To enable signed SAML, reach out to your Account Executive. To support signed requests and upload the certificate that the Twilio team shared with you, you need to update your IDP settings.
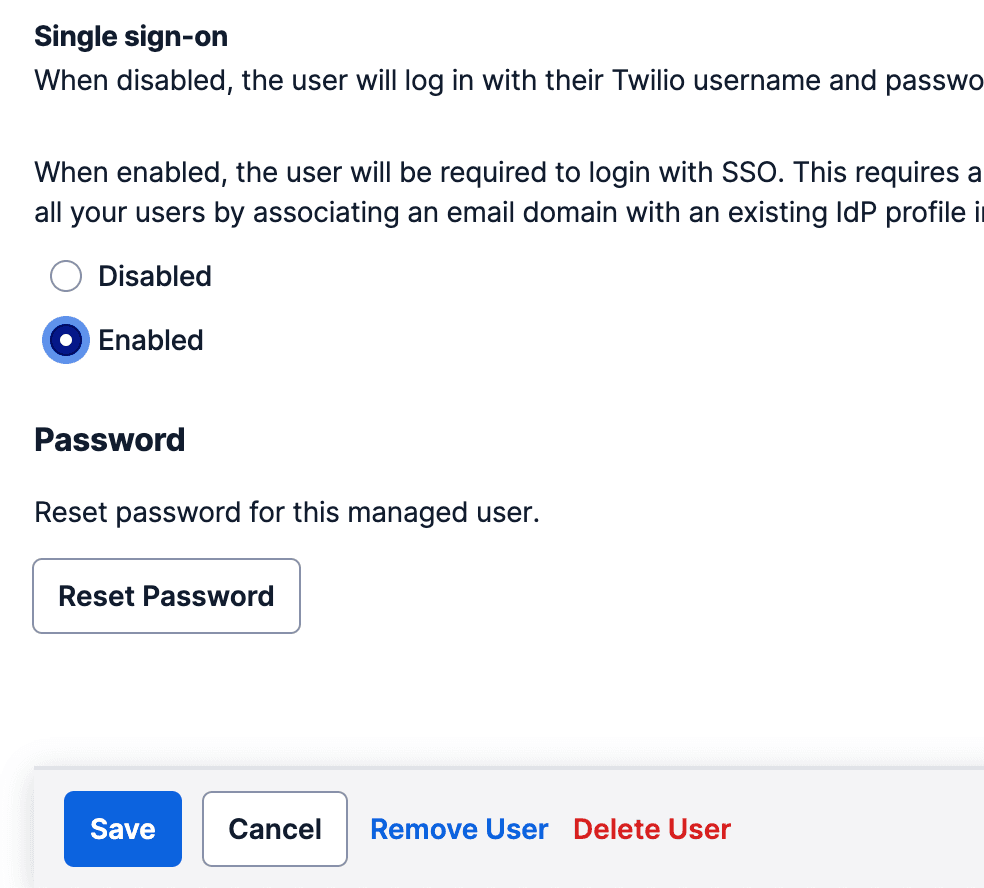
Note: You will need to first set up an SSO profile before you can enable/disable SSO on specific managed users. See Configuring SSO for Twilio Console if you have not already configured an SSO profile.
-
Go to the Admin Center
-
Click on "Users"
-
Click on the name of the user for which you wish to enable or disable SSO
-
Select "Enabled" or "Disabled" for the user
-
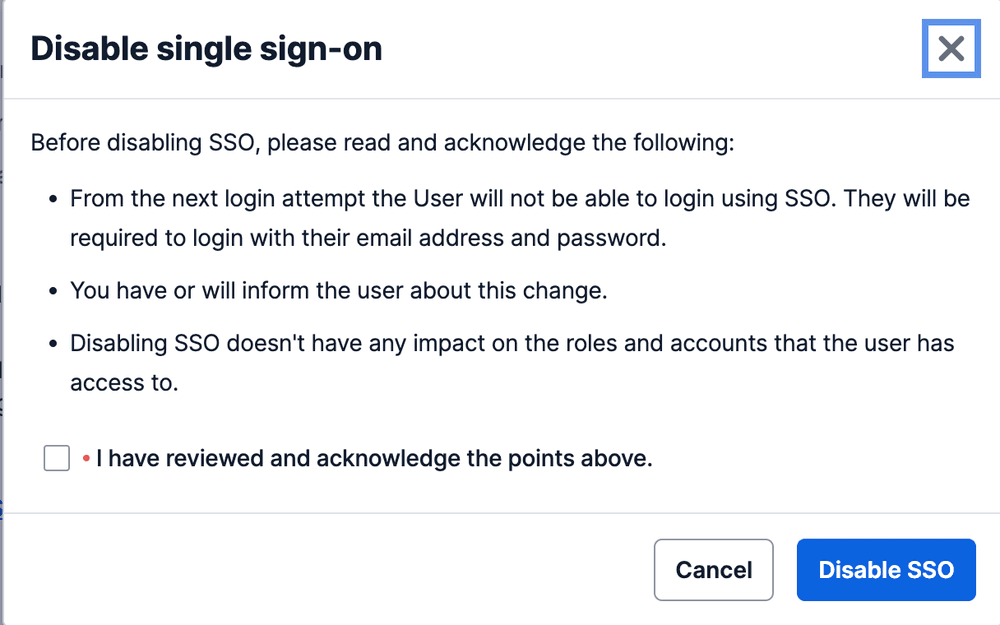
Acknowledge the pop-up prompt and confirm you wish to enable/disable SSO
-
Click "Save"