3 ways to implement PSD2's strong customer authentication (SCA) requirement
Time to read: 2 minutes

The European Payment Services Directive (PSD2) regulation requires Strong Customer Authentication (SCA) when a payer:
- Initiates an electronic payment over €30*
- Accesses their payment account online
- Does any other remote action "which may imply a risk of payment fraud or other abuses"
This applies to:
- Business and/or customers in the European Economic Area
- Online/debit or credit card-not-present transactions
Originally the deadline was September 2019, but that's been extended until 31 December 2020 (the SCA deadline in the UK is now 14 September 2021).
There are three ways to use Twilio to implement SCA for transactions in your application:
- Verify SMS One-Time Passcodes (OTP)
- Push authentication
- Transactional TOTP
This post will give an overview of each method and provide resources to get started.
SCA requirements for card-not-present transactions
SCA requires two-factor authentication using a combination of the following factors. Compliant elements are outlined in detail in the June 2019 EBA opinion document (see Tables 1, 2, and 3).
- Inherence element (i.e. fingerprint scan, voice recognition, keystroke dynamics)
- Possession element (i.e. SMS OTP, hardware token, device-bound application)
- Knowledge element (i.e. password, PIN, memorised swiping path)
Twilio can help with the "something you have" factor by sending one-time passcodes via SMS, push authentication using the Authy App or embedded into your own application, or using the Authy API for transaction specific TOTP. These methods all support dynamic linking, the requirement to include transaction specific information in the authentication including:
- Payee (person or merchant)
- Payment amount
Option 1: Twilio Verify SMS
While SMS is an option for verification, note that financial institutions in some countries like Germany are moving away from SMS.
Make sure Transaction Verification is enabled on your Verify Service in the console.
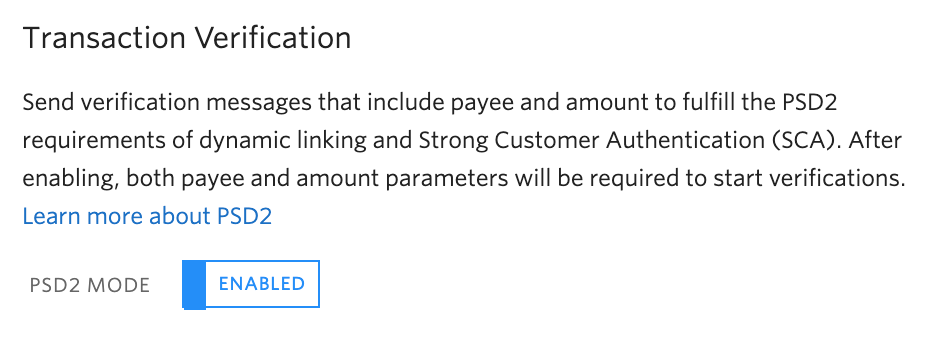
Then you can add dynamic linking information about the transaction when making the API request like so:
You can learn more about using Verify for SCA in the documentation.
Option 2: Push authentication
The new Verify Push SDK allows companies to embed push authentication logic directly into their mobile application, creating an SCA compatible authenticator using something your customers likely already have installed. Learn more about how to get started with Verify Push in the documentation. Since the API for push authentication already supports additional context fields, adding amount and payee works seamlessly.
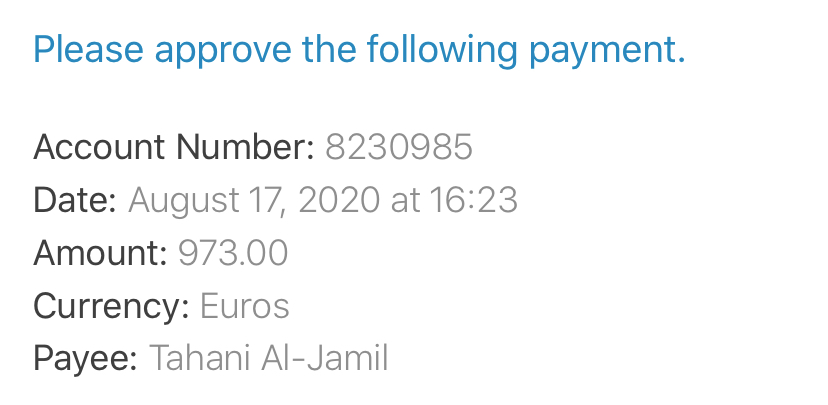
Option 3: Transactional TOTP
Time-based one time passwords (TOTP) is a standardized way to do offline authentication. The "offline" part of that makes it challenging for most applications to satisfy the transaction specific dynamic linking requirements, but Twilio implemented a way to do it with Transactional TOTP.
Here's how it works using the Authy API and Authy App
- Add a user to your Authy application
- Display a secondary QR code from the payment page which the already-registered user will scan from the Authy App
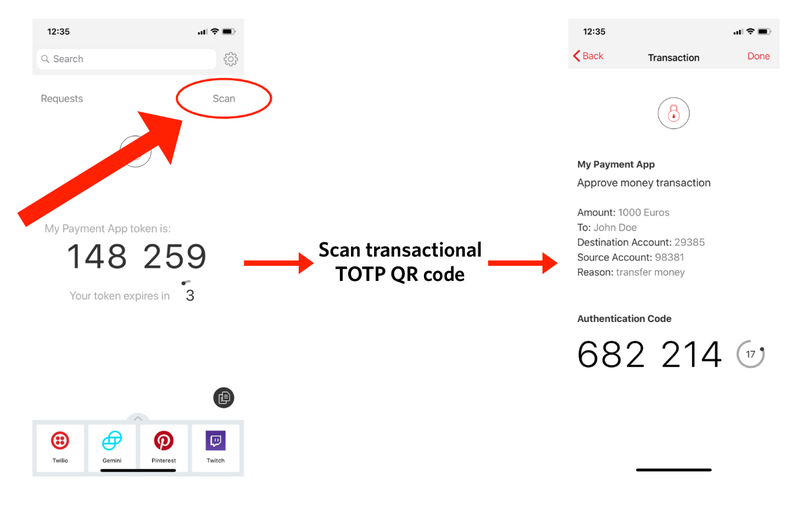
This is a proprietary solution, so it won't work with other authenticator applications like TOTP normally does, but it's a great option for offline authenticator support. Check out this blog post for more details on how to get started.
What's Next?
You have a few months left to implement SCA, longer if you're in the UK. If you have more questions, please reach out - we've helped a lot of companies develop compliant solutions and would love to help you too.
Looking for other ways to add strong authentication to your site or application? We have more ideas and tutorials for 2FA like:
Related Posts
Related Resources
Twilio Docs
From APIs to SDKs to sample apps
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars
Learn from customer engagement experts to improve your own communication.
Ahoy
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.


