Understanding push authentication
Time to read: 4 minutes

Push authentication is one of the most secure and easy to use forms of user authentication. When a company issues an authentication challenge, the user only has to tap allow or deny when they receive the push notification on their phone—much easier than typing in a one-time password (OTP).
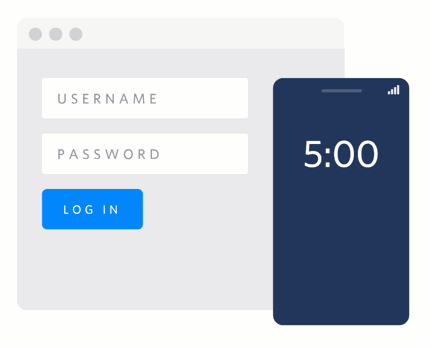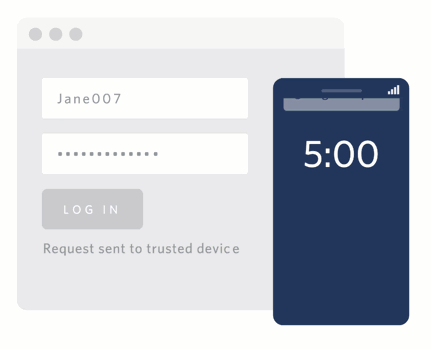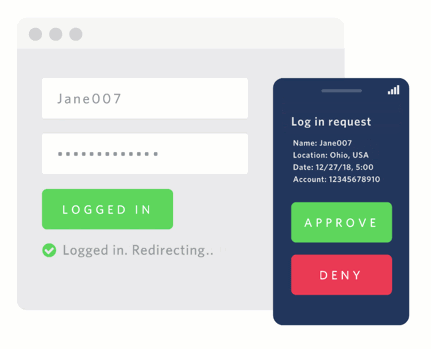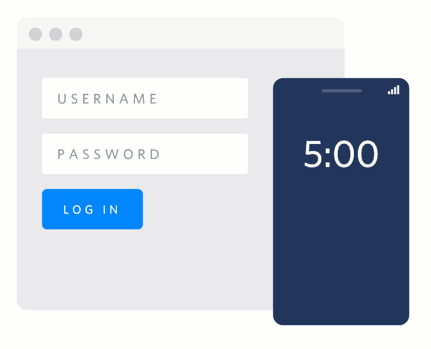
Using push authentication means a company can also add useful context about the authentication event. Think of things like payments: instead of just sending a code, the authentication request can include information about the payment like the amount and recipient. Even better, because it's one of the few forms of authentication that lets the user deny an authentication attempt, companies can take advantage of that information to identify real time phishing attacks or other malicious activity.
Push authentication also uses public key cryptography under the hood to link a single device (like a user's phone) to their identity. That makes it impossible for an attacker to impersonate a user unless they have access to a registered device.
Push authentication doesn't sacrifice user experience for more security
Every authentication method has its tradeoffs. Passwords, while familiar can be guessed or leaked. SMS multi-factor authentication (MFA), while easy to enroll since most people can receive text messages, is vulnerable to SIM swap attacks. Even authenticator apps like Authy and Google Authenticator, while offering more security than SMS, rely on a shared secret key that is portable (often shared via a QR code) and not tied to a single device.
Push authentication is both user friendly and secure. The user only has to tap allow or deny to securely authenticate a login or transaction. Push authentication uses public key cryptography to generate a key pair on the user's device: the private key never leaves the mobile device and the public key is sent to the authenticating company's servers. This provides protection against leaking a shared secret and isn't susceptible to man-in-the-middle attacks.
Push offers a high-enough level of protection that companies are using it for passwordless authentication — replacing passwords altogether instead of even adding a second layer with two-factor authentication.
This method does require additional development, so Twilio released our Verify Push API to help companies quickly and securely deploy push authentication in their mobile apps. Stay tuned for web app support.
How does Verify Push authentication work?
Verify Push handles both the:
- Client SDKS for mobile operating systems (iOS and Android)
- API layer for generating and checking authentication challenges
Together these turn the end user's mobile device into a secure key.
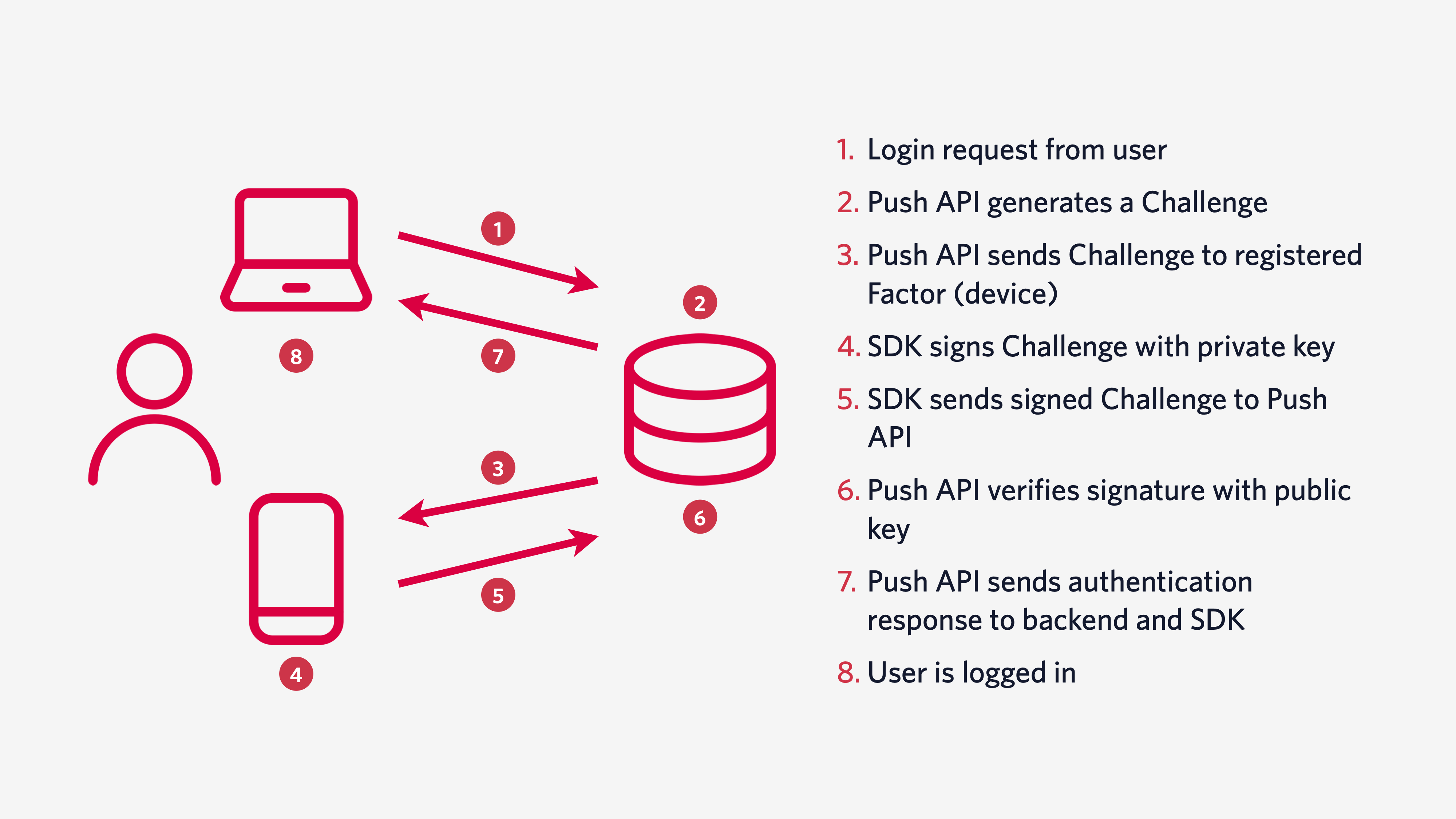
Verify was built to comply with NIST's recommendations for out-of-band verifiers, including managing secrets, expiration and rate limiting so you can focus on the business logic for your application. To learn more about the architecture behind Verify Push, check out the documentation.
When to choose Verify Push authentication over SMS
Consider stronger authentication with push authentication if your business is protecting a lot of value. This could include companies dealing in financial services, healthcare, or e-commerce. I'd love to see consumer telecoms like Verizon or T-Mobile using this type of authentication which could help protect other accounts that use SMS based authentication.
Push authentication is also a good choice if you already have a lot of customers using your mobile application. Because you can embed Verify Push directly into your mobile app, your customers will automatically have an additional layer of security without needing to do much work.
Other reasons to choose push authentication include:
- You want cost predictability globally
- You can take action on "denied" authentications
- You need to meet regulatory requirements like PSD2's strong customer authentication.
When to consider additional authentication channels
For consumer MFA, a channel is only as good as the number of people who opt in to using it. If your company doesn't have a mobile app or has a large number of customers not using your mobile app, you'll definitely want to add other authentication channels like SMS, email, or TOTP in addition to Push.
SMS and email are low friction options for onboarding since they don't require a user to download an additional application. Additional authentication channels are also useful when you want to support fallback options for account recovery if and when a user loses access to their mobile device.
The great thing about Twilio Verify is that it supports multiple channels with one API. You can issue authentication challenges via push or one-time passcodes sent with SMS, voice, or email. Stay tuned for TOTP support and Verify Push in the Authy App.
How to configure Verify Push authentication in your mobile app
There are two ways to get started with Verify Push:
Option 1: Embed the SDK into your existing mobile app
Follow the instructions in our quickstarts to embed the Verify Push SDK in your mobile application.
Option 2: Deploy the Demo App
Download the code to run a demo application to get a sense of how the SDK and API work.
What's next?
As more and more people use smartphones and rely on wifi instead of cellular networks, push authentication is likely to become a standard expectation for authentication. Delight both your most security-conscious users and your security-unaware users with an easy to use, secure authentication option.
Questions about whether Verify Push is the right solution for you? Get in touch and we'll be happy to talk through your authentication needs or learn more about how Transferwise uses Verify Push to seamlessly secure their customers.
Related Posts
Related Resources
Twilio Docs
From APIs to SDKs to sample apps
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars
Learn from customer engagement experts to improve your own communication.
Ahoy
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.


