Best practices to secure inbound calls to your contact center
Time to read: 6 minutes

As companies firm up their website authentication with increased security like two-factor authentication, attackers are flocking to less secure channels like call centers to impersonate their victims and gain access to their accounts. Account takeover (ATO) like this is growing at a staggering rate, up 72% in 2019 according to the 2020 Javelin Identity Fraud Study, "due in large part to technological advancements that have made it easier for criminals to manipulate and socially engineer information". As businesses move more of their operations away from in-person stores in the wake of COVID-19, call center security is more important than ever.
While ATO is possible on your website, over half of financial services companies said call centers were the primary attack channel for ATO. That's because call center agents are fallible to social engineering, a form of hacking that uses psychological manipulation to bypass security measures guarded by humans.
Not convinced? Watch Rachel Tobac, an accomplished ethical social engineer and CEO of SocialProof Security, hack a CNN reporter last year by calling contact centers for furniture stores, hotels, and airlines:
As Rachel points out, there are things you can do to protect yourself as a consumer, but "ultimately, it is the company's responsibility to keep their customers' data safe and updating their authentication protocols over the phone is a really good way to start."
Here are our recommendations for updating your authentication protocols for inbound calls to your contact center:
Recommendation #1: actually authenticate users
Most call centers only identify the user, not authenticate. In my research, most companies used knowledge factors like phone numbers, emails, or social security numbers to validate that they were talking to the right person. The problem is that these are all pieces of information about a person that are relatively easy to find (or buy).
You wouldn't let someone log into your website with just a phone number and email address, so why do we let people do it over the phone?
We recommend using a possession factor, or something physical the user has, to actually authenticate the user. If you're going to use a knowledge factor, use something that isn't possible to google, like a PIN or verbal password.
Here are five options to actually authenticate users:
- SMS verification One-Time Passcode (OTP)
- Email verification OTP
- Callback
- Service codes
- PIN or verbal passcode
After identifying the user, send an SMS OTP to the phone number attached to their account (if they have a mobile phone). Check out Twilio's Verify API to get started or use the Verify+Flex plugin. Amazon does this as part of their automated system, and it's easy to use:
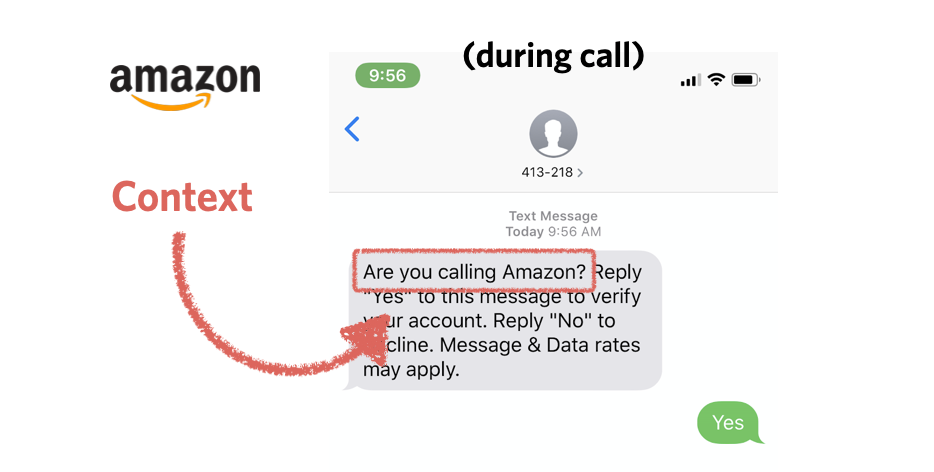
While SMS is a less secure form of 2FA, it's still way better than nothing: a 2019 Google study found that SMS tokens "helped block 100% of automated bots, 96% of bulk phishing attacks, and 76% of targeted attacks".
2. Email verification OTPIf the user is unable to receive an SMS (has a landline, is traveling, phone number has changed), you could send a verification code to the email address on file. Check out Twilio's Verify API email channel to learn more.
3. CallbackVerizon used this technique the last time I called them - the agent called me back immediately at the number on file. This has the same effect as an SMS 2FA -- trust that the customer is not spoofing the phone number -- and is a good option if your customer can't receive an SMS or email (i.e. landline callers).
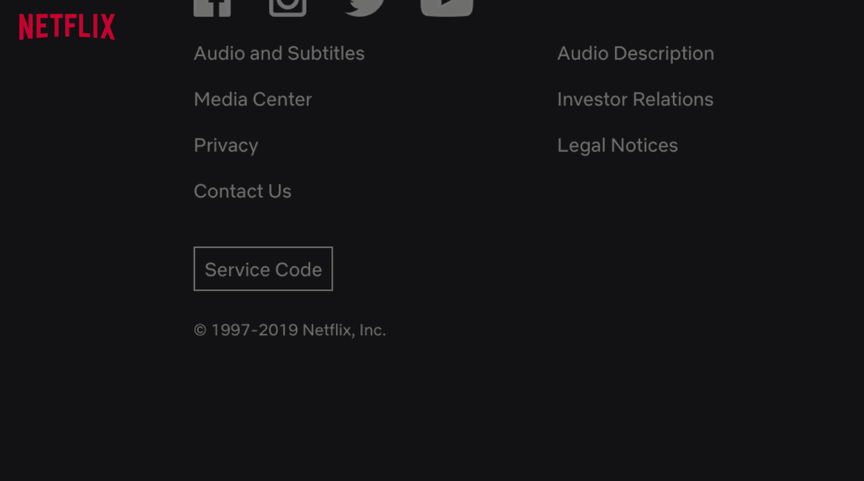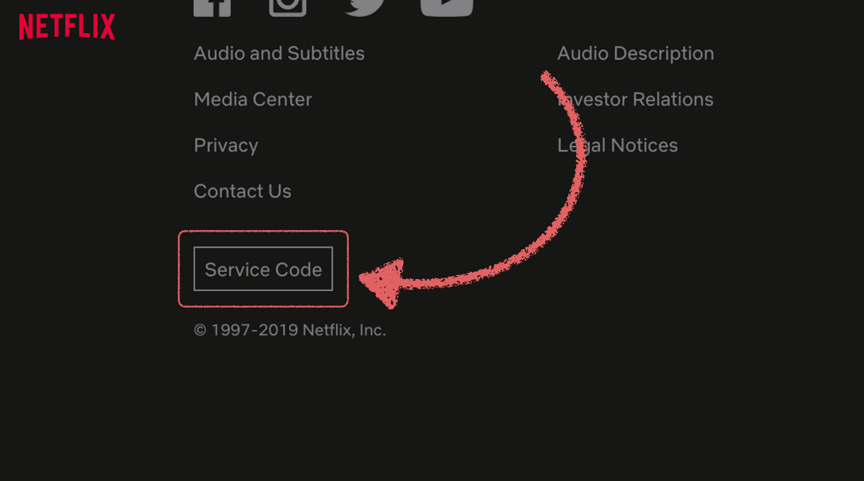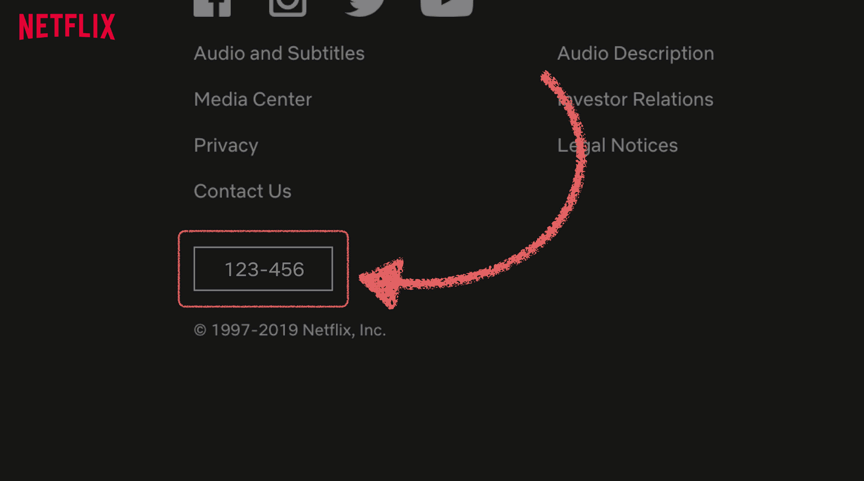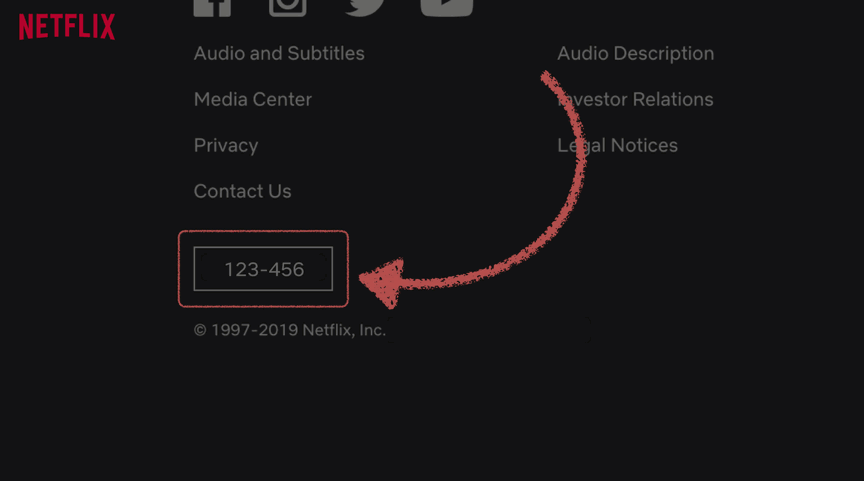
This set of methods assumes that the user is logged into or can log into their web account. This is a reasonable expectation for some of your customers, and encouraging it can save you time.
If you have one, sign into your Netflix account, scroll all the way to the bottom (keep going, eventually it will stop loading content), and click on the "Service Code" button.
Months after discovering this feature, I met Carlota, one of the brilliant people behind the implementation at Netflix who explained how it works: clicking the Service Code button generates a token and syncs with the Netflix support system so help desk agents can see the code. Codes expire in ~24 hours. When you call and provide the code, agents can trust you are the person tied to the account.
This approach requires that customers log in to generate the PIN, but has the advantage that they won't forget it. Carlota was careful to mention Netflix's implementation has likely evolved since 2012, but the general approach still makes a lot of sense.
Other examples of on-demand PINs can be borrowed from TV authentication, which has a similar challenge that entering (or saying) a password is hard. Here's an example of how YouTube prompts you for authentication:
5. PIN or verbal password
Many mobile carriers use a PIN to verify users when they call. This is an additional knowledge factor (different from the website password) that is easy to say over the phone (important!) and more secure than a searchable knowledge factor like a date of birth or your mother's maiden name.
Recommendation #2: don't share personal information
Agents providing unnecessary amounts of my personal information happened way more than I expected during my research. On one particularly egregious occasion, the agent greeted me with:
"Can I confirm that I'm speaking with Kelley Robinson? Ok. To verify your identity please provide your full name."
On a different occasion, a utility company detected my phone number and offered my full address in an automated greeting.
Offering personal information puts your customers at risk from potential stalkers and other attackers that can use the information to "authenticate" victims' identity in other call centers. You can train your agents to be wary of requests for such information, or better yet build guardrails so they are unable to provide the information.
Recommendation #3: build guardrails for your agents
Your agents are trained to be helpful since most conversations are with legitimate customers. We can't blame agents for wanting to be helpful, but if your business deals with valuable customer data, one way to protect both agents and customers is to build guardrails.
This includes:
- Limiting caller information available to agents
- Only exposing information after a caller is properly authenticated
- Having dedicated agents that have access to do the most sensitive actions
All of this is possible with Twilio Flex, our highly customizable cloud contact center product.
Services like VoiceIT, TRUSTID, Nice and Pindrop perform fraud detection that may help you determine caller risk to protect agents and save time, but these methods are more opaque to you and the end user.
Inherence factors like voice recognition are also an option, but some services for this are unproven or racist.
Recommendation #4: consider your threat model
All of this advice is going to depend on how much value your business is protecting and the level of friction your customers are willing to accept.
Take inventory of what you're allowing customers to change over the phone and consider limiting sensitive actions if you can't implement true authentication. I called a shipping company to change the address on my account and they told me I had to do that online. I think that's a fine solution.
One credit union call center implemented a policy where "if callers flub two verification questions, they must visit a branch for positive identification." This might be too much friction for an ecommerce business but could be reasonable for other financial services providers. With COVID-19, customers may be wary of any in person verification. To address this, ING bank uses Twilio to verify customers with a video call.
American Express performed some basic identification when I called, then transferred me to a specialist and sent an SMS OTP when I wanted to send a credit card to a new address. This is a good example of adapting your protections to the risk of the action. For example, reading a customer's account balance is less risky than transferring funds.
Best practices for call center authentication security summarized
There is no one size fits all solution for contact center security. I hope this post has inspired you to audit your current security and be intentional about which investments and changes you make to keep your customers safe.
Remember:
✅ Identity is not authentication. Use real authentication.
📵 Do not provide additional personal information to the caller.
💁 Make it hard for your agents to mess up. Don't let them access more information than they need.
🔐 Figure out what the right level of security friction is for your business.
Learn how to get started with Twilio's phone and email verification in our docs. Questions? Find me on Twitter @kelleyrobinson. I can't wait to see what you build!
Related Posts
Related Resources
Twilio Docs
From APIs to SDKs to sample apps
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars
Learn from customer engagement experts to improve your own communication.
Ahoy
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.

