How New Authentication Systems Can be the Key to a Password-Less Future
Time to read:

The death of the password has been predicted for quite some time now. Bill Gates pronounced the password dead way back in 2004, and every year cybersecurity experts confidently announce that the humble password will soon be a thing of the past.
In some ways, these predictions are examples of wishful thinking. The password has significant problems, and is one of the major sources of security vulnerabilities in all types of computer systems. Users typically choose weak passwords that are easy to guess, and password databases are breached all the time.
It’s no wonder, then, that cybersecurity pros hope that the password will be replaced with a stronger system. In this article, we’ll look at how the password has changed over the years, and look at two new systems – WebAuthn and FIDO – that are currently the front-runners to finally replacing the password.
The insecure history of the password
Though passwords have been used for thousands of years, their modern history starts with Fernando Corbató, an engineer who worked at MIT in the 1960s. Corbató developed the password so researchers could access their own files through the Compatible Time-Sharing System (CTSS) in use at the university at that time.

Corbato was the first to admit that the system he developed wasn’t perfect. Back then, it was never supposed to be used to protect highly-sensitive personal information. Early web services in the 1990s adopted it largely due to the simplicity of the system – with little thought given to the security implications. A password is fine for securing user files on a closed system; a password is much less suitable for protecting your bank details.
Because of the limitations of the standard password, researchers have been seeking a replacement for years. In some ways, a lot of progress has been made. In others, we are still in the Dark Ages when it comes to secure user verification.
Limitations of standard passwords
There are a number of major limitations when it comes to standard passwords. You would think if every user of every system used a strong and unique password for each account they held, the password would be a (fairly) secure solution.
Unfortunately, that’s not the case.
The first problem is that users cannot be trusted to use strong passwords. Survey after survey has found that the most common passwords are still – believe it or not – “123456” and “password”. These passwords are so common, many password crackers will try them before deploying any other techniques.
Another related problem is users are often lazy when choosing different passwords for different systems, despite the widespread availability of MFA-enabled password managers that will do this for them. Instead, many people will use the same password for every website and web service they use.
That means if a hacker gets hold of a user’s password, they have instant access to every single account. This is a particular problem when a user makes a poor password for a site that doesn’t hold personal info (which is, perhaps, understandable) and then re-uses it for more critical accounts.
Finally, even if users take their own security seriously, their passwords can still be stolen. Passwords are some of the most commonly leaked pieces of sensitive user information. A quick look at even a small part of the over 500 million leaked passwords that are now available confirms this, and it also reinforces how unimaginative people are when choosing passwords.
When combined, these issues mean the simple password is no longer a secure solution for user authentication. That’s why Twilio’s always thinking about how to encourage stronger passwords and recommend turning on Two-factor authentication everywhere it’s available.
Iterations upon the standard password
Over the past few years, there have been several approaches trying to make passwords more secure, without sacrificing too much of the simplicity that makes passwords so attractive for users.
The first of these was developed way back in the 1970s by cryptographer Robert Morris Sr., who used “hashing” to encrypt passwords. This meant that the original password was not stored in a password database, and so was more resistant to being stolen. A similar advance was made later, called “password salting”, in which random data is inserted into password databases, making them incrementally more difficult to crack.
The problem with both hashing and salting, however, is they don’t stop a password being guessed. Guessing is pretty easy if a user has not used a strong password.
That’s why the next advance in password technology sought to remove the centrality of the password. Email verification is now widely used to ensure that users are who they say they are.
One time passwords (OTP’s) provide an extra security layer for applications, and in a previous tutorial you can see how to set up a system to provide one time passwords to users via voice calls powered by Twilio’s programmable voice SDK and Laravel.
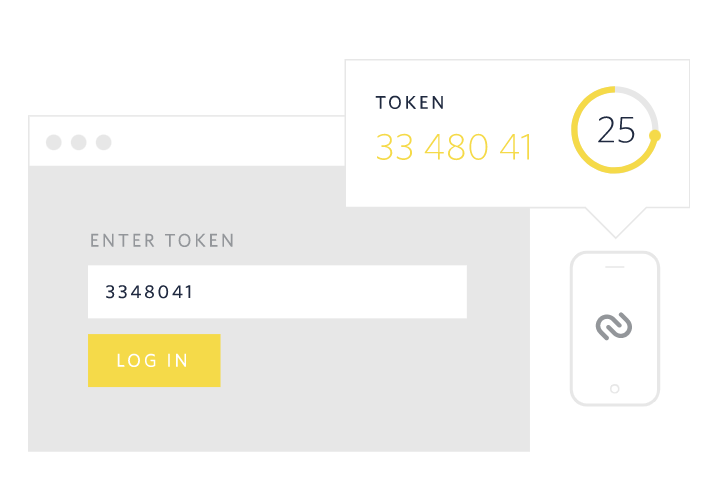
Perhaps the gold standard at the moment, though, is two-factor authentication. These systems still rely on a password, but add another level of security by requiring users to have another device – commonly a smartphone, although other devices are also used.
Twilio offers two pre-built products, Verify and Authy, which spare developers the hassle of implementing two-factor authentication systems from scratch, and make sure your verification and authentication SMS messages get to their intended recipients quickly and consistently.
WebAuthn and FIDO2 - How it works
The leading emerging solution for the replacement of the password is a protocol called FIDO2. This is a system developed by the Fido Alliance, and aims to remove passwords entirely from the authentication process.
Using the FIDO protocol, a website or app asks a user’s machine for a key. This key is a hardware-based token that proves the identity of the user. Then, the server requests a key, which requires the user to key in a PIN. Though entering a PIN might sound a lot like entering a password, in reality, FIDO2 is much more secure than traditional password systems. That’s because the PIN never leaves the user’s machine, and so cannot be stolen by a hacker who manages to intercept their connection.
FIDO, in turn, relies on a series of other protocols. The system is composed of the W3C Web Authentication specification and corresponding Client-to-Authenticator Protocols (CTAP) from the FIDO Alliance.
FIDO2 supports passwordless, second-factor, and multi-factor user experiences with embedded (or bound) authenticators (such as biometrics or PINs) or external (or roaming) authenticators (such as FIDO Security Keys, mobile devices, wearables, etc.).
Pros and Cons of WebAuthn and FIDO2
FIDO2 and WebAuthn offer a large number of advantages over traditional password-based authentication systems.
- FIDO is more secure. The protocol replaces potentially weak passwords with hardware-based authentication keys. This means no sensitive information is shared across networks, which protects users against phishing, session hijacking, man-in-the-middle, and malware attacks.
- WebAuthn can help to reduce password re-use attacks, because the user has a unique authentication key for each account they hold. These types of attacks are very common, and reducing them is a major priority for cybersecurity professionals.
- Because FIDO2 and WebAuthn are open standards, anyone can work with them. This not only allows developers to quickly take advantage of the extra security that these protocols offer but also provide a greater level of transparency into these systems.
- For even higher levels of security, FIDO can be used in combination with external authentication keys (such as USB drives), or even with biometric inputs. This makes the system highly adaptable.
On the other hand, there are a number of disadvantages of FIDO2 and WebAuthn:
- Historically, the primary drawback of FIDO2 was its compatibility with commonly used web browsers. Fortunately, that is changing now. Chrome and Firefox have announced WebAuthn API and CTAP1 support as the client, and Dropbox now integrates with the WebAuthn API. This has encouraged others to follow suit: most recently, Microsoft Edge released support for WebAuthn API, CTAP1, and CTAP2, making it the browser with the widest authentication support.
- Public key cryptography used to share authentication keys in the FIDO protocol requires a higher level of computing resources than traditional password-based systems. This means that the system is unlikely to reach low-power devices (and particularly, embedded IoT systems) for a few years to come.
Looking ahead
Whether FIDO2 and WebAuthn will come to replace the password or not remains to be seen. At the moment, these protocols are the front-runners in a race that has been going on for years, and in which many systems have been proposed and abandoned.
At the moment, the major competitor to these systems is biometrics. Biometric systems, which rely on a user’s fingerprint or retina for authentication, are becoming much more common, and – since they also don’t rely on passwords – may come to completely replace password systems in the coming decade. This is despite the implications of high level deepfakes for biometric systems, which some claim could undermine their security.
Twilio also offers functionality that allows you to easily integrate biometrics into your systems. VoiceIt, for instance, offers an extra level of security in the form of voice biometrics. Your voice is used as a key – which cannot be duplicated by hackers – to gain access to restricted data or spaces. VoiceIt integrates seamlessly with Twilio’s platform, allowing old IVR scripts to be repurposed with a voice biometrics security layer.
Whether the password will be replaced with biometrics or FIDO2 will ultimately come down to the willingness of developers to start building these authentication protocols. It will be fascinating to see what emerges as the true heir of the humble password, but one thing is clear: the password’s time is running out.
Sam Bocetta is a freelance journalist specializing in U.S. diplomacy and national security, with emphasis on technology trends in cyberwarfare, cyberdefense, and cryptography. He can be reached here on LinkedIn.
Related Posts
Related Resources
Twilio Docs
From APIs to SDKs to sample apps
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars
Learn from customer engagement experts to improve your own communication.
Ahoy
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.

