How the Verify API works
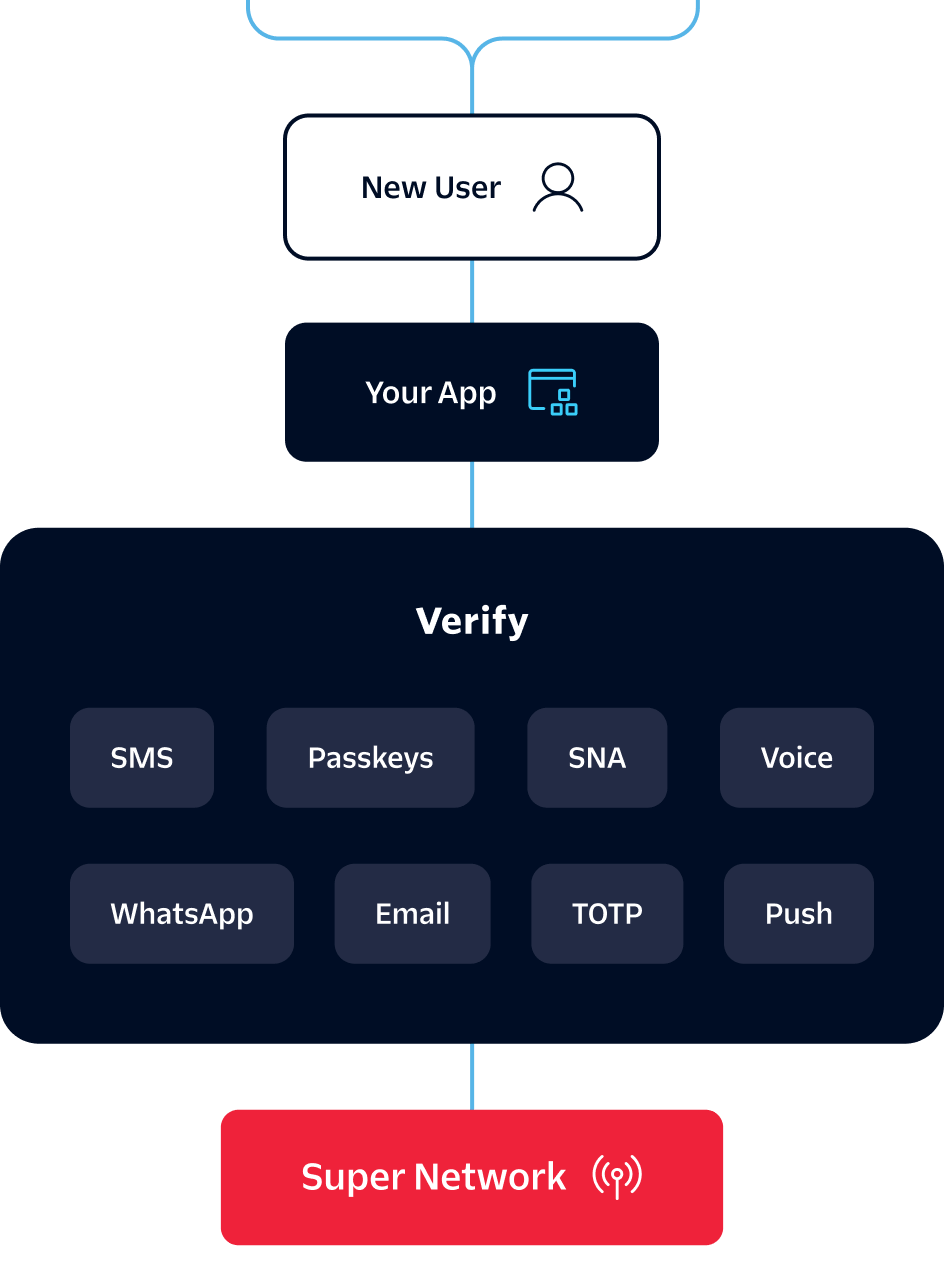

Verify is a turnkey API for user verification. Add two-factor authentication across channels like SMS, email, WhatsApp, and TOTP or implement frictionless verification with Silent Network Authentication (SNA).
Quickly integrate a one-time password authentication (OTP) solution that handles your connectivity, channels, code generation, fraud monitoring, and prevention.






