Protect Your Data with Twilio SendGrid’s Event Webhook Security
Time to read:
This post is part of Twilio’s archive and may contain outdated information. We’re always building something new, so be sure to check out our latest posts for the most up-to-date insights.
This post originally appeared on the Twilio SendGrid blog.
Corporate data breaches have increased by 67% over the past 5 years. And malicious attacks on your company do not come cheap. According to a study by IBM Security, data breaches can cost an average of $8.19M, as well as lead to multiple long term consequences. To guard against these expensive and long-lasting impacts, security against bad actors is more important than ever before.
Data breaches can be especially costly when it comes to email. Because email provides extensive engagement information, you can develop strategic programs around it. When email data is compromised, marketing and product roadmaps can be dramatically impacted.
Establishing a secure connection between you and Twilio SendGrid is critical - enter Twilio SendGrid Event Webhook Security!
Secure Event Webhook
The Secure Event Webhook guarantees that your email event data is coming directly from your Twilio SendGrid account. Protect your data and follow security protocol by implementing these two layers of security: Signed Event Webhook Requests and OAuth 2.0. These two security methods are separate, but can also be implemented simultaneously. While both are highly secure, these features serve different, but valuable security functions.

With Signed Event Webhook Requests, you are able to verify that the email event data is being posted by a trusted source. Once enabled, Twilio SendGrid will digitally sign all inbound requests before posting to your HTTP POST URL. To create the digital signature, we use an asymmetric method of cryptography. This tool is highly secure and easy to implement, as we have developed SDKs for all major languages.
Twilio SendGrid also supports OAuth 2.0. This feature verifies and authorizes Twilio SendGrid, ensuring requests are originating from a trusted source. Through OAuth 2.0, you use the Client Credentials grant type, which requires Twilio SendGrid to post a token with each Event Webhook request. This process provides enhanced security, as well as control over which events you would like to be posted to the URL. However, it also needs advanced configuration, requiring you to provide information for the authorization process.
How Signed Event Webhook Requests works
When you enable Signed Event Webhook Requests, Twilio SendGrid will generate a public/private key pair. The private key is only visible to Twilio SendGrid and accessed when creating the digital signature.
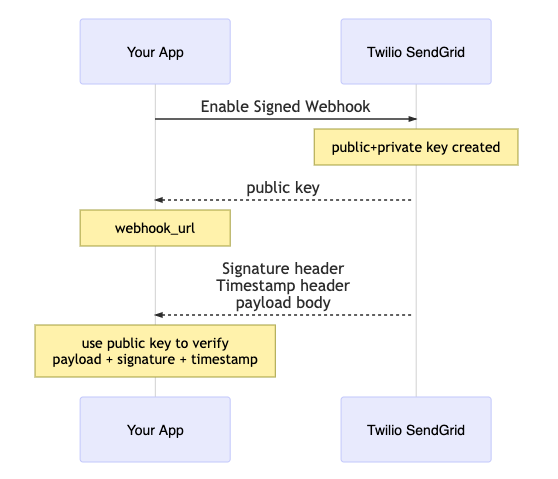
Using Elliptic Curve Digital Signature Algorithm (ECDSA), Twilio SendGrid will use this hash and the private key to create a digital signature. The signature is then base64 encoded and added to the request as an HTTP header (X-Twilio-Email-Event-Webhook-Signature). The timestamp is also added as an HTTP header (X-Twilio-Email-Event-Webhook-Timestamp) as a measure against replay attacks.

We highly recommend using a package or library from any of our supported languages to automate the signature verification process and make things easier.
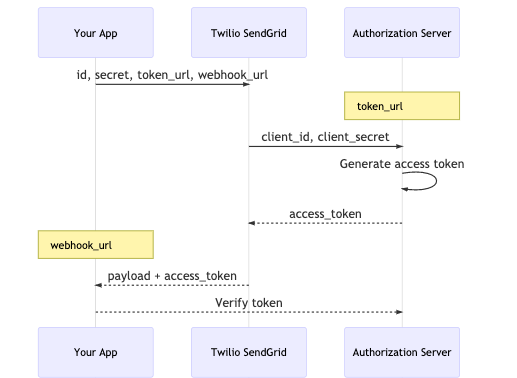
You’ll need to provide a Client ID, a Client Secret, and a URL to the authorization service (the token URL), and save this information when creating or editing your Twilio SendGrid Event Webhook. Once saved, Twilio SendGrid will pass the Client ID and the Client Secret to the token URL and request an access token. The token will then be added to the request as an HTTP Authorization header before posting to your HTTP POST URL. You can trust that the Event Webhook is the verified sender because the token is only shared among your authorization server, Twilio SendGrid, and your application.
Now that you understand how to secure your event webhook, you can implement these new features in your Twilio SendGrid console today! To get set up, follow the instructions provided in Getting Started with the Event Webhook Security Features.
Madison is the Product Marketing Manager at Twilio SendGrid, where she evangelizes email as a vehicle for customer engagement. She is passionate about the power of analytics, and leverages data to drive product insights and GTM strategy. When not in a spreadsheet, you can find her quoting The Office or hiking with her dog, Ziggy. She can be reached at mspringgate [at] twilio.com or on LinkedIn.
Related Posts
Related Resources
Twilio Docs
From APIs to SDKs to sample apps
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars
Learn from customer engagement experts to improve your own communication.
Ahoy
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.