Email to SMS Gateways Are Going Away. How to Keep Your Alerts Working with Twilio Programmable Messaging
Time to read:
Starting July 31, 2024, Twilio SendGrid blocked all email to SMS gateway traffic in line with carrier requirements and industry standards. Any email sent to an address like 14155551212@txt.att.net is no longer delivered. Charges will still apply for these attempted messages. Twilio’s Email Policy and Acceptable Use Policy prohibit email to SMS gateway traffic. Carriers no longer allow you to use public gateways due to spam concerns, reliability issues, and better alternatives. In this post, we’ll detail an alternative method which adapts your previous infrastructure, so you no longer rely on public email-to-SMS gateways for delivery.
If you’ve built or rely on a public email-to-SMS gateway, it’s time to change – what can you do now?
- Rewrite your legacy systems to use an SMS API (costly and complex)
- Or, you could drop in a SMTP server that receives emails, verifies permissions, then makes Twilio SMS API calls. Your legacy systems keep working as they are.
This guide walks you through option two: setting up an SMTP to Twilio SMS gateway so your existing systems can keep working with minimal changes. We’ll also help you set things up in a way that supports long-term reliability and best practices.
Why Email-to-SMS gateways are dying
AT&T officially discontinued its email-to-text service in 2025. Other carriers are following suit or filtering these messages aggressively to combat spam.
While these gateways worked for years, email-to-SMS gateways are no longer reliable. Carriers are ending support because:
- They’re spam magnets
- Delivery is unpredictable
- Better, more secure options exist (like Twilio’s Programmable Messaging API)
If your business relies on timely alerts that were previously delivered through an email-to-SMS gateway, continuing to use a legacy system that’s being phased out will pose challenges. With this SMTP-to-Twilio Programmable SMS gateway, the email stays within your internal network. Your SMTP server receives the message, validates that it’s coming from an authorized sender, and sends an SMS via Twilio’s Programmable Messaging API. This setup can help you move away from legacy gateways while supporting more reliable and maintainable alerting.
How the SMTP-to-Twilio gateway works


- Your app sends an email to something like 14155551212@ yuktiahuja.com
- The SMTP server receives the message within your local network. In this demo, the email is never really delivered across the public internet. It acts as a local trigger that gets converted into a standard SMS request
- The server checks that the sender is authorized to use the gateway
- It extracts and normalizes the phone number
- It sends the email body as an SMS via Twilio’s Programmable Messaging API
If the phone number is already in E.164 format (e.g., +14155551212), it’s used as-is. Otherwise, it’s converted based on your default region (e.g., US).
Prerequisites
- Node.js v18 or higher
- A Twilio Account ( Sign up with Twilio for free if you haven’t yet)
- Docker (optional)
- Clone the repo
- Buy an SMS-enabled Twilio number
How to set it up
Now that you've got your accounts and numbers set up, you’re ready to start the build. We’ll run you through the major steps you’ll need to build an SMTP to SMS bridge. After that, you’ll be able to test locally with internal users and authorized numbers.
Step 1: Install dependencies
Run:
Step 2: Create a .env file
Create an .env file, then open it with your favorite text editor or IDE. Edit the following lines:
You can find TWILIO_ACCOUNT_SID and TWILIO_AUTH_TOKEN in your Twilio Console. Use the SMS-enabled number you purchased during the Prerequisites (in E.164 format) as the TWILIO_PHONE_NUMBER.
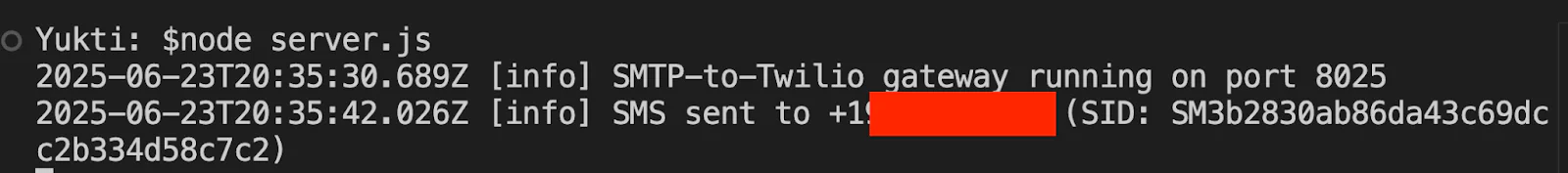
Step 3: Run the server
And that’s all you need – run the server, then you can move on to testing.

Alternatively, you can run the setup with Docker:
Or as a systemd service:
Redirecting legacy systems
To avoid disrupting production systems during setup or testing, we recommend first validating everything in a staging or test environment.
Update your legacy system’s hosts file to point to your chosen domain ( yuktiahuja.com for this example) to the IP address of your SMTP gateway. This lets your legacy application route messages to the new gateway without modifying any production code.
How to test
At this point, a small set of internal users should test the new functionality. Here, we’ll lay out a few ways you can validate your setup.
Using swaks: (a flexible and scriptable SMTP testing tool):
Next, we’ll discuss what you’ll need to do for production.
Security and On-Premises deployment
Why security matters
This project sets up an SMTP server that accepts emails, validates the sender is allowed to trigger a message, then forwards SMS via Twilio’s Programmable Messaging API. If you use a setup similar to this in production, it’s crucial that you consider the following security practices to limit abuse and ensure access is restricted to only authorized senders.
What you really, really, really need to do
- Only allow systems on your internal network to send emails to the server. Firewalls, access control lists, or a VPN can help lock this down.
- Add SMTP authentication and enable TLS. This prevents random bots from abusing your server. See this blog post on SMTP security written for SendGrid, the same best practices apply to any SMTP server
- Monitor your logs regularly for unusual or non-baseline activity, such as a sudden spike in message volume or messages coming from unexpected sources. Set up alerts to catch this early, and make sure to keep your dependencies up to date to patch known vulnerabilities.
- If you're using this with legacy systems that can't be changed, run the gateway on a machine inside your network. Don't expose it to the internet.
Get ready for production
Once you’ve thoroughly tested your setup with an internal audience and a limited set of valid outbound SMS numbers, you’ll want to ensure a few other things are in place before going to production.
- Use a reverse proxy like Nginx and a process manager like PM2 or systemd to keep things stable. See this Twilio guide on handling SSL termination for secure WebHook setup behind Nginx or a load balancer.
- Add authentication and TLS to your SMTP setup.
- For high volumes or retry handling, plug in a queuing system like Redis or RabbitMQ.
And once you’re successfully in production, monitor SMS delivery through Twilio and make sure errors don’t go unnoticed.
If something breaks
- Check the Twilio logs first, they’ll often tell you what’s going wrong.
- Make sure your Twilio Account SID, Auth Token, and phone number are all correct.
- Confirm that port 8025 or your SMTP port is open and reachable from wherever your email is coming from.
With a little care, this setup can help you keep legacy systems sending alerts without opening yourself up to fraud, abuse, and other risks.
Conclusion
Legacy systems may be hard to change, but the infrastructure they rely on is disappearing. If you're still using email-to-SMS gateways, now’s the time to adapt.
This SMTP-to-Twilio Programmable Messaging gateway gives you breathing room to keep critical alerts working while you plan your long-term move to a modern messaging stack.
As you plan ahead, consider migrating fully to Twilio Programmable Messaging. It offers a more reliable, and flexible way to send messages versus the legacy email gateways. With features like delivery tracking, better control, and support for modern messaging use cases, it’s a scalable option that can grow with your business.
Alex Chun is a Solutions Engineer at Twilio.org. Alex Chun partners with social impact organizations to create tech solutions for communication workflows. His areas of interest are hotlines, technologies for helping climate changes, and animal rescue. You can reach him at achun [at] twilio.com .
Yukti Ahuja is a Principal Solutions Engineer at Twilio. As an SE, she is a problem solving extraordinaire, blending technical expertise to bridge the gap between complex technology and practical solutions for customers. You can reach her at yahuja [at] twilio.com .
Related Posts
Related Resources
Twilio Docs
From APIs to SDKs to sample apps
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars
Learn from customer engagement experts to improve your own communication.
Ahoy
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.