Scan your projects for crossenv and other malicious npm packages
Time to read:
This post is part of Twilio’s archive and may contain outdated information. We’re always building something new, so be sure to check out our latest posts for the most up-to-date insights.

On August 1st, Oscar Bolmsten tweeted about how he found a malicious npm package called crossenv that scans for environment variables and POSTs them to a server.
@kentcdodds Hi Kent, it looks like this npm package is stealing env variables on install, using your cross-env package as bait: pic.twitter.com/REsRG8Exsx
— Oscar Bolmsten (@o_cee) August 1, 2017
This is particularly dangerous considering that you might have secret credentials for different services stored in your environment variables. Apparently it’s also not limited to just crossenv, but a series of packages — all of them are names of popular modules with small typos such as missing hyphens.
Check your project for malicious packages
These packages have been taken down by npm, but since credential theft happens upon installation, you should check if you have installed one of them. Ivan Akulov was so kind to compose and publish a list of (at least some of) these malicious packages on his blog. He also wrote a small one-liner that you can execute to check if these packages are installed in your current project:
Search for infected projects on Mac/Linux
If you are like me a person who regularly develops Node.js applications you might have a series of projects and not just one project to check for. I extended Ivan’s command for that reason using find and xargs to actually scan all subdirectories of the folder that contains my projects and execute Ivan’s command there. You can run it by simply copy pasting this command into your command-line:
I know this is quite a long command so what does it do?
- It searches recursively from your current directory down into the subdirectories for folders that are named
node_modulesusing thefindcommand. The depth is currently limited to 4 but you might want to alter that depending on your project structure. - It will then use
xargsto parse and execute a command for every line (e.g. directory) that is returned byfind - The command that it will execute in a new shell instance performs a few things by itself:
- First the shell navigates into the parent directory of the
node_modulesfolder - It will print the current directory using
pwdto show you which directory it’s currently scanning (no worries it doesn’t mean that that directory is infected) - Afterwards it will run
npm lswhich lists all installed modules of that project - Since
npm lsmight output some errors of missing dependencies or similar we will pass all messages tostderrto/dev/null(i.e. discard them) - For everything else we will pipe the output through
grepto check if it contains any of the malicious packages. If it finds one it will list it under the the respective path.
Search for infected projects on Windows
That command works when you are on Mac or Linux.. Corey Weathers wrote a small PowerShell script for that will do the same thing on Windows:
How do I see if it found a malicious package?
The output should be similar to this example (where I actually searched for express instead to demonstrate it).
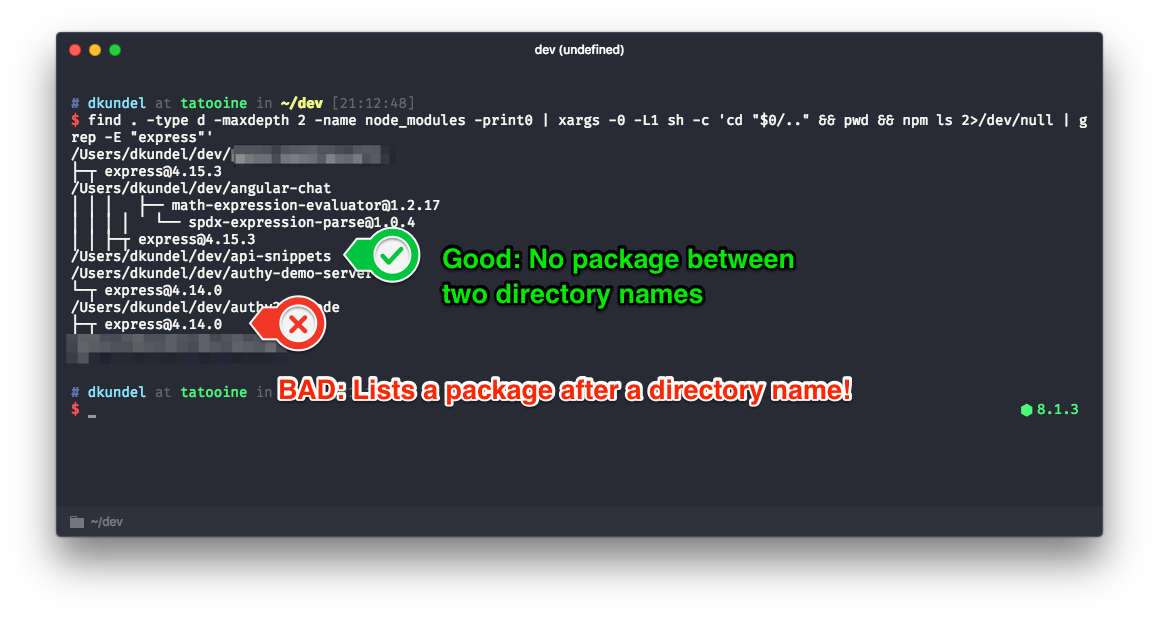
What if a malicious package was detected?
You should immediately rotate all secrets that you have stored in the environment variables. If it’s a project that is shared with other folks don’t forget to alert them to do the same. Don’t forget that Continuous Integration systems and cloud hosts like to use environment variables as well. So if you shipped one of these projects into production or used a system that uses environment variables don’t forget to rotate them there as well.
It didn’t find any malicious packages so I’m good right?
Well this is just a list of packages that we know of but since the npm ecosystem is massive it’s hard to know if these were all. So if you want to be sure simply rotate the secrets nevertheless.
What if I found another malicious package?
If you found another malicious package make sure to report it to npm that it can be taken down as soon as possible. There is more information on how to contact them at on their website or simply shoot an email to security@npmjs.com.
Is there a way I can see if my Twilio account has been compromised?
If you discovered you used one of these libraries with an application using your Twilio Account Credentials you may want to check for unusual spike in product usage, such as phone calls or messages. Also make sure to change your secret or API Key/Secret depending on what you use.
In case you have any questions feel free to shoot me a message:
- Email: dkundel@twilio.com
- Twitter: @dkundel
- GitHub: dkundel
Related Posts
Related Resources
Twilio Docs
From APIs to SDKs to sample apps
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars
Learn from customer engagement experts to improve your own communication.
Ahoy
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.


