Why Two Factor Authentication Should be a Part of Your Security Plans for 2013
Time to read:
This post is part of Twilio’s archive and may contain outdated information. We’re always building something new, so be sure to check out our latest posts for the most up-to-date insights.

Cyber security heats up this week at the RSA Conference with more than 20,000 people in San Francisco discussing President Obama’s recent executive order, the growing number of password hacks and how to protect your business against them. Twilio will be there too talking two-factor authentication, and the pros and cons of phone-based token delivery, aka out of band communication. We believe the phone should be integral to security strategies, and below are the reasons why. Today we also released a whitepaper exploring these topics around phone-based security – download it here.
So why should you consider two-factor authentication as a security solution for your customers?
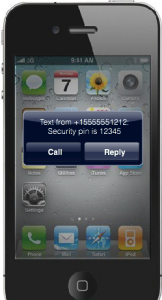
- Everyone has access to a phone. There are a billion mobile phones in the world — smart phones and features phones. And don’t forget landlines. These devices are cost-effective replacements for expensive tokens and password generators.
- Two-factor authentication doesn’t mean just pushing one-time passwords to users. With SMS, you also have an way to receive out of band inbound user verifications. With voice, you can accept DTMF verification such as seen within the finance and bank industry.
- SMS isn’t the only way of delivering one-time passwords via phone. With a platform like Twilio, you can also deliver one-time passwords via a voice call. This allows businesses to broaden their customer deployment base to not only mobile devices but landline phones as well.
- With voice delivery, a server can get acknowledgement of one-time password receipt. This allows greater flexibility in restricting the time to live of a password.
- When you look at your current system you have to ask yourself: Do you make small tweaks to existing infrastructure with an accepted user workflow or make a drastic change for marginal technical risk reduction? It is always great to look at new ideas for identity and access management; however, at the end of the day security also has to make business sense and it has been shown that two-factor authentication is a solution to strengthen your already existing infrastructure.
Phone-Based Authentication Resources
If you’re exploring how TFA fits into your security system, take a look at these resources below including some technical How To’s that demonstrate how simple it can be to implement. Download our free whitepaper here.
- Read about the solution: Two-Factor Authentication with Twilio
- Read the Docs: Twilio documentation for Two-Factor Authentication
- Technical How To: Add Two-Factor Authentication To Your Website with Google Authenticator and Twilio SMS
- Technical How To: How to Build a Phone-Based Two-Factor Authentication
- Technical How To: Build a Simple Phone Verification with Twilio, PHP and JQuery
- TFA in Action: Phone-Based Two-factor Authentication Is A Better Way to Stay Secure
- TFA in Action: The Key to Phone Verification is a Good User Experience
- TFA in Action: Authy Delivers Two-Factor Authentication Security in Minutes
Related Posts
Related Resources
Twilio Docs
From APIs to SDKs to sample apps
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars
Learn from customer engagement experts to improve your own communication.
Ahoy
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.