How to Encourage Stronger Passwords: P1e@$e $t0p Using Bad Rules
Time to read:

We have a big problem when it comes to password security.
People reuse passwords. And they use passwords that are short and easy to guess. This is a problem because even if you don’t care if your Myspace account gets hacked, if you were using the same password there as you are for your email or your bank account, you’re gonna have a bad time.
That’s because hackers will use those leaked credentials to gain access to your other accounts in a process known as credential stuffing. It’s still common practice because bad actors can make a lot of money doing this.
You may hope people have moved past using short, easy to crack passwords like 123456, but of course there are people that still use them.
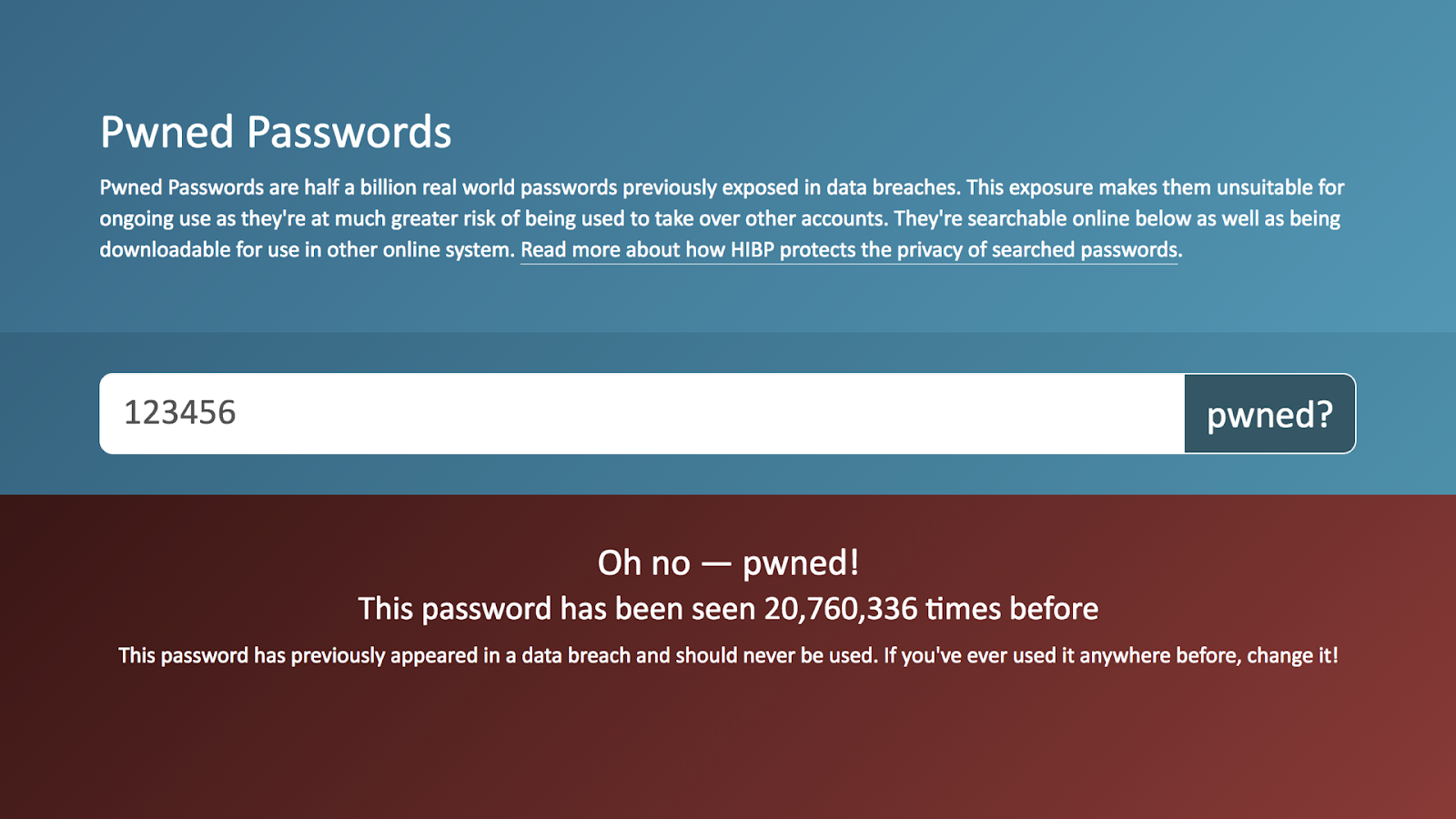
In fact this password, 123456, has been seen over 20 million times according to the site haveibeenpwned, a project from security researcher Troy Hunt. In honor of world password day Hunt suggests we should “stop using stupid passwords.” It’s good advice, but let’s provide some more specific guidance.
Defining good passwords
Stupid is a subjective adjective so let’s be more precise. Let’s say I create my next account with the password smashmouthsallstarwasalegitimatelygoodsongdontatme.
Stupid? Maybe. Secure? Yes. It’s a secure password because it’s long and that’s pretty much the only password rule that matters. XKCD explains:
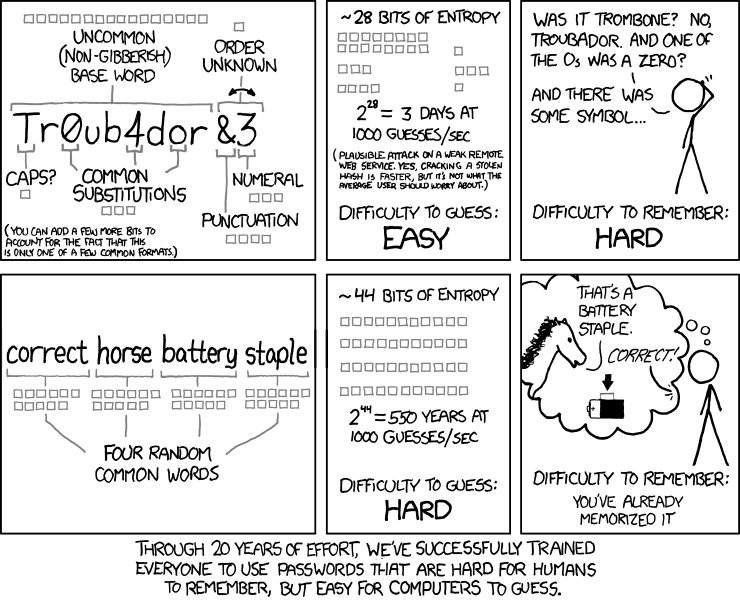
The random word method that XKCD encourages is known as Diceware, and it’s a great option to generate your password manager master password.
Burn all password rules

If you’re a web developer, take inventory on your company’s password requirements. The official recommendations that influenced thousands of websites’ security policies were updated in 2016. You can read The National Institute of Standards and Technology’s (NIST) full report for “memorized secret verifiers” (aka passwords) or see my tl;dr version here.
Some of the highlights of the updated password recommendations include:
- Don’t require arbitrary password change requirements (e.g. every 3 months)
- Stop forcing people to use special characters, uppercase letters, etc.
- Disallow passwords that have been compromised
For an entertaining (or perhaps disheartening) look at the state of password security, follow @PWTooStrong and Dumb Password Rules.
Identify what is wrong with these pictures. pic.twitter.com/KJ1XgrZI1g
— Aaron Toponce ☕ (@AaronToponce) April 24, 2018
Adding another layer
Passwords alone still leave you insecure, which is why we’re big fans of two-factor authentication. A second factor adds an additional layer of security in case the first factor (your password) is compromised. For more information, check out Authy and the APIs we offer for easily adding 2FA to your site.
Staying secure
If you’re interested in learning more about password security and Two-factor authentication:
- See how to turn on 2FA for your favorite sites.
- Find out if your email or password has been breached with Have I been Pwned?
- Add 2FA to your app with our quickstarts for Node, Ruby, Python and more.
- Encourage better passwords with NIST’s guidelines.
There is a lot of advice for security on the internet, but experts agree that the simple things like using a password manager and turning on 2FA can be the most effective for keeping your identity protected. Encourage your friends and family to adopt these practices and we’ll help make the internet a more secure place.
Related Posts
Related Resources
Twilio Docs
From APIs to SDKs to sample apps
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars
Learn from customer engagement experts to improve your own communication.
Ahoy
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.


