Everything You Need to Know About STIR/SHAKEN Right Now
Time to read:

If you’re like the rest of us, your phone rings periodically throughout the day receiving calls from numbers that look suspiciously close to your own phone number, or sometimes it is your phone number calling you. Don’t worry, you’re not seeing things, this is robocalling fraudsters trying their darndest to get you to pick up your phone. You’ve most likely blocked many of these numbers, installed apps like Hiya, Youmail, Nomorobo or Robokiller and considered throwing your phone against the wall. We get it, we’ve all been there. However change is on the horizon and it’s coming in the form of STIR/SHAKEN.
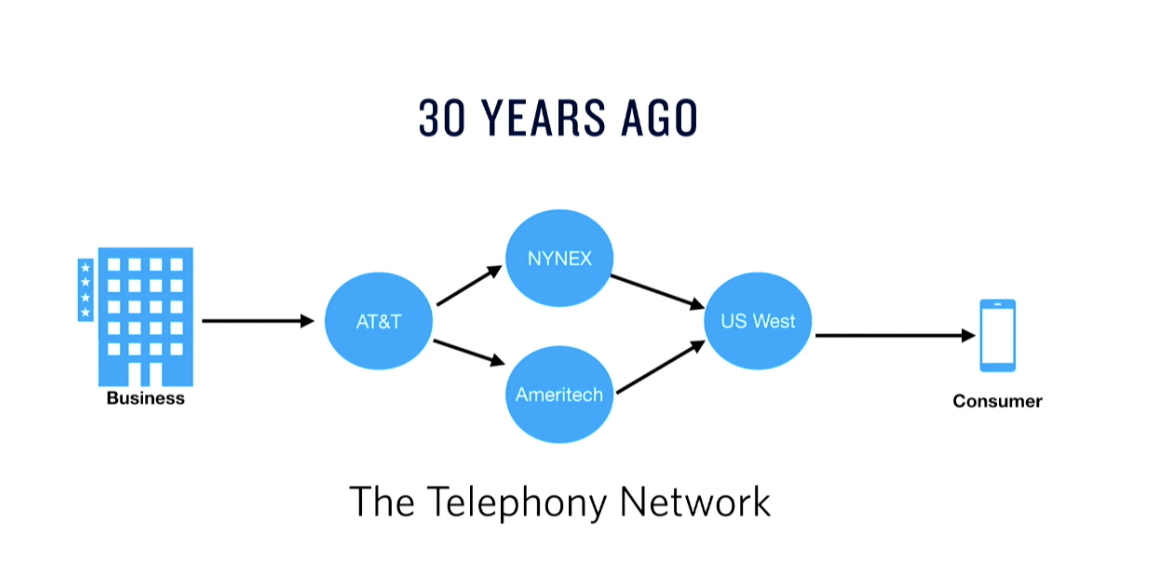
How did we get here?
Robocalls didn’t just suddenly appear one day. Robocalls are the byproduct of the evolution of telephony that has been weaponized by scammers to defraud vulnerable populations. When our parents grew up, telephony was highly regulated and people answered the phone because they trusted the caller. The advent of technical innovations such as computerized dialers, and inexpensive IP-based calling on the Public Telephone Network combined with an aging and vulnerable population are key factors in the explosion of robocalls. People who grew up trusting phone calls and still answering the phone, expecting a trustworthy person at the other end have been identified by fraudsters as an exceptionally vulnerable audience for exploitation via robocalls. Imperfect robocall detection methods complicate the issue and allow both good and bad actors to impersonate calling numbers.
Legislation alone can’t and hasn’t solved the fraudulent robocall problem: the 2009 Truth in Caller ID Act prohibits the transmission of inaccurate calling number information with the intent to defraud cause harm or wrongfully obtain something of value. The penalties run in excess of $10,000 per violation. This hasn’t put a dent in the problem and frankly is difficult to enforce. Congress and the FCC recently updated the Truth in Caller ID Act in 2019 to specifically include text messaging and include a prohibition on caller ID spoofing from outside the US.
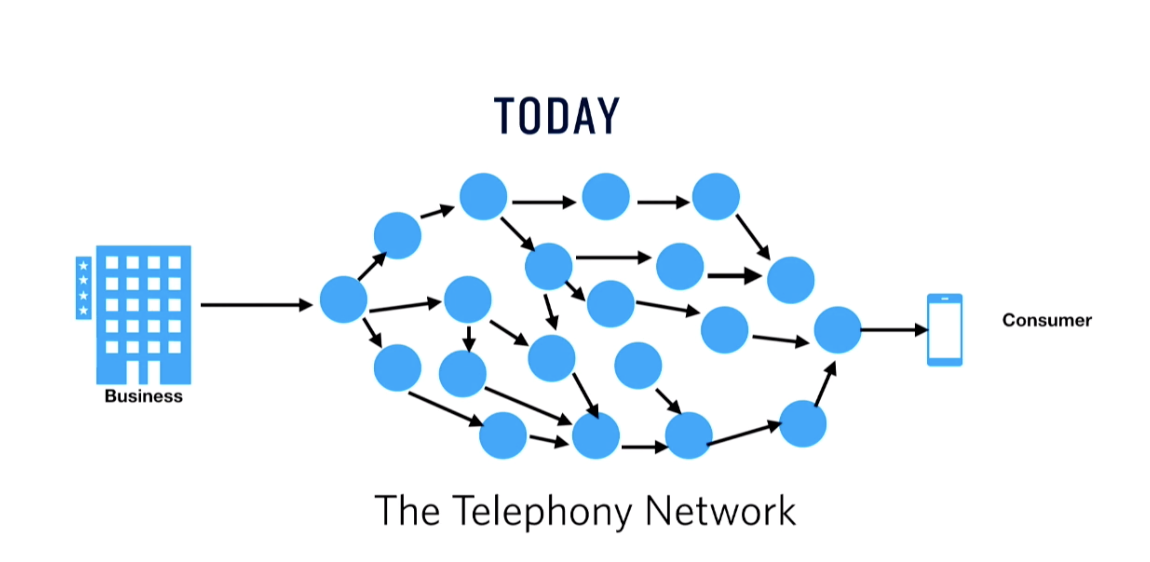
Bringing Call Authentication To the Telephony Network
STIR/SHAKEN (Secure Handling of Asserted information using toKENs)/STIR (Secure Telephony Identity Revisited) is designed to bring call authentication to the telephony network in order to verify the authenticity of the call being placed. STIR/SHAKEN will have a marked effect on decreasing the volume of unwanted and illegal robocalls which will improve the likelihood that wanted and important calls will get through and be answered. The technology uses JSON Web Tokens (JWT), if you’re a web developer just think SSL, and certificates to authenticate the caller and determine if they are authorized to use the number they’re using to place the call.
STIR/SHAKEN end-to-end
When a call is placed, the originating call provider, let’s say Verizon in this case, receives the call parameters (the from and to telephone numbers) and then uses a signing service to sign the call (for more information on Public Key Encryption check out this blog). The call is now signed with Verizon’s private key and that means that Verizon is standing behind the origination of this call and its parameters. The call traverses the telephony network to the terminating service provider. For the sake of this example let’s say AT&T. AT&T will fetch Verizon’s public key and verify that the call and associated parameters are valid through a certificate authority. STIR/SHAKEN introduces a new trust-anchor into the world of certificate signing: Secure Telephony Identity Policy Administrator (STI-PA). The STI-PA is responsible for selecting the certificate authorities and for providing Service Provider Code token to service providers so they can acquire private keys for signing calls and public keys for verifying calls. Once AT&T has the public certificate from Verizon they can verify calls and assert that the owner of the phone number is the one placing the call through a visual display, such as a green checkmark on Comcast Xfinity VoIP phones or with “Caller Verified” as seen on Android.
SIP and Identity Headers
Standard SIP headers used for passing calls through the telephony network will, in a STIR/SHAKEN world, have an identity field consisting of a Base64 encoded JSON Webtoken (JWT) that will look something like this:
The token signing URL provides information on who originated the call and is assuming responsibility for placing it. The origination ID is tied to the specific client that is initiating the call thus it creates a chain of trust between call originator and the platform that is placing the call. By being able to determine who is placing fraudulent calls it’s possible to better enforce the existing laws and curb the flood of robocalls.
What do you have to do right now?
Expect to see STIR/SHAKEN rollout in 2020 starting with the mobile operators. If you buy phone numbers from other providers then you can verify your ownership of those numbers on Twilio using the REST API https://www.twilio.com/console/phone-numbers/verified or the Console https://www.twilio.com/docs/voice/api/outgoing-caller-ids
As part of this work we have joined a number of industry organizations including becoming a board member of The Alliance for Telecom Industry Solutions (ATIS), and more recently US Telecom. On the policy and legislative front Twilio attended the FCC Robocall Summit and US Telecom Robocall Summit, demoing Twilio to Congress and supporting the TRACED Act and Stopping Bad Robocalls Act.
Hands on information on how to verify caller IDs at scale.
Stay tuned for more on that in the weeks to come!
Len Shneyder is a 15+ year email and digital messaging veteran and the VP of Industry Relations at Twilio SendGrid. He can be reached at lshneyder [at] twilio.com.
Related Posts
Related Resources
Twilio Docs
From APIs to SDKs to sample apps
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars
Learn from customer engagement experts to improve your own communication.
Ahoy
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.