Supporting Europe’s PSD2 And The Strong Customer Authentication It Requires
Time to read:
This post is part of Twilio’s archive and may contain outdated information. We’re always building something new, so be sure to check out our latest posts for the most up-to-date insights.

It seems that every month some new payment app pops up looking to be the next category disruptor. Innovative companies like TransferWise are making headlines, with simple to use smartphone apps that allow you to send money abroad, quickly and cheaply. Amazingly, Transferwise is already profitable and handling nearly £1 billion ($1.3 billion USD) in transactions a month. Bitcoin valuations are racing through the roof. And there are even lines of digital jewelry (Kerv, NFCRing). Wear one of these “payment rings” on your finger, and you’ll pay for your next burger and fries without reaching for your wallet.
In the wake of all the amazing advancements in ways to send money to friends or pay for things we buy, are regulations to ensure that consumers can use these new technologies safely and without worry. The most pressing, due to a January 2018 deadline, is the European Union Commission’s update to its Payment Services Directive: PSD2. Initially conceived in 2007, PSD created policy that regulates payment services and financial service providers throughout the European Union. Jump forward 10 years, and the payment industry is booming with new technologies and companies trying to finally bring an end to the stronghold of physical cash.
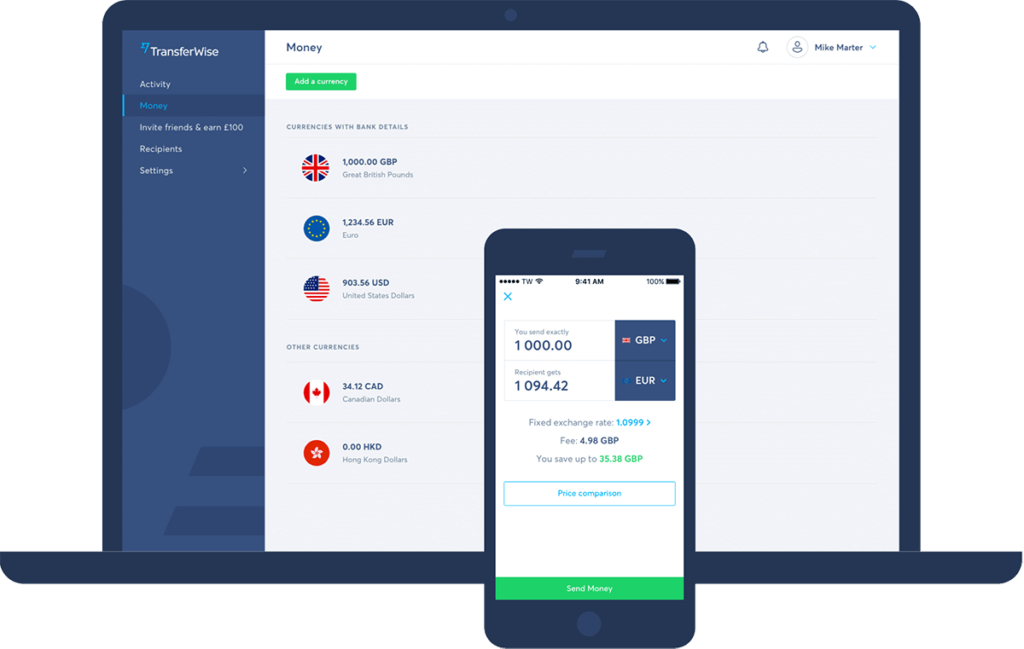
One of the significant elements of PSD2 is it will allow businesses like Amazon to connect payments directly to a user’s bank, instead of having to redirect to another service like PayPal or Visa. Of course, gaining access directly to the funds in a customer’s bank account requires their permission. It also elevates security concerns. While payment networks like Visa have built massive fraud and security systems to ensure things like stolen credit cards are prevented from wiping out a consumer’s funds, the same can’t be said for every new service that springs up
Consequently, PSD2 also comes with a new set of rules, defining what they call Strong Customer Authentication (SCA). Essentially, by opening more direct access between merchants and their consumer’s bank accounts, there must be an increased level of security in the form of strong authentication and authorizations of transactions.
The most common form of stronger authentication is known as 2FA: a security method where a username and password must be coupled with something like a smartphone-generated one-time password (OTP). However, PSD2 adds an interesting spin by requiring that all SCA must be performed by “dynamically linking” the authentication to details in the transaction. In effect, PSD2 is directing that the “channels” used in typical 2FA events (SMS, voice, push notifications) are separate from the transaction itself (on a website or in a mobile app) but dynamically linked to the transaction.
Common 2FA methods such as SMS and push authentication are perfect for this requirement. However, time-based one-time passwords (TOTP) are generated independently of the payment authorization and therefore cannot be dynamically linked.
Twilio Delivers 2FA That Satisfies PSD2 Rules and Regulations
With this new regulation, the scope for enforcing SCA has dramatically increased, and even those with solutions already in place are concerned about the scalability of existing solutions.
Twilio, one of the leading communications platforms as a service (cPaaS), knows quite a bit about sending authentication 2FA codes and account alerts via SMS at scale. We send millions of them a day. Our Authy API allows payment providers to generate these SMS codes without having to worry about the carrier policies that sometimes block SMS messages thinking they are spam. The Authy API allows for an action message to be passed along with the authentication SMS to provide the dynamic link back to the payment.
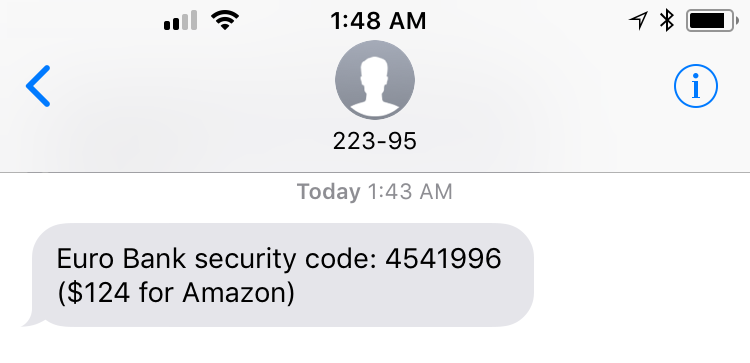
A significant step up from using SMS (which is restricted to only text with a limit of 160 characters per message segment) is a push authentication. Push 2FA uses a smartphone app to present the user with a much more user-friendly “Accept” or “Deny” message that contains a great deal of information about the transaction at hand. Developers can either enable the popular Authy 2FA app for this purpose or build the functionality into their own apps using our SDK, like the example below.
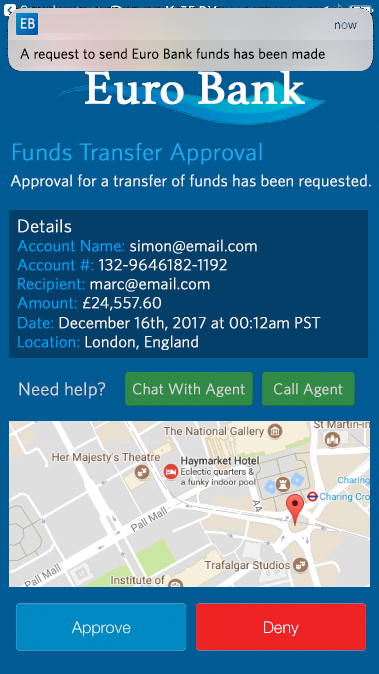
Another challenge for companies is the simple task of just notifying customers. Notifications and alerts need to be sent regarding suspicious activity such a fraudulent behaviour or non-transactional account changes, like updates to customer address. Once again Twilio has APIs that can help companies address these sorts of customer notifications at scale.Twilio Notify unifies the ability to send messages via SMS, push notifications and even Facebook Messenger, all into a single API. This makes contact consumers, over their chosen communication channels, much easier.
As you can imagine, European financial institutions and payment service providers face a new set of opportunities and challenges that accompany PSD2 requirements. Fortunately, Twilio is ahead of the curve, and has a deep history delivering sound and modern authentication solutions to a global financial industry.
For banks and payment providers, the complexities and costs of the technical improvements needed to support PSD2’s SCA requirements need to be carefully evaluated. While PSD2 becomes law in January 2018, there is still time to satisfy the SCA requirements..
You can get started now, our push authentication feature in the Twilio Authy API is the most convenient and secure of the Twilio security solutions and has been adopted as an industry go-to. Your users get better protection, and your organization adapts to PSD2 compliance faster and more thoroughly than you ever thought possible.
Need help?
- Learn more about Twilio two-factor authentication today.
- Explore the Twilio Authy APIs
- Connect with Twilio
- Or call +1-855.910.8712
Related Posts
Related Resources
Twilio Docs
From APIs to SDKs to sample apps
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars
Learn from customer engagement experts to improve your own communication.
Ahoy
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.


