Deliver Secure and Reliable OTPs with Twilio Verify and PingOne
Time to read:
PingOne now supports direct integration with Twilio Verify through its built-in custom server notification provider. This enables customers to improve one-time passcode (OTP) delivery success and reduce fraud such as SMS pumping and fake account creation. By plugging Twilio Verify into PingOne’s MFA notification system, customers gain the benefits of global sender management, intelligent fallback, and built-in fraud protection.
This guide walks through how to configure the integration using PingOne settings, with no additional orchestration tools required.
Why use Twilio Verify?
Twilio empowers businesses to stop fraud before it starts, ensuring that only legitimate users gain access while maximizing conversion rates. Twilio Verify is a fully managed OTP delivery platform that helps secure and streamline user authentication across multiple channels. Twilio Verify manages global sender pools for you so you can scale worldwide without managing phone number registrations.
Unlike basic messaging APIs, Twilio Verify adds layers of automation and routing intelligence that increase OTP delivery, and fraud protection against SMS pumping attacks. Features like Geo Permissions allow you to block OTP delivery to unwanted or high-risk countries based on the country code, helping protect your application from suspicious traffic. Twilio Verify also includes intelligent channel orchestration, built-in message localization, pre-send carrier checks using Twilio Lookup, and configurable rate limiting to help ensure OTPs reach real users quickly while minimizing delivery failures and reducing operational complexity.
With seamless integration and reduced overhead, businesses can accelerate time to market, scale authentication with confidence, and focus on growth without compromising security or user experience.
How PingOne's Custom Server setup works with Twilio Verify
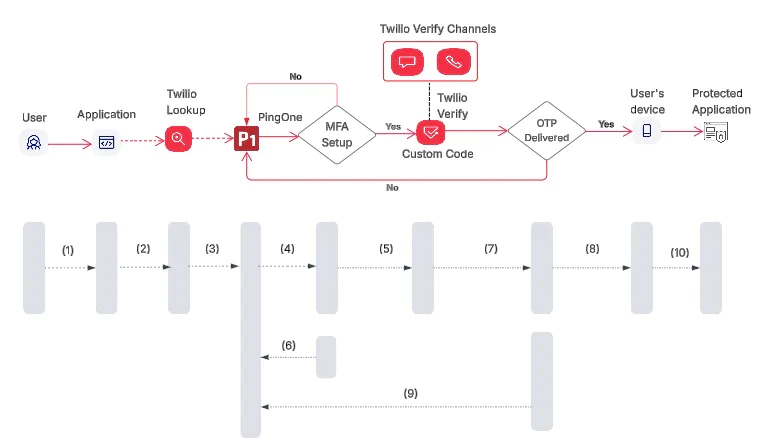

The sequence of events for SMS/Voice one-time passcode (OTP) authentication includes:
- The user enters their email and phone number on the login page of the application.
- (Optional) The application sends the user’s phone number to the Twilio Lookup API to access features like number formatting and line type detection. This step applies only if the Twilio Lookup packages have been purchased.
- The Twilio Lookup API returns the correctly formatted “To Number,” and confirms the number is a valid mobile number. The user is redirected to PingOne for authentication.
- PingOne checks if MFA is already configured for the user.
- If MFA is already configured, PingOne calls your custom server, which in turn uses the Twilio Verify API to initiate the OTP request.
- If MFA is not configured, PingOne prompts the user to enroll in MFA (e.g., SMS or Voice).
- Twilio Verify delivers the OTP to the user via the selected channel (SMS, Voice).
- Once the OTP is delivered, the user enters it on the PingOne authentication screen. PingOne verifies the code, completes authentication, and confirms the user’s identity and MFA status.
- The user can select a fallback method if they cannot receive the OTP
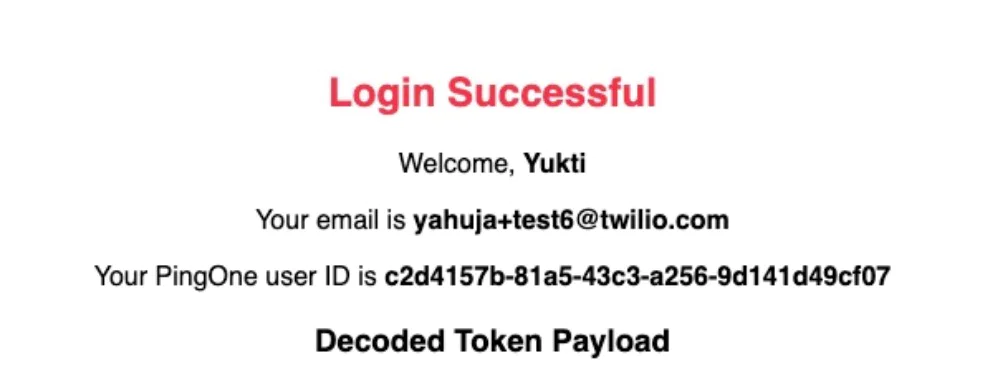
- After successful authentication, the user is granted access to the protected application. For this blog, a success screen is shown displaying the user’s name, email, PingOne ID, and token details.
Prerequisites for Sending OTPs with PingOne and Twilio Verify
Before you begin, make sure the following are ready:
- Node.js v18+ installed on your system
- A PingOne account
- A Twilio account ( Sign up or log in)
- A Twilio Verify Service created from the Twilio Console
- Twilio Account SID (starts with
AC...) - Twilio Auth Token
- Verify Service SID (starts with
VA...) - Custom Code enabled on your Verify service.
- Navigate to your Verify service → Code Configuration → Enable Custom Verification Code
Once you have those in place, we can get started.
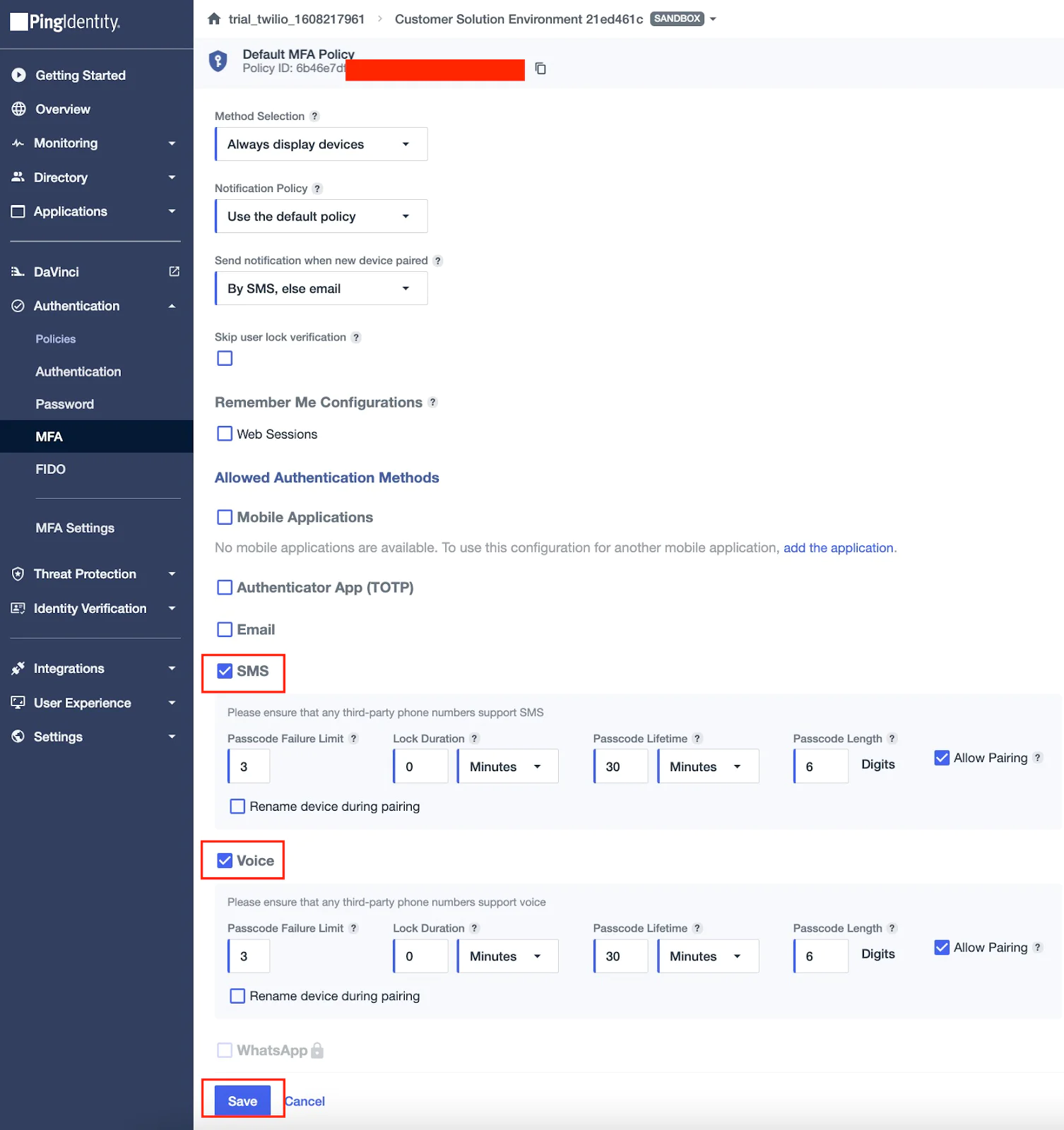
Step 1: Create or edit the MFA Policy
For this demo, you’ll need a PingOne MFA policy. You can either edit the default policy or create a new one. In this guide, we edited the default policy to enable SMS and Voice as MFA options. To do this:
- Go to Authentication > MFA
- Select Default MFA Policy
- Click on the pencil icon and check the SMS and Voice options.
- Click Save

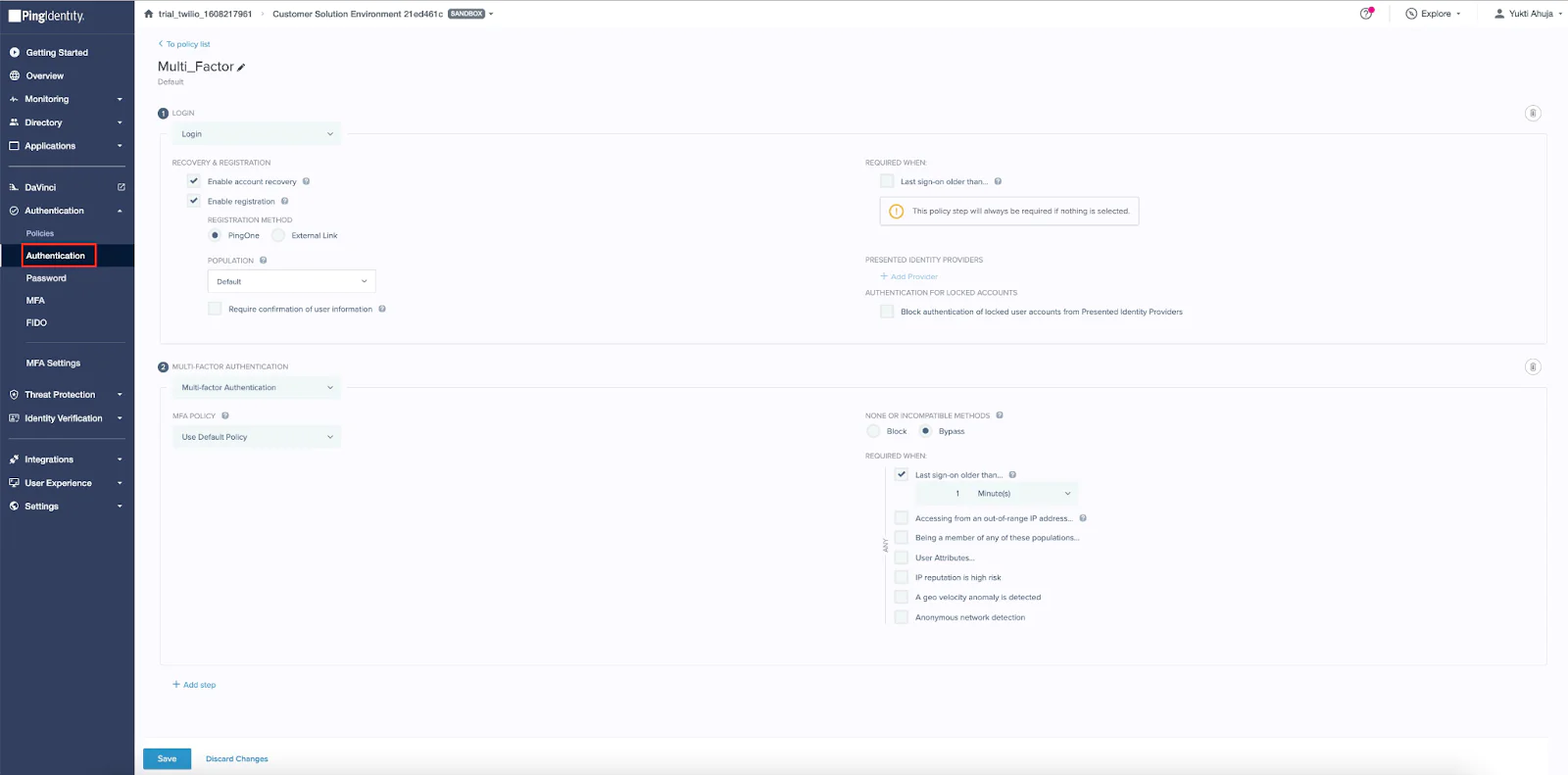
Step 2: Create an Authentication Policy in PingOne
For this demo, you’ll need a PingOne authentication policy that requires MFA. If one doesn’t already exist in your environment, follow the steps below to create a new policy:
1. In the PingOne admin console, go to Authentication > Authentication.
2. Click + Add Policy.
3. Enter a Policy Name (e.g., Multi_Factor).
4. For Step Type, select Login.
5. Under Login settings:
- Enable Account Recovery
- Enable Registration
- Set Registration Method to PingOne
- Set Population to Default
6. Click + Add Step and select Multi-factor Authentication from the dropdown.
7. Under MFA Settings:
- Choose the default MFA policy
- Set Bypass option to: None or Incompatible Methods
- Under Required When, select: Last sign-on older than 1 minute (You can adjust this time setting based on your security requirements.)
8. Click Save to create the policy.

Step 3: Create a PingOne Application
Below are the steps to add a new Single Page Application in PingOne, which will be used to log in and test Twilio Lookup and Twilio Verify. You can find more details in the PingOne documentation linked here.
To create a PingOne Application:
1. Log in to your PingOne admin console.
2. Navigate to Applications > My Applications and click + Add Application.
3. Select Single-Page Application as the type.
4. Enter your Application Name and Description, then click Save.
5. Open your newly created application and go to the Configuration tab.
6. Set the Redirect URI to: http://localhost:3000/auth/callback
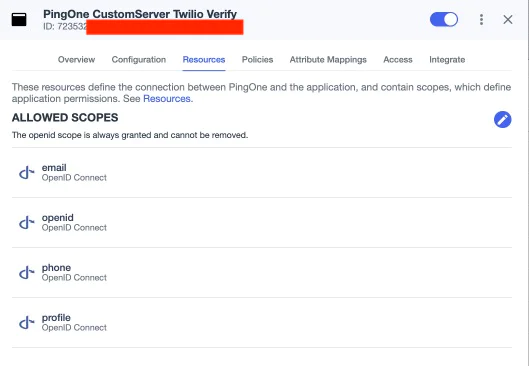
7. Switch to the Resources tab and assign the following scopes:
emailopenidphoneProfile

8. Navigate to the Policies tab and select an Authentication Policy ( Multi_factor) with MFA enabled.
9. Click Save to apply the changes.
10. Finally, make note of the following configuration values for later use:
- Environment ID
- Client ID
- Client Secret
- Token Endpoint
- User Info Endpoint
Step 4: Configure Twilio Verify in the PingOne Custom Server option
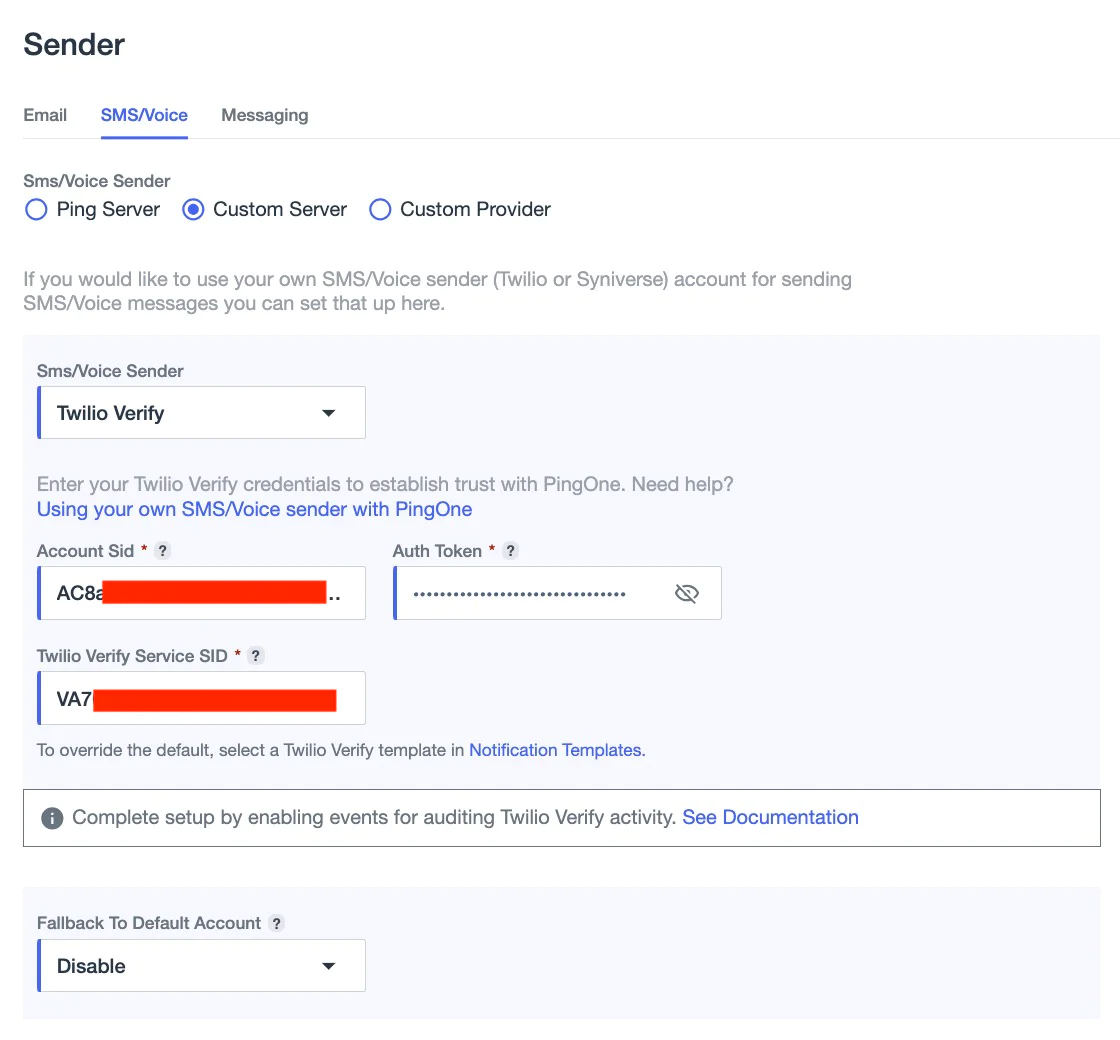
In this step, you’ll configure Twilio Verify as a custom notification provider in PingOne using the Custom Server option. This setup allows PingOne to call your backend, which then triggers the Verify API to send OTPs. You can find more details in the PingOne documentation linked here. To do this:
- Log in to your PingOne admin console.
- Navigate to Settings > Sender and click the pencil icon.
- Select Custom Server
- In the Sms/Voice Sender list, select Twilio Verify.
- Enter the Account Sid for your Twilio account.
- Enter the Auth Token for your Twilio account.
- Enter the Twilio Verify Service SID.
- Click Save.

Step 5: Set Notification Policies and Templates
There are two ways to manage notification templates for MFA in PingOne:
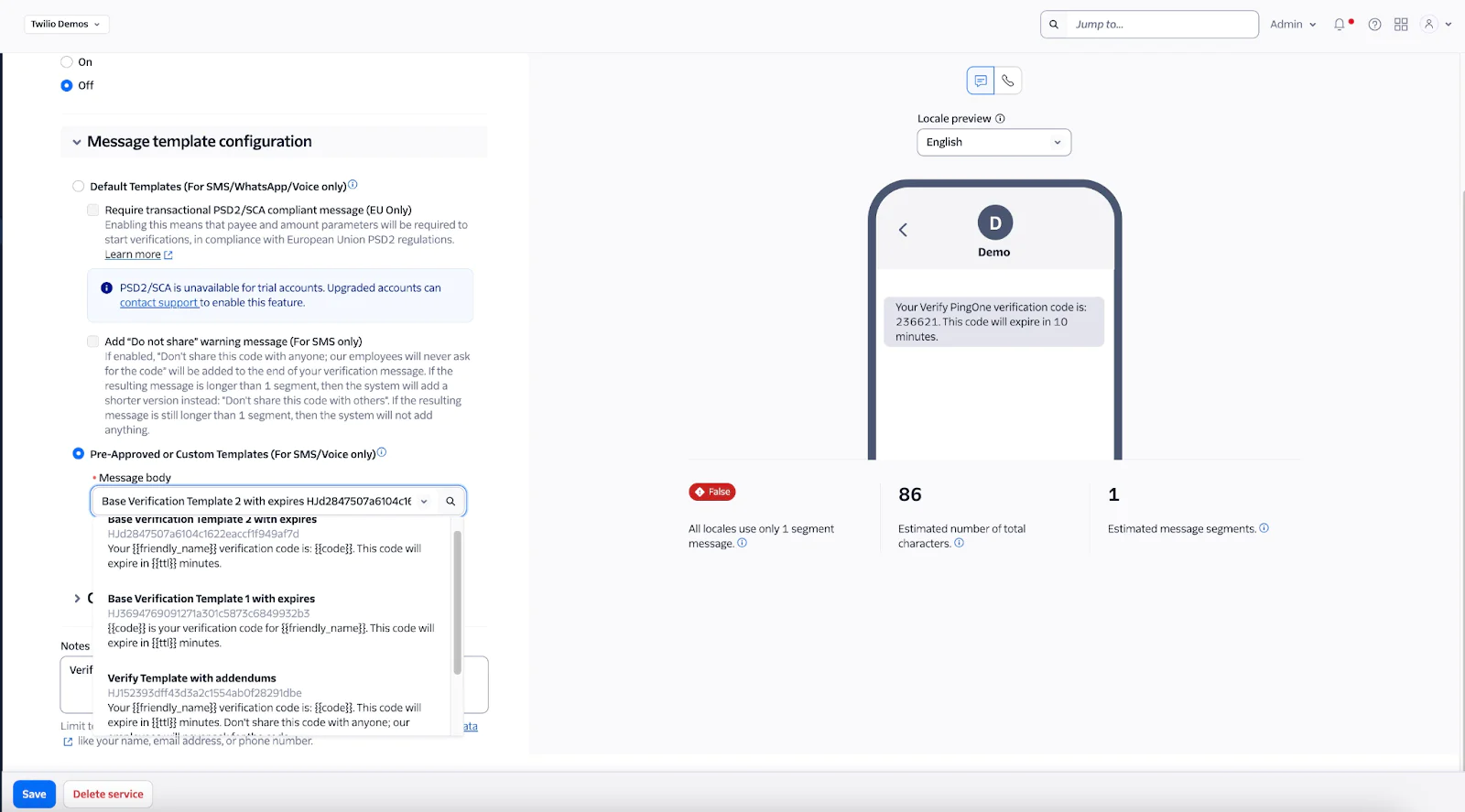
Option 1: Use Twilio Verify Templates
With Twilio Verify, you can use the default template provided or request a custom template through Twilio Support.
To configure templates:
- In the Twilio Console, go to Verify > Services
- Select your Verify Service
- Under the General tab, scroll down to the Message Template Configuration section
- From the dropdown, choose the default SMS template , pick a pre approved template or a custom template Note: Read this support articlefor more information on how to request a custom template if our other templates do not suit your business needs.
- Save the service

Option 2: Use PingOne Templates
Alternatively, you can use PingOne’s built-in templates.
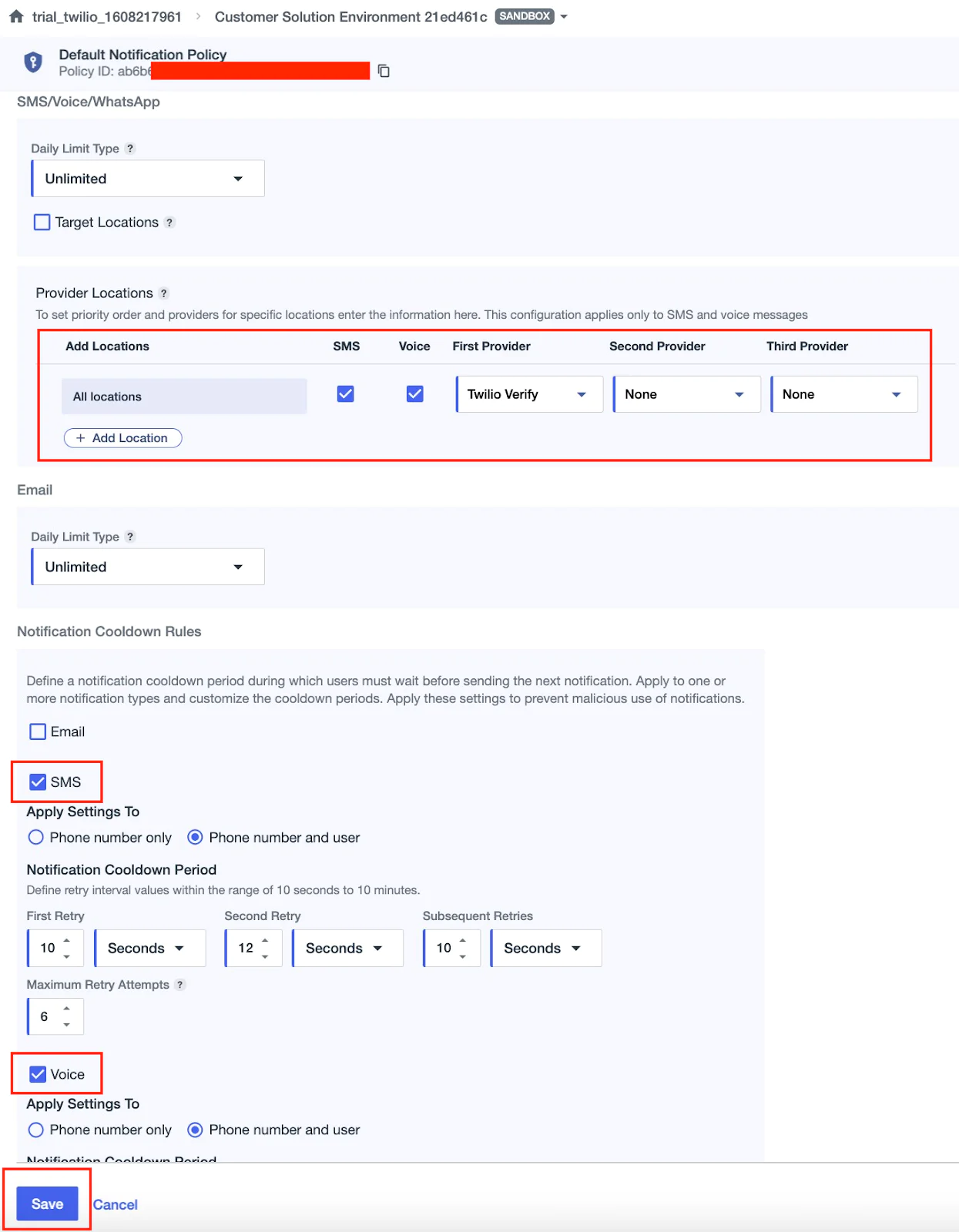
The first step is to set the Notification Policies for SMS/Voice. You can find more details in the PingOne documentation linked here.
- To do this:
- Log in to the PingOne admin console
- Navigate to User Experience > Notification Policies
- Click the policy you want to edit and then click the pencil icon, or click the plus icon (+) to create a new notification policy
- Under Provider Locations, configure the providers for SMS and Voice:
- Make sure the First Provider is set to Twilio Verify
- Optionally, set the Second and Third Providers using the dropdown if available
- Check the boxes for:
- SMS
- Voice
- Click Save

For MFA Templates:
- Use the Strong Authentication Notification Template for OTP delivery
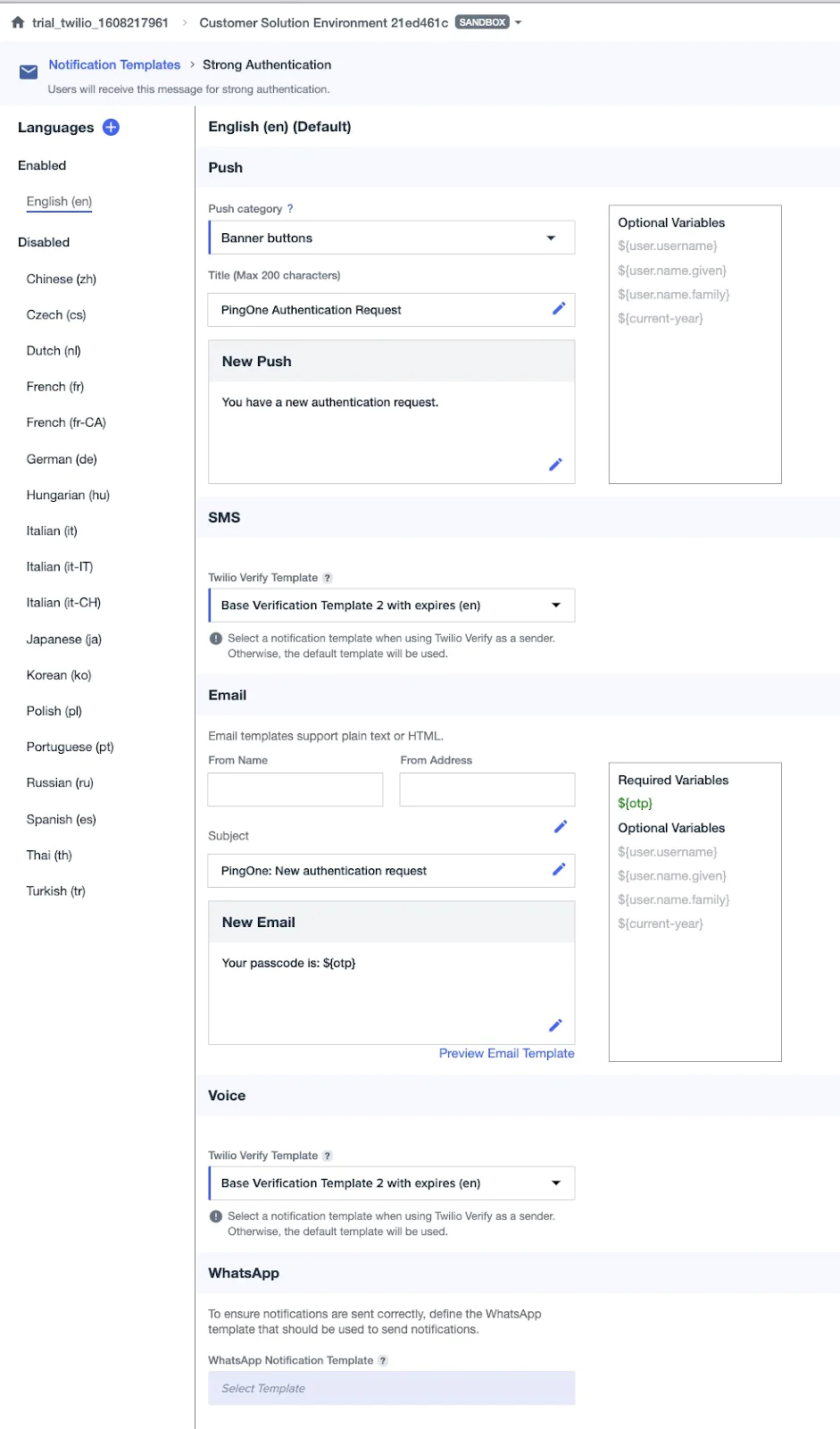

- Use the Device Pairing Template when new users are adding an MFA method
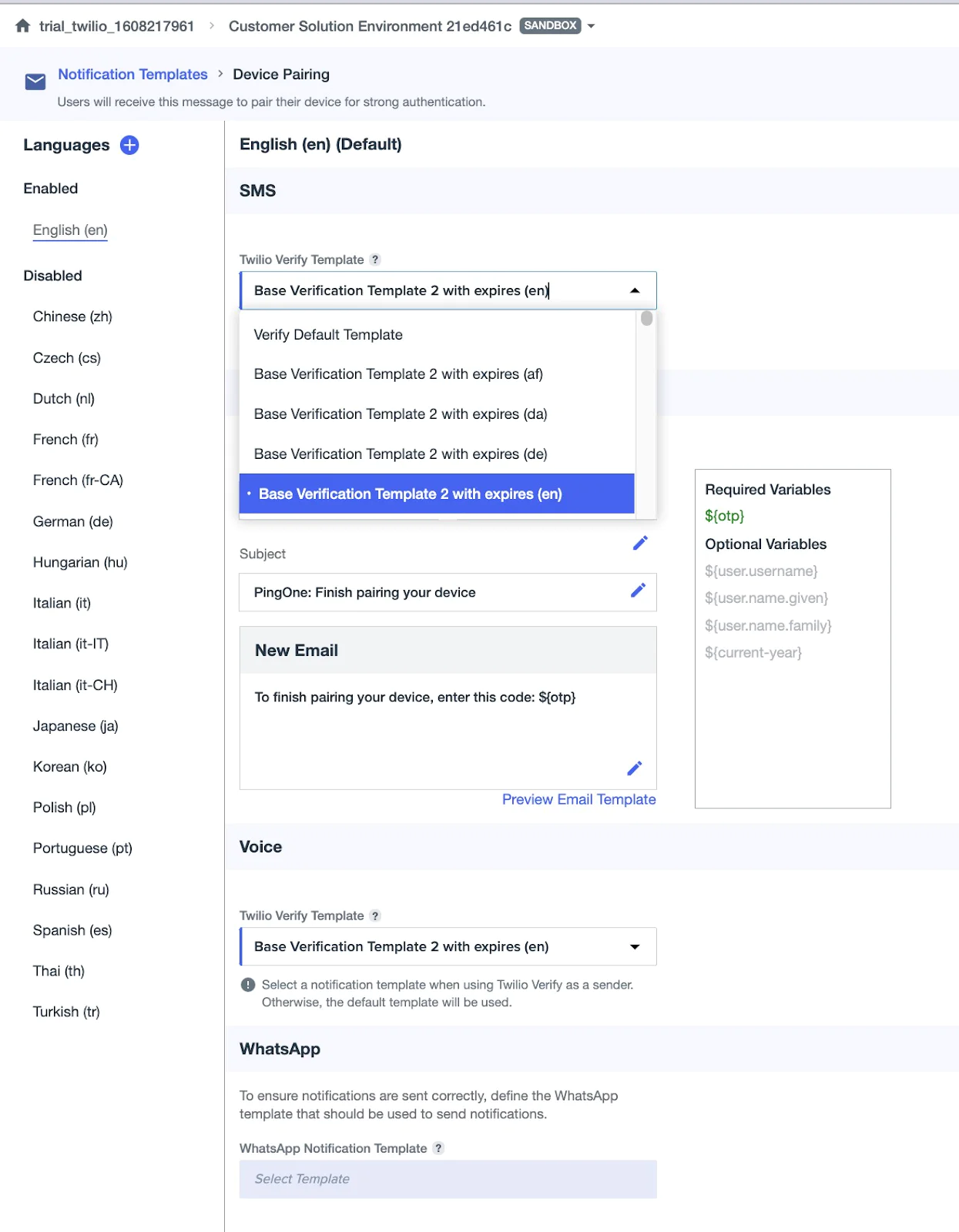

You can customize Twilio Verify templates and set locale and language preferences. If you select a Twilio custom template and leave the PingOne configuration unchanged, the message sent to users will follow the Twilio template. If you select a template from the PingOne template list, that template will override the Twilio configuration and the message will follow the PingOne version.
If you need to use your own custom templates, you must request approval by the Twilio Verify support team. After approval, they can be used in PingOne with the appropriate locale settings.
Step 6: Set up the demo application to test the integration
Clone the demo app
Clone the Node.js app from this repo:
Set up environment variables
Create a .env file by copying the example:
Update the .env file with the following values:
TWILIO_ACCOUNT_SID=Twilio Account SIDTWILIO_AUTH_TOKEN=Twilio Auth TokenPINGONE_ENV_ID=PingOne environment IDPINGONE_APP_ID=PingOne App ID from step 3PINGONE_CLIENT_SECRET=PingOne Client Secret for the app created in step 3PINGONE_REDIRECT_URI=http://localhost:3000/auth/callbackPINGONE_TOKEN_ENDPOINT= PingOne Token Endpoint from Step 3PINGONE_USERINFO_ENDPOINT=PingOne User Info Endpoint from Step 3
Install dependencies
Make sure you're using Node.js v18+ (use nvm if needed):
Start the application
Run the application
Test your application
Follow the steps below to test the end-to-end login flow using PingOne and Twilio:
1. Launch the app
- Visit: http://localhost:3000
- Enter your email address and phone number
- Click Login


2. Twilio Lookup check
1. Your terminal window will show the application's activity and debug output.
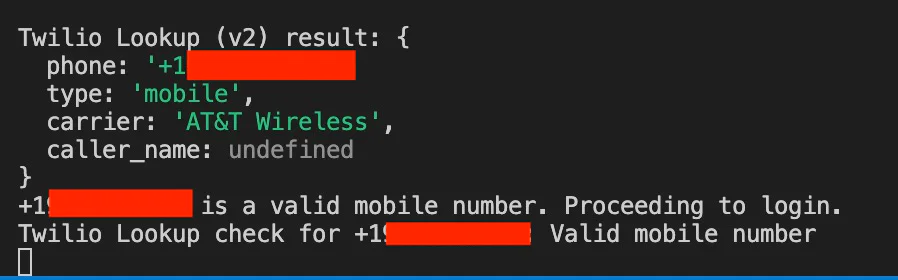

2. If the phone number is invalid, the app will stop and prompt you to enter a valid number.
3. This validation is powered by the Twilio Lookup API, which ensures only valid mobile numbers proceed to authentication.
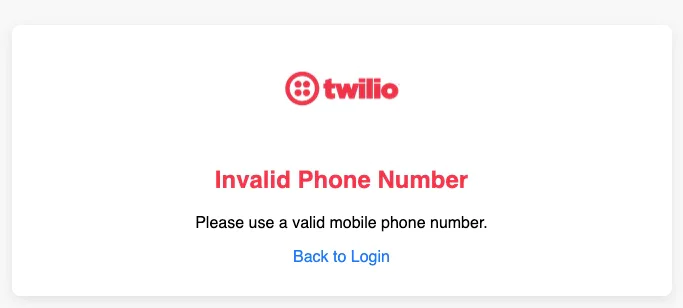

3. Redirect to PingOne Login
- If the number is valid, you will be redirected to the PingOne login screen.
- Make sure the user you're logging in with is already created in PingOne and has MFA enabled.
- You can customize the branding and themes for this login page in the PingOne admin console.


4. First-time login experience
If this is the user's first login:
1. PingOne will prompt the user to reset their password.
2. After that, it will prompt the user to enroll in an MFA method (SMS or Voice).
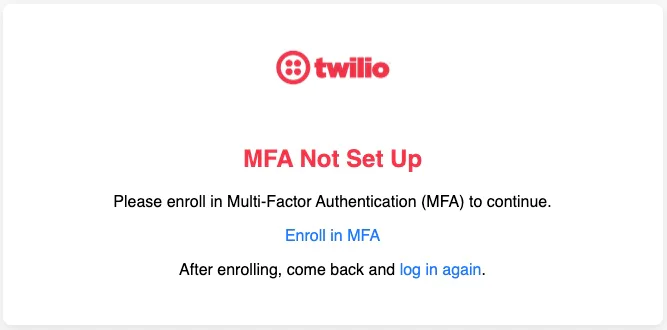

3. Click Enroll in MFA.
4. A new window will open to add an authentication method.
5. Enroll in MFA
1. Click Add Method
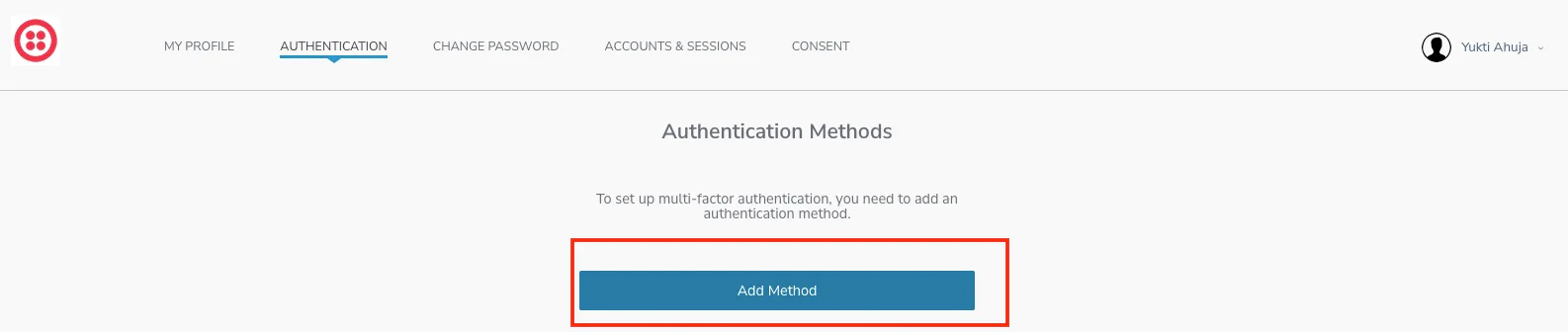

2. Choose your preferred channel Text Message (SMS) or Voice
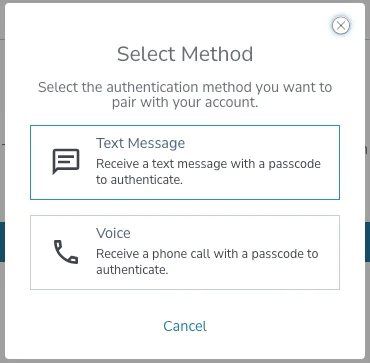

3. For this demo, we selected Text Message
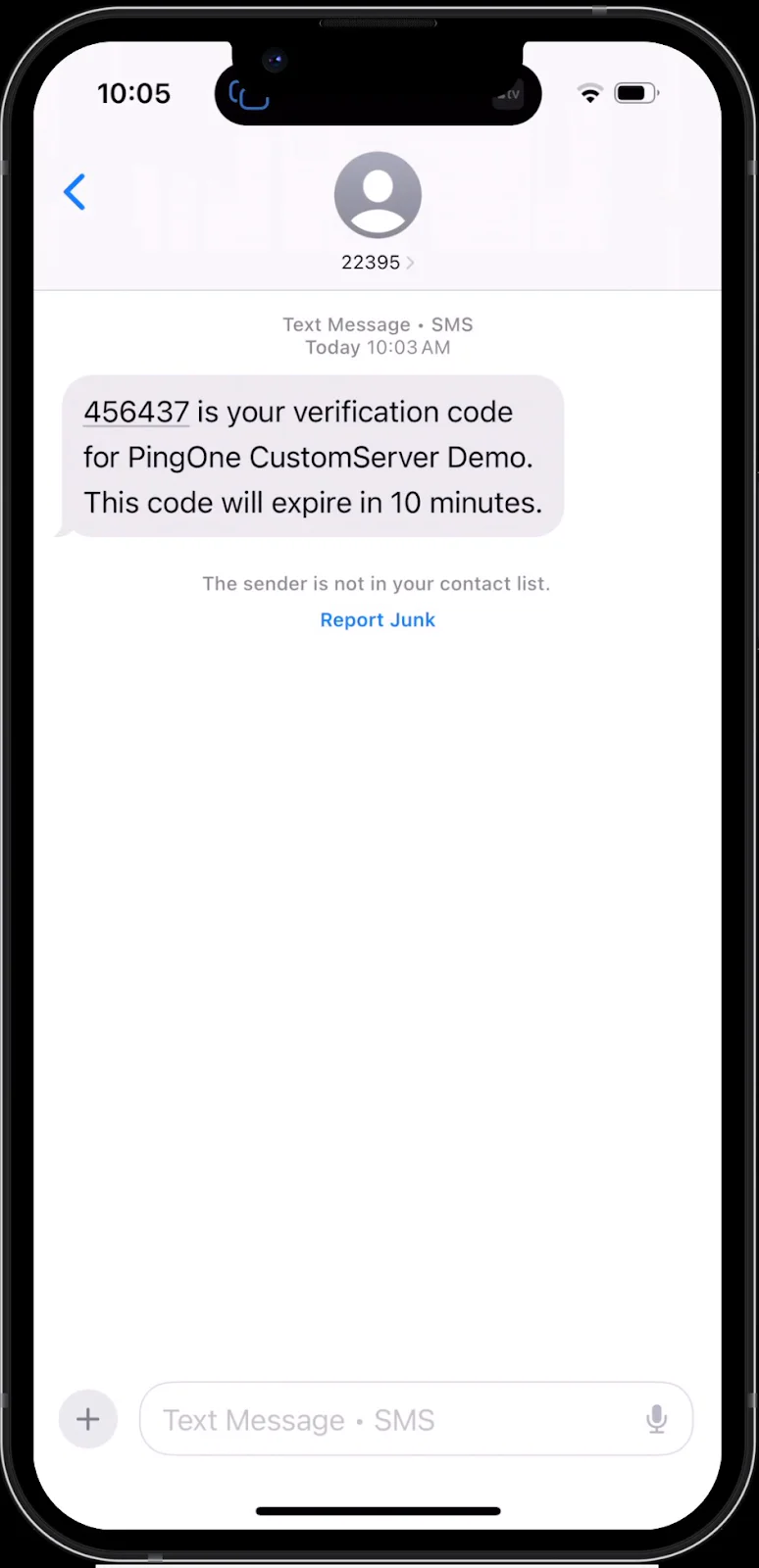
4. You should receive an SMS based on your configured PingOne notification template
5. Plug in the OTP code in the MFA setup screen
6. MFA will now be set up for this user

6. Log in again with MFA
1. Go back to http://localhost:3000
2. Log in again with the same email and phone number
3. Now you’ll see the MFA prompt to request an OTP from your profile
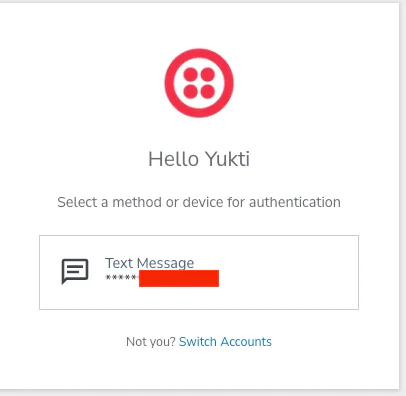

4. Click on Text Message and you will receive a new OTP based on the selected PingOne template.
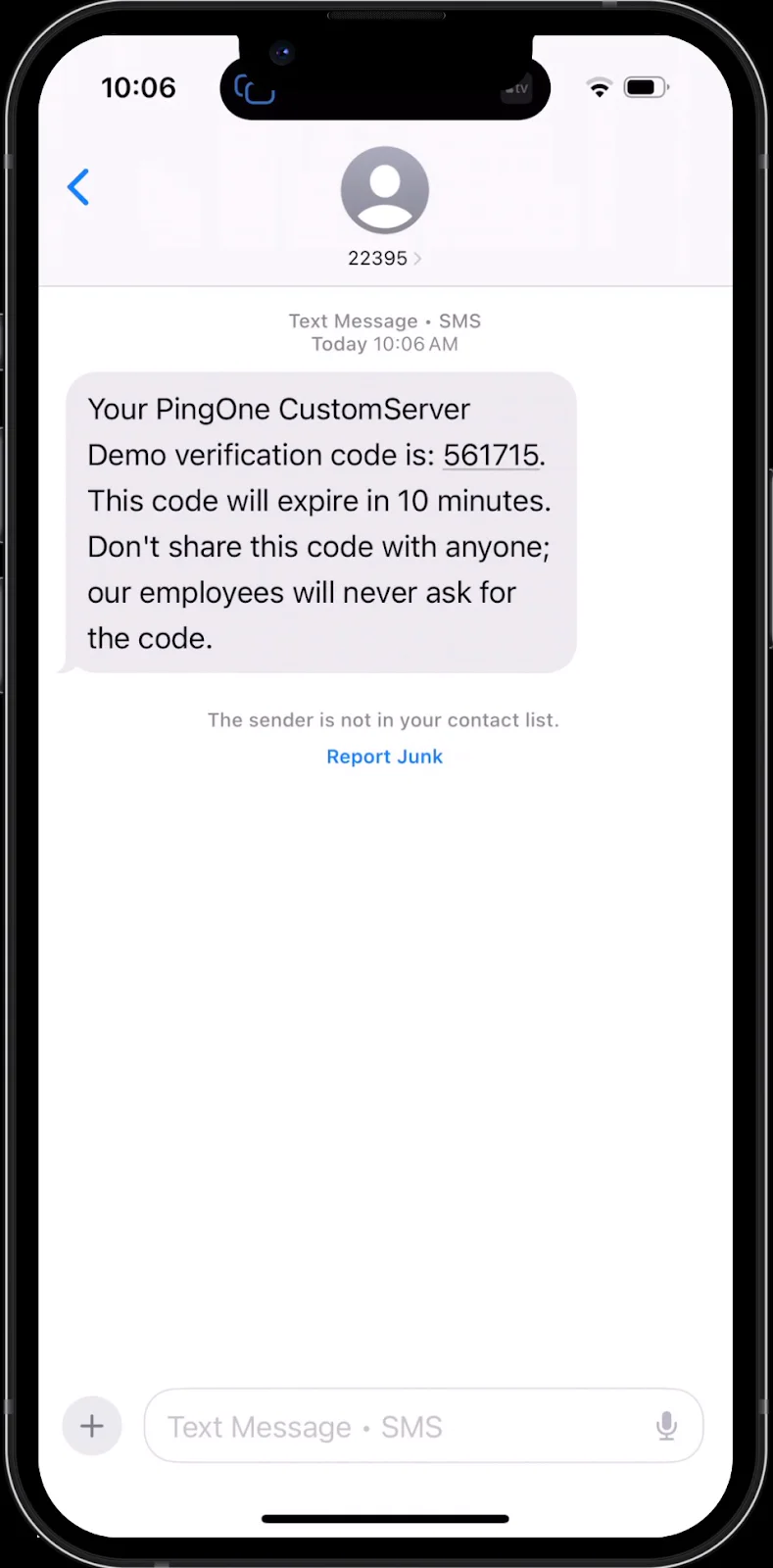

5. Once verified, you will be successfully logged in to the application using Twilio and PingOne!

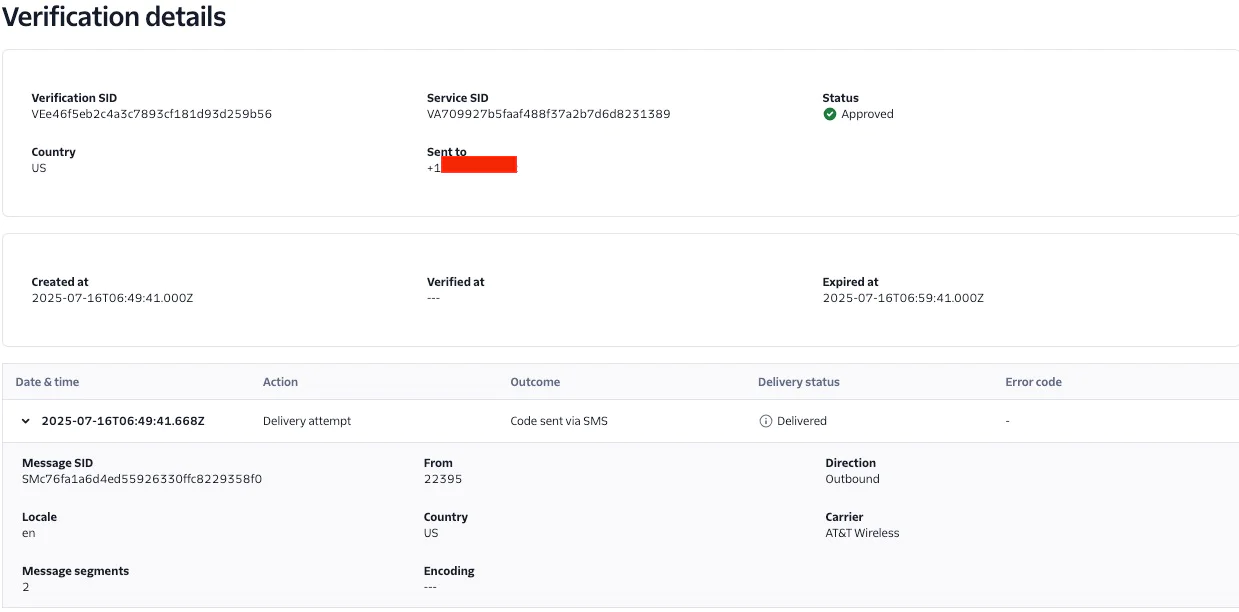
7. View OTP Delivery Status in your Twilio Console
Once the OTP is sent, you can confirm that the request was successful in the Twilio Console.
- Log in to your Twilio Console
- Navigate to Monitor > Logs > Verify
- Click on a verification attempt
- The status should show as approved once the user enters the correct OTP

Delivering OTPs with Twilio Verify in PingOne
Your users can now log in securely using multi-factor authentication, with one-time passwords sent via Twilio Verify. Want to explore more about what Twilio Verify can do? Check out Twilio Verify API documentation. We can't wait to see what you build and secure!
Yukti Ahuja is a Principal Solutions Engineer at Twilio. As an SE, she is a problem solving extraordinaire, blending technical expertise to bridge the gap between complex technology and practical solutions for customers. You can reach her at yahuja [at] twilio.com .
Itai Zach is a Staff Product Manager at Twilio, with deep expertise in Identity and Access Management. Recognized as an SME in MFA, Risk, and Passwordless, his record showcases strong capabilities in strategic planning, new product development, and client engagement across his 20 years career in the software industry.
Related Posts
Related Resources
Twilio Docs
From APIs to SDKs to sample apps
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars
Learn from customer engagement experts to improve your own communication.
Ahoy
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.


