Integrate Twilio Verify Service with RSA SecurID
Time to read:
Many organisations in the banking sector are still using RSA SecurID with hardware tokens for multi factor authentication (MFA). However, employees might forget their hardware token thus won’t be able to login. This leads to high support costs, poor user experience and reduced productivity. This is the exact challenge that one of our customers in banking is trying to address. So we worked together to explore how Twilio Verify Service can be leveraged as an alternative MFA. This will allow their employees to login their protected systems by using a One-Time Password (OTP) delivered to their employee’s mobile phone.
This blog post will walk you through the steps of how to integrate Twilio Verify service with RSA SecurID.
How does Twilio Verify work with RSA SecurID?
We use Twilio Functions as a proxy between RSA Authentication Manager and Twilio Verify service because RSA Authentication Manager’s HTTP-Plugin does not support HTTP(s) basic authentication, while Twilio Verify REST API requires basic authentication.
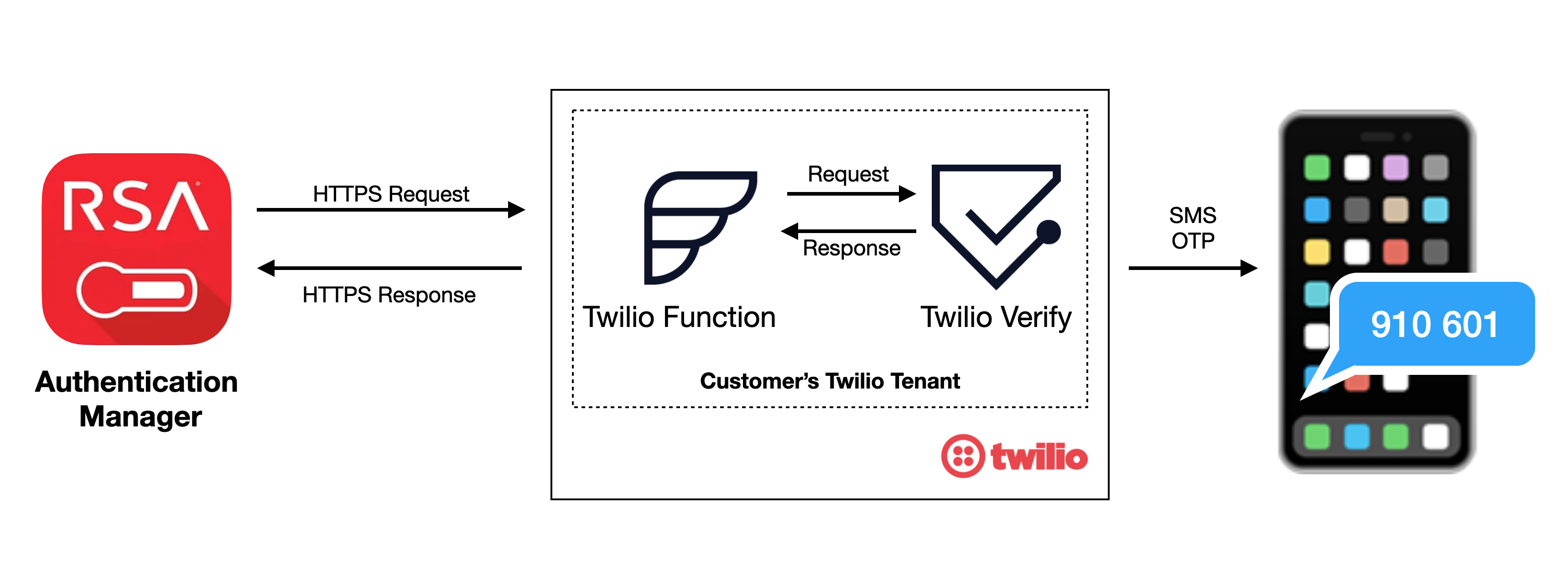
What you will need to code along with this post:
- Twilio Account
- Twilio Verify service that you will create in Twilio Console
- Twilio Function that you will create in Twilio Console
- RSA SecurID and Administrator access to RSA Authentication Manager
Login to the Twilio Console either as an account owner or an account administrator. You can create a Twilio account for free.
Setting up the Twilio Verify Service
Go to Verify in the console and create a new Verify service.


In this example, we name the service as “RSA Verify Integration”. Enable the custom code feature and note down the Service SID value (VAXXX…).


Setting up the Twilio Function
Go to Twilio Functions and click the Create Service button.
Click the blue "Add" button and select "Add Function". Make the function URL a long random string to help obfuscate the URL. Change the function to "public" which allows applications other than Twilio to make requests to your function.
Next, copy the code from my GitHub project and replace everything in the CODE area.
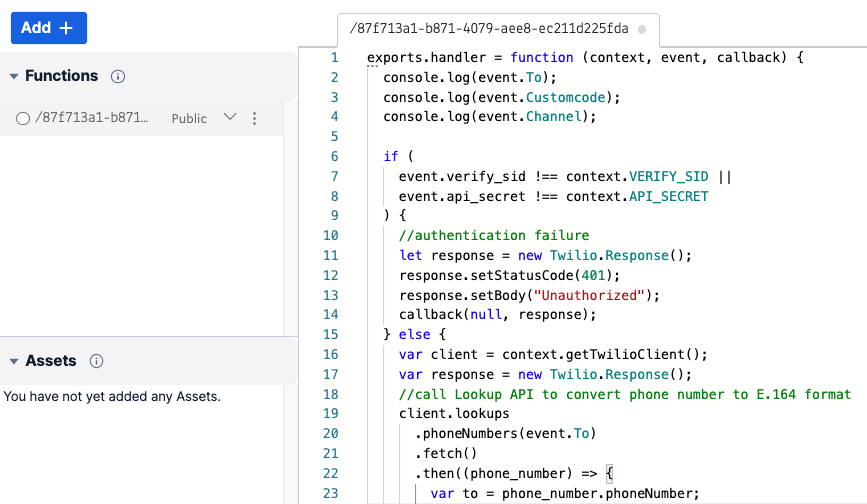
The function will take two parameters as input: the Verify Service SID (verify_sid) and a shared secret (api_secret), which is a long random password shared between the function and RSA security manager. Parameters are passed in via HTTPS POST in the request body.
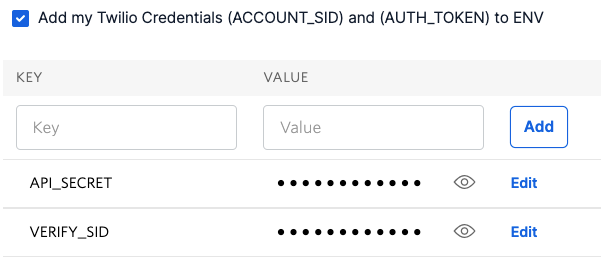
Next, we need to setup two environment variables and also update dependencies. Click "Environment Variables" above the "Deploy All" button.
Make sure the "Add my Twilio Credentials" checkbox is selected. Add a new variable name called API_SECRET. Please generate a long complex password for the Value of API_SECRET.
To prevent fraud on your account, please use strong complex password for API_SECRET and keep it safe. This is the shared secret between your RSA Authentication Manager and your Twilio function.
Repeat the process to create another environment variable called VERIFY_SID and update the value with the value of your Verify Service SID (VAXXX…) that you created in the previous step.
Last, update Twilio version under the Dependencies to 3.36.0 or higher. Click Save and Deploy All to save the changes you made.
Everything in Twilio is now setup, let us head over to RSA Authentication Manager.
Configuring RSA Authentication Manager
RSA authentication manager comes with a HTTP plug-in. For general information about how to configure HTTP Plug-in for SMS token delivery, please check RSA online documents here and also here.
Go to SMS configuration tab on the On-Demand Tokencode Delivery page as shown below.
Under Tokencode Delivery by SMS section
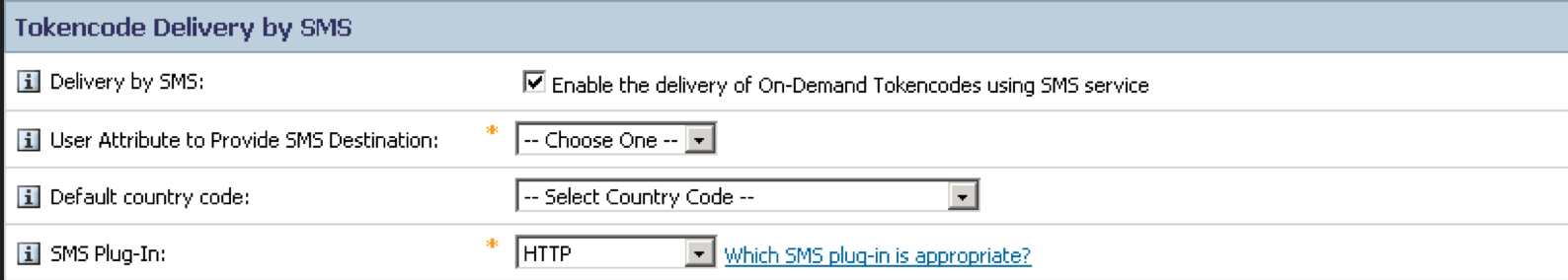
- Tick the Enable the delivery of On-Demand Tokencodes using SMS service checkbox
- Select user’s mobile number attribute from the dropdown menu of User Attribute to Provide SMS Destination. This is the mobile number to which the SMS OTP will be sent.
- Select the Default country code from the drop-down menu (Optional)
- Select HTTP from the SMS plug-in drop-down menu
Under SMS Provider Configuration section:
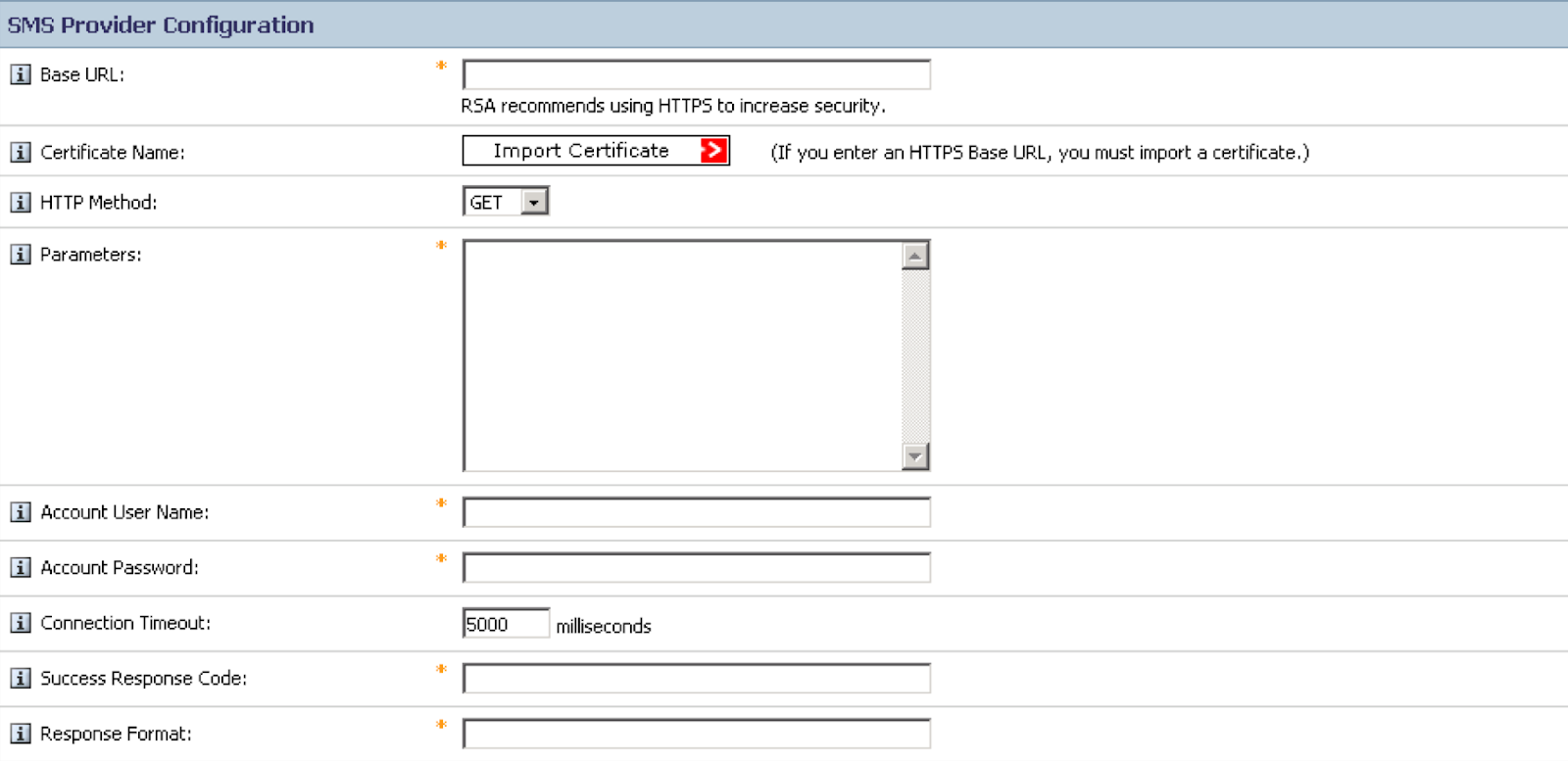
Copy the full path of your RSA Verify Twilio Function (https://xxx-xxx.twil.io/YOUR_LONG_RANDOM_STRING) to the Base URL field
Download the certificate (see note below) from your Twilio function, use the full URL of your function without the path (https://xxx-xxx.twil.io/) and import the certificate by clicking Import Certificate.
You can either import the root certificate, the intermediate certificate or Twilio Function certificate. To minimise possible interruption to your service due to expiration of the pinned certificate, you might consider to import the root certificate.
Next, select POST from the HTTP Method drop-down menu and copy the following string into the Parameters field
To=$msg.address&Customcode=$OTT&Channel=sms&verify_sid=$cfg.user&api_secret=$cfg.passwordThen:
- Enter the Service SID value (
VAXXX…) for Account User Name - Enter the value of API_SECRET for Account Password
- Copy the word
pendinginto the Success Response Code field - Copy the following line into the Response Format field (note there is a leading period)
.*status":\s?"([a-zA-Z]*)Please also configure SMS HTTP Proxy Configuration if HTTP proxy is used. Please speak to your network administrator for proxy detail. Leave it empty if HTTP proxy is not used in your network.
Do not forget to Click Update to save the SMS configuration.
To test your configuration, under Test SMS Provider Integration:
- In the Mobile phone number to test fields, select a country code, and enter the number for a mobile phone that receives the test message and the OTP.
- Click Send Test Text Message.
The system saves all of your changes before the test is conducted. If the connection is unsuccessful, you see an error message.
Updating Certificate
If you are using Twilio Functions with your RSA Authentication manager, you will need to update the RSA Authentication manager when we update our certificates. You can see how to monitor Twilio's security updates in this post.
Using Twilio Verify and RSA SecurID together
As you can see from this example, the Twilio Verify service is very straightforward to use. Twilio Functions offer a lot of flexibility. It glues the two services (RSA Authentication Manager and Twilio Verify service) with just a few lines of codes so the services can interact with each other. If you have any questions, please leave a comment below or reach me on my GitHub.
Dr Mingchao Ma has more than 15 years’ experience in Cybersecurity. In the account security team at Twilio he helps customers build solutions using Twilio Cloud security APIs. He previously worked at Microsoft UK helping financial sector customers adopt Microsoft Cloud security technologies. Before this he was a lead security architect at IBM UK. Mingchao has a PhD in information security, and cybersecurity certifications such as CISSP-ISSAP, CISM, SABSA etc. He is a Microsoft Certified Azure Solutions Architect Expert, Microsoft 365 Certified Enterprise Administrator Expert and Microsoft Certified Azure DevOps Engineer Expert.
Related Posts
Related Resources
Twilio Docs
From APIs to SDKs to sample apps
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars
Learn from customer engagement experts to improve your own communication.
Ahoy
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.


