Google Authenticator app support now available in Authy API
Time to read:
This post is part of Twilio’s archive and may contain outdated information. We’re always building something new, so be sure to check out our latest posts for the most up-to-date insights.

Twilio’s market leading two-factor authentication API, Authy, has added support for Google Authenticator and other TOTP-standard apps. This new API update gives customers of our API the ability to accept tokens generated from Authy or any other TOTP compliant application. The enhancement increases the broad scope of options the API currently gives to your end users and allows your developers to continue to rely on the Twilio 2FA API, reducing effort to implement and maintain your 2FA solution.
When a user account is protected with 2FA, the most common method is the entry of a one time passcode (OTP) after they’ve first provided a valid username and password. The user gets the OTP either via SMS, a voice call, or (the most secure option) from a mobile or desktop app. When an app is involved, the passcode is generated using time as a reference, and therefore the method is called Time based One Time Passcodes, or TOTP.
The Authy API has always supported the free Authy app, but this required some users to manage tokens for different websites across multiple different apps. Having to download and install yet another mobile app can be frustrating for users, especially when they have one that works already. That’s why we’ve decided to update our API and allow you to further reduce the friction for users opting in for 2FA.
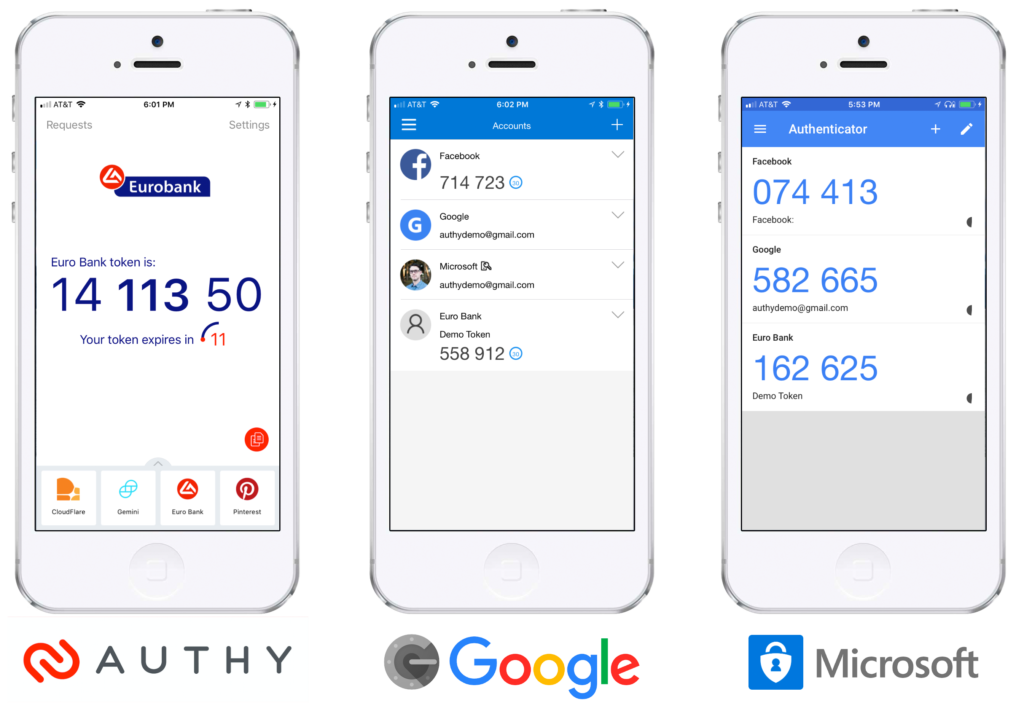
Implementing this new feature is easy. In the UI where you ask the user to enable 2FA, you can now offer Authy and Google Authenticator (or any authenticator) options. The advantages of using Authy app are that it supports push authentication, gives users control over the security of their 2FA account, and provides a secure self service path to recovery if a user changes their phone number or loses their device. If the user selects Google Authenticator, the steps are simple.
- Ask the user for their phone number. This is still required because it’s part of the secure mechanism by which we can help users recover access to accounts. It also allows users to fall back to SMS/voice calls when needed.
- Add the user to the Authy API. The API will return an authyid which you must save in your application for future authentications.
- Call the Authy API to generate a QRCode which you present to the user. We generate a PNG and give you a public URL to it, super easy! They can then scan this code into their Google Authenticator or other compatible application. Before you confirm the 2FA enablement, it’s recommended that you ask for the code to ensure the user has successfully scanned it. (Next step)
- The user’s 2FA app of choice will now start generating the 2FA codes. When they enter these codes them into your application (and as mentioned above, always do this during 2FA enablement) pass the code to the Authy API to verify it.
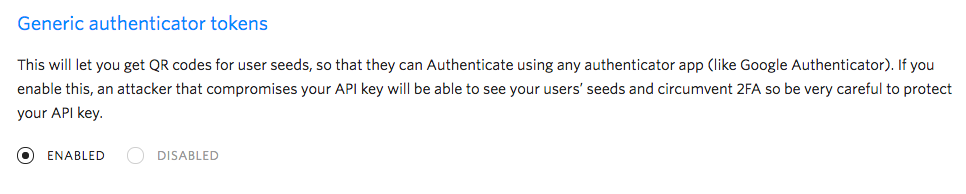
To enable this feature, you have to switch it on in the console. Simply login to twilio.com/console, then navigate to Authy -> Select your application -> Settings. At the very bottom you can switch on this new feature.
Of course, we still recommend using an Authy app over something like Google Authenticator. Working on iOS, Android, Windows, and MacOS — and also supporting the latest in push authentication — Authy has the ability to backup the tokens and, when combined with the Authy API, vastly improves the user’s 2FA experience. Using the Authy app also allows application owners to make much more secure decisions around the authentication experience, which works to improve the security of all user accounts.
Have you implemented the Authy API, but want total control over the application authentication experience? We recommend using the Authy SDK which allows you to embed TOTP and push authentication features directly in your application, just as Namecheap and Transferwise have chosen to do.
If you are a customer of the Authy API, and have had users asking to use something other than the Authy app for their TOTP tokens, head over to our documentation and get started. If you are thinking about increasing the account security for your users, then head over to our docs for best practice advice and detailed guides.
Related Posts
Related Resources
Twilio Docs
From APIs to SDKs to sample apps
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars
Learn from customer engagement experts to improve your own communication.
Ahoy
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.