Voice Calls 101: CNAM, STIR/SHAKEN, and Voice Integrity Explained
Time to read:
Voice Calls 101: CNAM, STIR/SHAKEN, and Voice Integrity Explained
Voice call technology has evolved significantly over the last decade, but not all of that advancement has been used for good. Scammers and fraudsters use robocalls— sometimes with a spoofed caller ID to make you think the call is from a trusted party—to target unsuspecting victims. Their goal may be to extract sensitive information for identity theft or trick the target into handing over money or financial information.
Malicious actors have eroded trust in the PSTN (public switched telephone network), which has affected legitimate businesses that are trying to reach their current and potential customers through voice calls. Several tools and services have been put in place to rebuild the trust and reliability of voice calls:
- CNAM allows you to brand landline calls with a business name in the Caller ID field
- STIR/SHAKEN to verify the authenticity of the calls you place
- Twilio’s Voice Integrity to ensure your legitimate calls are not mislabeled as spam
In this post, we’ll dive into these key tools, looking at how businesses using Twilio Voice can use them to build trust with their customers.
CNAM: branding your calls
CNAM is short for caller ID name. It’s a feature that allows businesses to display their name on the recipient’s caller ID. Before we dive into the details, let’s review caller ID numbers.
The origin of caller ID numbers
Caller ID is a technology that’s been around since the 1990s. When you receive a call, your phone displays the phone number of the caller. With this additional information about the caller, you can decide whether or not to answer the call. Of course, the effectiveness of caller ID depends on your ability to recognize the phone number as familiar or—at the very least—local.
Soon after caller ID became ubiquitous, phones provided a feature where you could save a custom name for a caller ID number. When any subsequent calls with that caller ID number arrived, your phone would display the custom name.
The limitations of caller ID numbers today
Back in the early days of caller ID, your landline phone number was local and naturally tied to your geographic location. Even as you purchased cell phone service, the phone number you received was generally a local one. As a call recipient, if your phone displayed a local caller ID number, you had high confidence that the call was from a person or business in the area.
Today, mobile and VoIP service providers make it possible to activate a phone number in any region of the United States or nearly any country of the world. But if you and your business can do this, then so can scammers. This means that even if you see a local number show up on your caller ID screen, the call could still be coming from a call center halfway around the world.
What does this mean for your business? Imagine calling your customer who lives down the street. They see a local caller ID number, but they don’t recognize it. To them, you’re probably a scammer calling from the other side of the ocean. They won’t pick up.
The benefits of CNAM
By displaying your business name—not just an unfamiliar number—on the recipient’s caller ID, you enhance brand recognition and call acceptance rates. Imagine if your patient sees Valley ENT instead of +1 (415) 123-4567 on their caller ID. They may not recognize the number, but they will recognize your business name. By using CNAM to establish a trusted connection with their customers, businesses improve customer engagement.
Businesses that use Twilio Voice can set up CNAM for free. After you have activated a phone number in your Twilio account, you can follow the straightforward CNAM onboarding process.
How to get started with CNAM through Twilio
The steps for CNAM onboarding through the Twilio Console are as follows:
1. Create a Primary Business Profile in the Trust Hub.


2. After your Business Profile has been reviewed and approved, assign phone numbers in your account to the Business Profile.
3. Create a CNAM Trust Product instance.
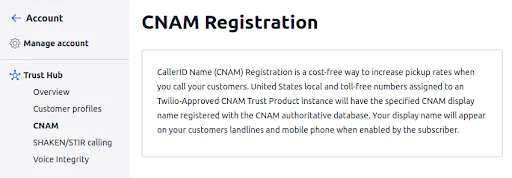

4. Select phone numbers from your Business Profile for CNAM registration.
After your CNAM Trust Product instance is approved, Twilio will register the CNAM display name for your numbers with the CNAM authoritative database in the United States.
As an alternative to working within the no-code Twilio Console, you can onboard programmatically through the Trust Hub REST API.
Key points to note
As you set up and use CNAM, take note of the following restrictions on the CNAM display name:
- Can be a maximum of 15 characters
- Must be a unique name or value, cannot be a generic value such as a city/state
- Should begin with a letter and can only contain letters, numbers, periods, commas, and spaces
- If no caller name (CNAM) is set for the number, the city and state of the number is the default display along with the phone number.
Also, note these additional restrictions:
- To use CNAM with toll-free numbers, you need to contact Twilio Support directly. This can’t be done through the standard onboarding process described above.
- Only Twilio phone numbers from the United States fully support CNAM lookups.
- After your CNAM Trust Product has been approved, the display name may take 48-72 hours to propagate to all carriers in the United States.
For more detailed information, please refer to Brand Your Calls Using CNAM.
STIR/SHAKEN: combating caller ID spoofing
STIR/SHAKEN is a technology that targets caller ID spoofing by adding an authentication layer to the telephony network. STIR/SHAKEN comes out of two acronyms:
- Secure Handling of Asserted information using toKENs
- Secure Telephony Identity Revisited
The perpetrators behind robocalls combine auto-dialing tools, pre-recorded messages, and caller ID spoofing. Caller ID spoofing in particular has presented a challenge to targeted, vulnerable populations. Without the ability to reliably detect robocalls, targeted individuals are still exploited. And for your business, this means recipients have low confidence that seeing your caller ID number on their phone actually means it’s you calling them.
How STIR/SHAKEN works
STIR/SHAKEN helps call providers verify the authenticity of the call being placed by using encrypted digital signatures. Here is a list of steps that take place when a call is made:
- The STIR system adds information, including caller ID, to the Session Initiation Protocol (SIP) header. The SIP header is attached to the VoIP call data that traverses the various network endpoints between the originating provider and the terminating provider.
- As the originating provider attests to the identity of the caller, it uses public key encryption to sign a JSON web token (JWT) and attach this data to the SIP header.
- At each point along the network, a provider can verify the signature of the token for authenticity and then examine the data in the SIP header, deciding whether to continue routing the call or reject it.
- SHAKEN is an additional mechanism that specifies how to verify a calling number through this SIP data and how to transport that data between VoIP networks and original (non-internet-based) telephone networks.
When attaching caller ID information to the SIP header, the originating provider can select one of three levels of attestation:
- A (full attestation): The originating service provider recognizes the phone number as being registered with the originating subscriber. The provider attests that the caller is known and has the right to use the phone number as the caller ID.
- B (partial attestation): Although the customer is known, the number used as the caller ID cannot be verified. It is unknown if the caller has the right to use this caller ID.
- C (gateway attestation): The call can only be verified as coming from a known gateway. It doesn't meet the requirements of A or B.
For a more detailed look at the technical aspects of STIR/SHAKEN, read Everything You Need to Know About STIR/SHAKEN Right Now.
What this means for businesses
For your registered and legitimate business, verifying your ownership of your phone numbers ensures that call providers can authenticate the calls that you make. You can ensure that customers will recognize your calls as legitimate rather than fraudulent by being part of the chain of trust
How to get started with STIR/SHAKEN through Twilio
Twilio, like all major phone carriers in the United States, has signing and verifying privileges for call origination and termination. If your business buys phone numbers from Twilio, then attaching those numbers to your approved Business Profile ensures outbound calls from those numbers will have STIR/SHAKEN A-level attestation.
On select smartphones, recipients will even see “Caller Verified” on incoming calls. If you have bought your phone number from a different provider, then you can port that number to Twilio before attaching it to your Business Profile.
For more detailed information, you can refer to Twilio's page on STIR/SHAKE.
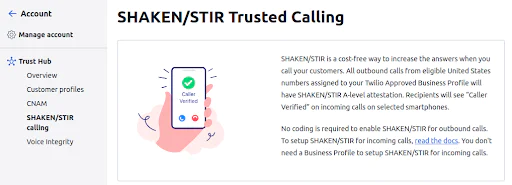

Twilio's implementation of STIR/SHAKEN illustrates its commitment to secure and reliable communication. By integrating these standards, Twilio helps to thwart the efforts of malicious actors who rely on spoofed numbers. This not only aids in curbing unwanted and potentially harmful calls but also restores public trust in phone communications.
Voice Integrity: ensuring call authenticity
As part of the effort to combat robocalls and caller ID issues, some call providers and smartphone manufacturers are using analytics engines and number reputation checks to label phone numbers as spam or not. While this is generally a good thing, it has also led to reduced call acceptance and increased call blocking of legitimate calls.
Voice Integrity from Twilio helps you remediate spam labels on your phone numbers and monitor phone number reputation. After you’ve attached your Twilio phone numbers to your approved Business Profile in the Twilio Trust Hub, Twilio will register these numbers with analytic engines for T-Mobile, Spring, AT&T, and (coming soon) Verizon Wireless.
By using Voice Integrity, your business can ensure that its calls are correctly identified and not mistakenly marked as spam. You can preserve the reputation of your business numbers and ensure that your phone communication reaches your customers.
How to get started with Voice Integrity through Twilio
Onboarding with Voice Integrity is simple and straightforward, especially if you’re a direct customer with no subaccounts:
- Create a Primary Business Profile in the Trust Hub.
- After your Business Profile has been reviewed and approved, assign phone numbers in your account to the Business Profile.
- Create a Voice Integrity Trust Product.
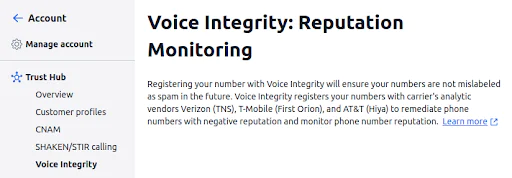

After your Voice Integrity Trust Product has been approved, select phone numbers from your Business Profile for use with Voice Integrity.
If you are a direct customer with subaccounts, then you will need to create a Secondary Business Profile for each subaccount, assigning phone numbers from the subaccount to the Secondary Business Profile. ISVs and resellers follow a similar onboarding process, creating Secondary Business Profiles either under their parent account or under customer subaccounts, as appropriate.
Partnering with Twilio for voice call quality and reliability
In this post, we've explored three key tools that businesses are using to build trust with their customers and improve call acceptance rates. In an era where your customers are flooded with robocalls and spoofed caller ID numbers, it’s essential for your business to verify your caller identity, brand your call, and ensure your call is not listed as spam.
Twilio Voice offers these critical tools and services to its business customers. Leveraging CNAM, STIR/SHAKEN, and Twilio’s Voice Integrity to get the most out of your business phone numbers is quick and easy.
Related Posts
Related Resources
Twilio Docs
From APIs to SDKs to sample apps
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars
Learn from customer engagement experts to improve your own communication.
Ahoy
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.