How to Use the Agent-to-Human Communication (A2H) Protocol with OpenClaw
Time to read:
OpenClaw is one of the most ambitious autonomous agent projects today, a personal AI assistant that connects to WhatsApp, Telegram, Discord, and 15+ other channels, with the ability to execute shell commands, manage files, and interact with the world on your behalf.
It's also a case study in why A2H, the Agent-to-Human Communications Protocol, matters.
The problem: Autonomy without accountability
OpenClaw users on Hacker News reported experiences like:
- "I woke up in the morning and it had been replying to ANY and ALL of my iMessages." ( 1 )
- "Without sandboxing, this thing could probably ruin your life." ( 2 )
- "The security story is basically 'hope for the best.'" ( 3 )
- "It hallucinated... Everything needs review." ( 4 )
These aren't criticisms of OpenClaw specifically – they're symptoms of a missing layer in the autonomous agent stack. When agents can act without gates, without proof, and without audit trails, users are left choosing between capability and control.
What OpenClaw has today
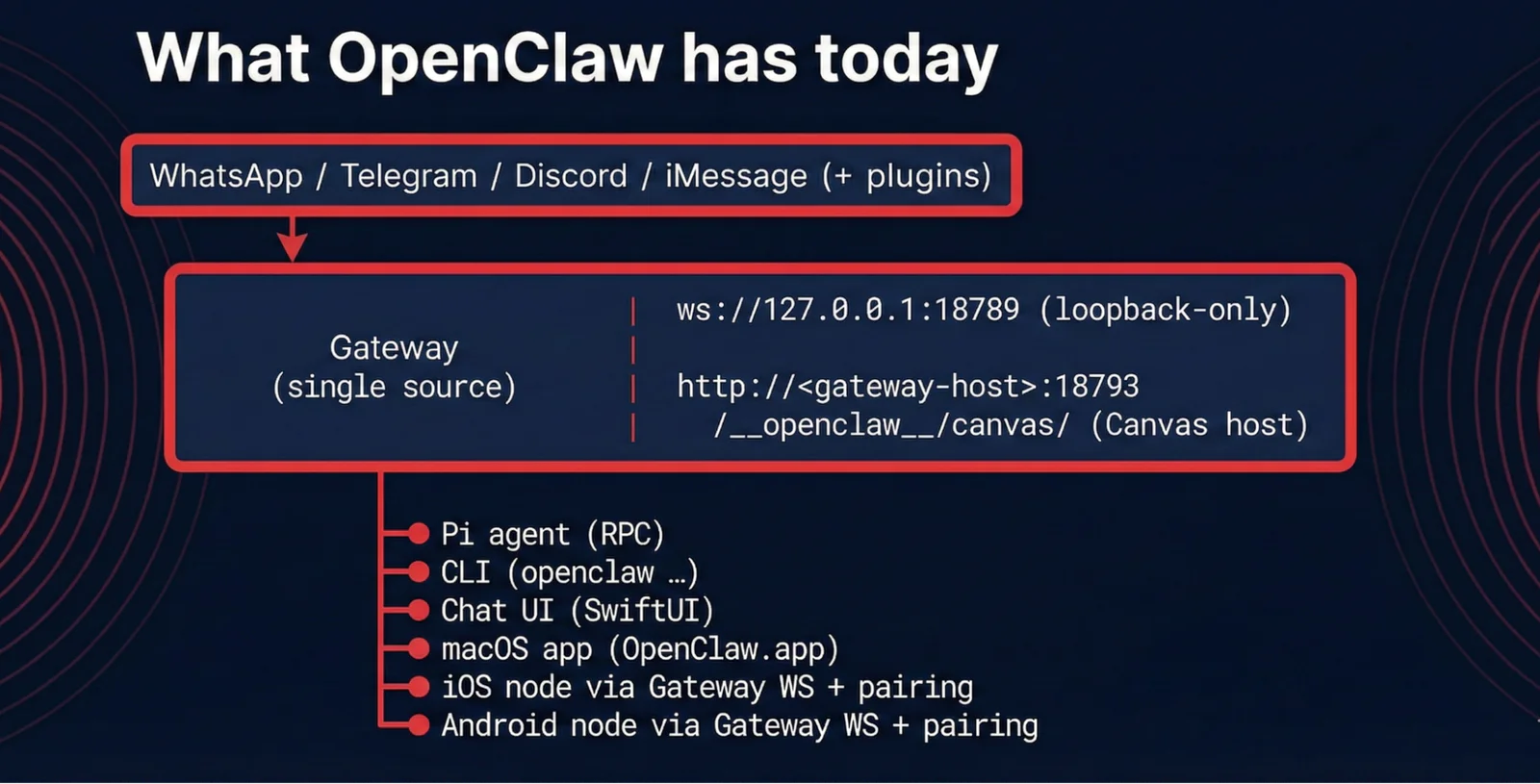

OpenClaw does have a security model: sandboxing, allowlists, DM pairing codes, and approval gates via CLI. Here's a typical exec tool config:
When a command isn't in the allowlist, OpenClaw prompts for approval in the same channel. The openclaw approvals CLI manages pending requests, and openclaw security audit --deep can harden the configuration automatically.
This is real access control, but there's a gap between approval and attestation:
| What Exists | What's Missing |
|---|---|
| Allowlists + sandbox | Cryptographic evidence of approval |
| Same-channel prompts | Out-of-band escalation for high-risk ops |
| approval-pending status | Signed proof for audit trails |
| Security audit CLI | Third-party attestation |
What A2H adds
A2H bridges the gap from "approval" to "consent with evidence":
Now when your agent wants to run rm -rf /var/backups/*:
- The agent pauses and sends an
AUTHORIZErequest to A2H - You receive an out-of-band notification (SMS, push) even if you're not watching the chat
- You authenticate with Face ID or Touch ID (not just typing "yes")
- The agent receives JWS-signed evidence and proceeds
- The evidence is attached to the audit log – cryptographic proof you approved
Try the OpenClaw integration example yourself:
OpenClaw's channels are excellent at delivery. A2H adds the trust layer: proof that a human approved, proof of what they approved, and proof of when they approved it.
For users who are "too afraid to try" autonomous agents, A2H provides the safety net. For users who are already running OpenClaw, A2H provides the audit trail they'll wish they had when something goes wrong.
We're excited to work with the OpenClaw community to make autonomous agents both powerful and trustworthy.
Additional resources
- Learn more about the Agent to Human Protocol
- A2H Protocol Specification
- A2A Protocol (Agent-to-Agent)
- Model Context Protocol (MCP)
- Twilio Verify
- Latency Extension for A2A
Rikki Singh is a product and engineering leader based in Bay Area, California. At Twilio, she leads the Emerging Technology and Innovation group Twilio Forward. Outside of work, Rikki enjoys hiking and camping with her husband and toddler.
Ryan Ferguson is a Senior software engineer manager based in Boulder, Colorado. At Twilio, he helps lead engineering initiatives on the Emerging Technology and Innovation team, Twilio Forward. Outside of work, Ryan enjoys running ultra marathons.
Related Posts
Related Resources
Twilio Docs
From APIs to SDKs to sample apps
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars
Learn from customer engagement experts to improve your own communication.
Ahoy
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.