Improving user privacy for two-factor authentication
Time to read:
While it is generally agreed that two-factor authentication (2FA) is an increasingly important means of adding security to your user accounts, you’ve probably heard of stories where the phone number used to enable 2FA ended up part of a data breach or was misused by the website. This has led to an unwillingness with some people to provide their phone number.
To address this, we updated Twilio’s Authy API to allow 2FA to be implemented on websites without having to collect the phone number from the user.
Why Authy asks for the phone number
Before we look at the new change, it’s worth understanding how Authy was designed to use your phone number. There are two elements to the Authy solution, the API which businesses use to integrate 2FA into their applications, and the Authy app which consumers use to generate 2FA codes. The phone number ties the two together, allowing for the following benefits;
- When enabling 2FA on a website, a user provides just a phone number and the 2FA tokens are automatically delivered to the app.
- If the user loses their phone, they can easily recover access to their 2FA codes by re-installing the Authy app which authenticates them using their phone number.
How this new method works
Instead of asking for the phone number when the user wants to enable 2FA, the Authy API now allows the website to show the user a QR code which contains data unique to the user, but is not personally identifiable. End users must first install the Authy app, which is then used to scan the code. The Authy app then communicates with the API to say that the user has enabled 2FA. The website then either polls the API for the update, or the update is received via a webhook. Instead of getting the users phone number, the website gets an authyid, which is an identifier tied to the user's Authy account but that represents no personal information. Note that this new method also removes not just a phone number, but also email address as a requirement to 2FA enablement.
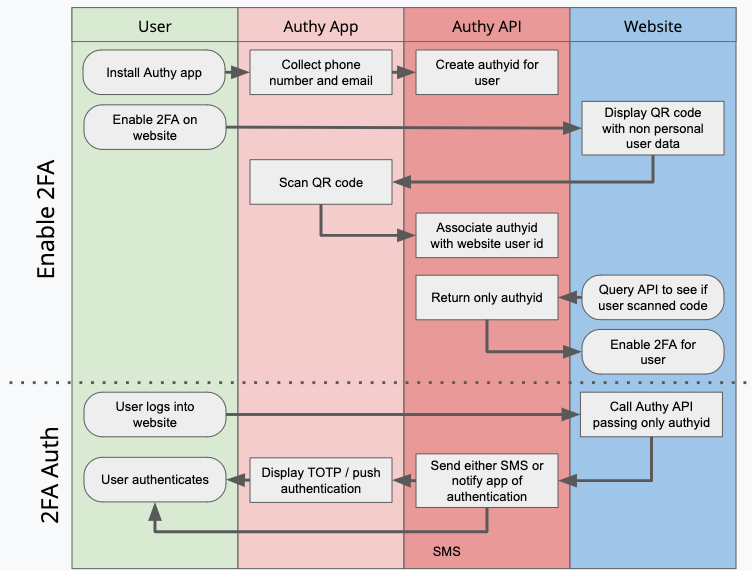
The Authy app knows the users phone number because that’s how it was installed and authenticated. But that information isn’t shared with the website where 2FA is being enabled.
Now when the website wishes to perform the 2FA step, it calls the API, passing in the authyid. Depending on the method of 2FA, the user either gets an SMS message with the login code, uses the Authy app to generate a soft token or they get a push authentication. All these methods work as normal, the only difference is the website the user is authenticating with either didn’t collect the phone number, or if it did, didn’t share it with the Authy API.
But hold on, isn’t the user just sharing their phone and email with Authy anyway?
The Authy app still requires you verify your phone number at installation. This is an important part of why Authy is the number one 2FA authenticator app, it allows you to use multiple devices for 2FA and also recover access if you lose a device. The key point with this change is that websites which enable 2FA with our API don’t need to know your phone number anymore.
An interesting side effect is that you can now enable 2FA on a website, not have to tell them your phone number, but still be able to get 2FA codes via a text message.
Increased privacy for 2FA
This change is now available for developers to implement. Head over to the docs and update your 2FA enablement flow. For the best 2FA experience, we recommend implementing push authentication too (docs here).
Related Posts
Related Resources
Twilio Docs
From APIs to SDKs to sample apps
API reference documentation, SDKs, helper libraries, quickstarts, and tutorials for your language and platform.
Resource Center
The latest ebooks, industry reports, and webinars
Learn from customer engagement experts to improve your own communication.
Ahoy
Twilio's developer community hub
Best practices, code samples, and inspiration to build communications and digital engagement experiences.